Brocade Mobility RFS Controller CLI Reference Guide (Supporting software release 5.5.0.0 and later) User Manual
Page 606
Brocade Mobility RFS Controller CLI Reference Guide
593
53-1003098-01
7
•
Wireless Controllers — Brocade Mobility RFS4000, Brocade Mobility RFS6000, Brocade
Mobility RFS7000
•
Service Platforms — Brocade Mobility RFS9510
Syntax:
remotegw ike-version [ikev1-aggr|ikev1-main|ikev2] {uniqueid}
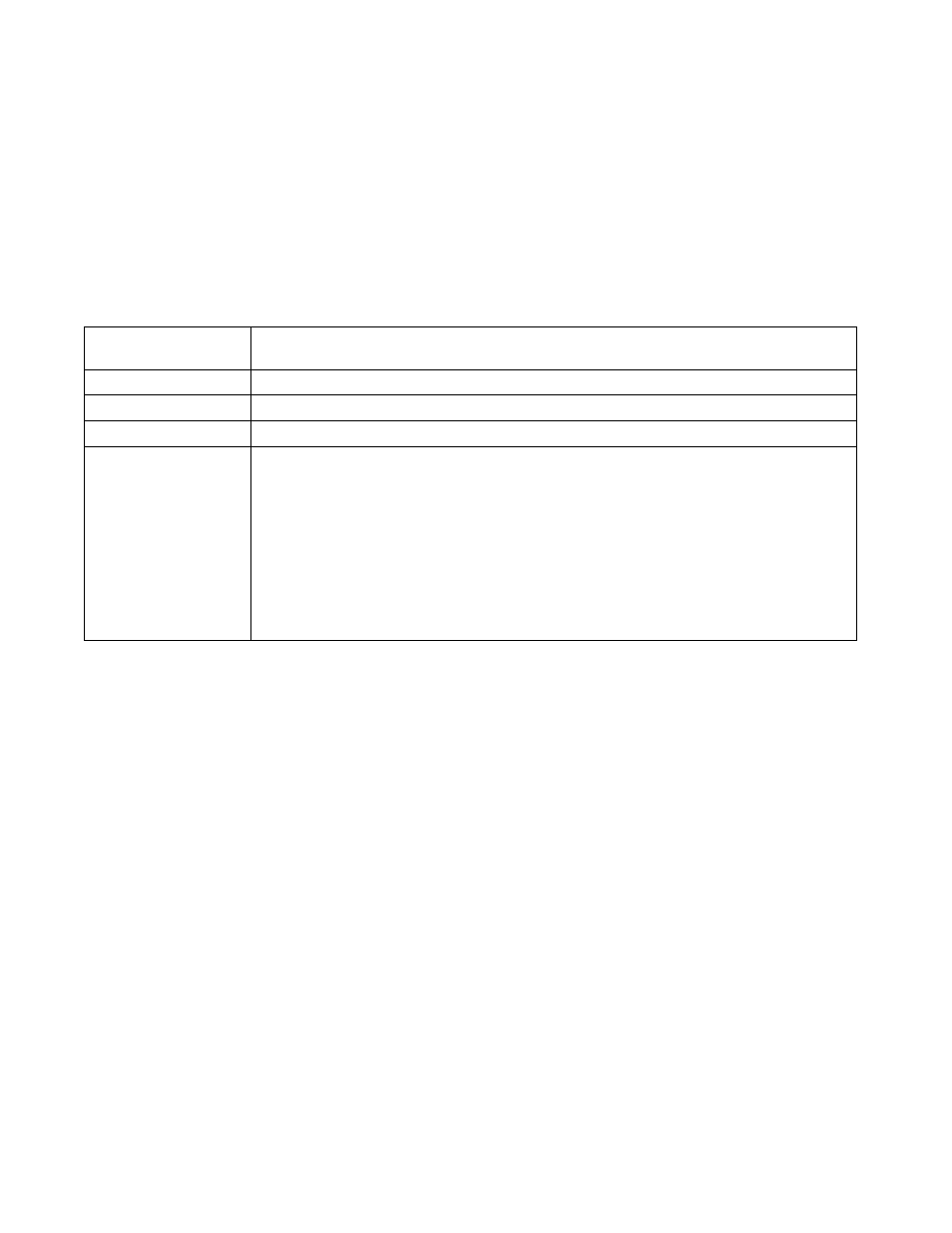
Parameters
remotegw ike-version [ikev1-aggr|ikev1-main|ikev2] {uniqueid}
Example
rfs7000-37FABE(config-profile-default-rfs7000-crypto-auto-ipsec-secure)#remot
egw ike
-version ikev2 uniqueid
rfs7000-37FABE(config-profile-default-rfs7000-crypto-auto-ipsec-secure)#
rfs7000-37FABE(config-profile-default-rfs7000-crypto-auto-ipsec-secure)#show
context
crypto auto-ipsec-secure
remotegw ike-version ikev2 uniqueid
rfs7000-37FABE(config-profile-default-rfs7000-crypto-auto-ipsec-secure)#
no
crypto-auto-ipsec-tunnel commands
Negates a command or set its defaults
Supported in the following platforms:
•
Access Points — Brocade Mobility 650 Access Point, Brocade Mobility 6511 Access Point,
Brocade Mobility 1220 Access Point, Brocade Mobility 71XX Access Point, Brocade
Mobility 1240 Access Point
•
Wireless Controllers — Brocade Mobility RFS4000, Brocade Mobility RFS6000, Brocade
Mobility RFS7000
•
Service Platforms — Brocade Mobility RFS9510
remotegw
ike-version
Configures the IKE version used for initiating auto IPSec tunnel with secure gateways
ikev1-aggr
Aggregation mode is used by the auto IPSec tunnel initiator to set up the connection
ikev1-main
Main mode is used by the auto IPSec tunnel initiator to establish the connection
ikev2
IKEv2 is the preferred method when wireless controller/AP only is used
uniqueid
This keyword is common to all of the above parameters.
•
uniqueid – Optional. Enables the assigning of a unique ID to APs (using this profile) behind a router by
prefixing the MAC address to the groupid
Providing a unique ID enables the access point, wireless controller, or service platform to uniquely identify
the destination device. This is essential in networks where there are multiple APs behind a router, or when
two (or more) APs behind two (or more) different routers have the same IP address. For example, let us
consider a scenario where there are two APs (A and B) behind two routers (1 and 2). AP ‘A’ is behind router
‘1’. And AP ‘B’ is behind router ‘2’. Both these APs have the same IP address (192.168.13.8). In such a
scenario, the controller fails to establish an Auto IPSec VPN tunnel to either APs, because it is unable to
uniquely identify them.
After enabling unique ID assignment, enable IKE unique ID check. For more information, see
