The 802.1x implementation – Allied Telesis AlliedWare Plus Operating System Version 5.4.4C (x310-26FT,x310-26FP,x310-50FT,x310-50FP) User Manual
Page 1064
802.1X Introduction and Configuration
Software Reference for x310 Series Switches
40.6
AlliedWare Plus
TM
Operating System - Version 5.4.4C
C613-50046-01 REV A
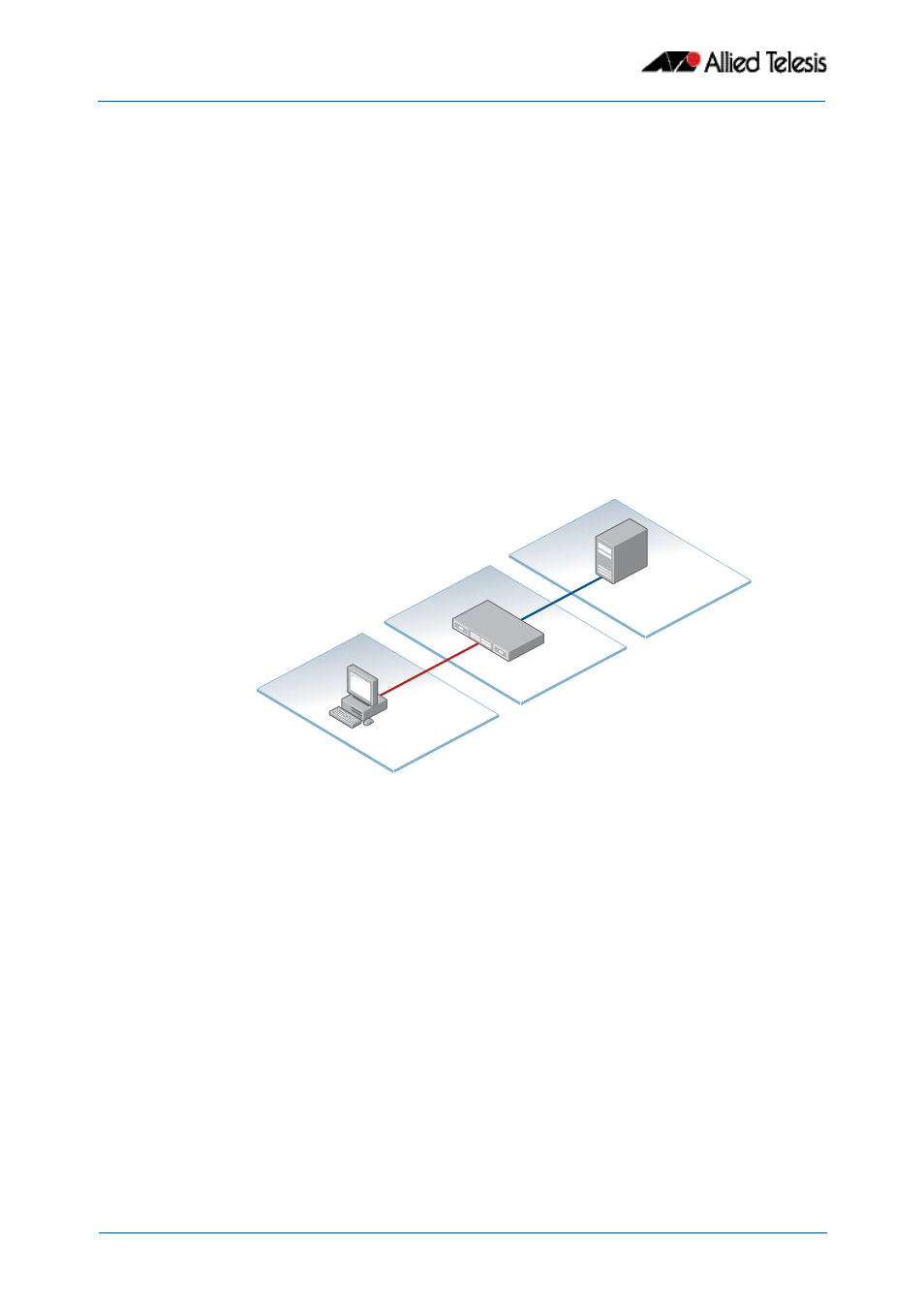
The 802.1X Implementation
802.1X port access control is achieved by making devices attached to a controlled port
authenticate themselves via communication with an authentication server before these
devices are allowed to access the network behind the controlled port.
Authentication is required on a per-port basis. The main components of an 802.1X
implementation are:
■
the authenticator - the port on this device that wishes to enforce authentication
before allowing access to services that are accessible behind it.
■
the supplicant - the port that wishes to access services offered by the authenticator’s
system. The supplicant may be a port on a PC or other device connected to this
device.
■
the authentication server - a device that uses the authentication credentials supplied
by the supplicant, via the authenticator, to determine if the authenticator should
grant access to its services.
To configure the switch operating as authenticator, follow the instructions below:
1. Configure a RADIUS server for the switch to send requests to
2. Instruct 802.1X to use the configured RADIUS server
3. Configure port1.0.5 for 802.1X authentication
awplus(config)#
radius-server host 192.168.1.250 key
<secret-key>
awplus(config)#
aaa authentication dot1x default group radius
awplus(config)#
interface port1.0.5
awplus(config-if)#
dot1x port-control auto
awplus(config-if)#
spanning-tree portfast
Switch
RADIUS
Server
Supplicant
Authenticator
Authentication Server
192.168.1.250
192.168.1.45
port1.0.5
