Lkm/sskm key vault high availability deployment, Exporting and, Lkm/sskm key vault – Brocade Network Advisor SAN + IP User Manual v12.3.0 User Manual
Page 1075: High availability deployment
Brocade Network Advisor SAN + IP User Manual
1003
53-1003155-01
Steps for connecting to an LKM/SSKM appliance
25
Exporting and registering the switch KAC certificates
on LKM/SSKM
1. Select Configure > Encryption from the menu task bar to display the Encryption Center
dialog box. (Refer to
Figure 376
on page 976.)
2. Select a switch from the Encryption Center Devices table, then select Switch > Export
Certificate from the menu task bar.
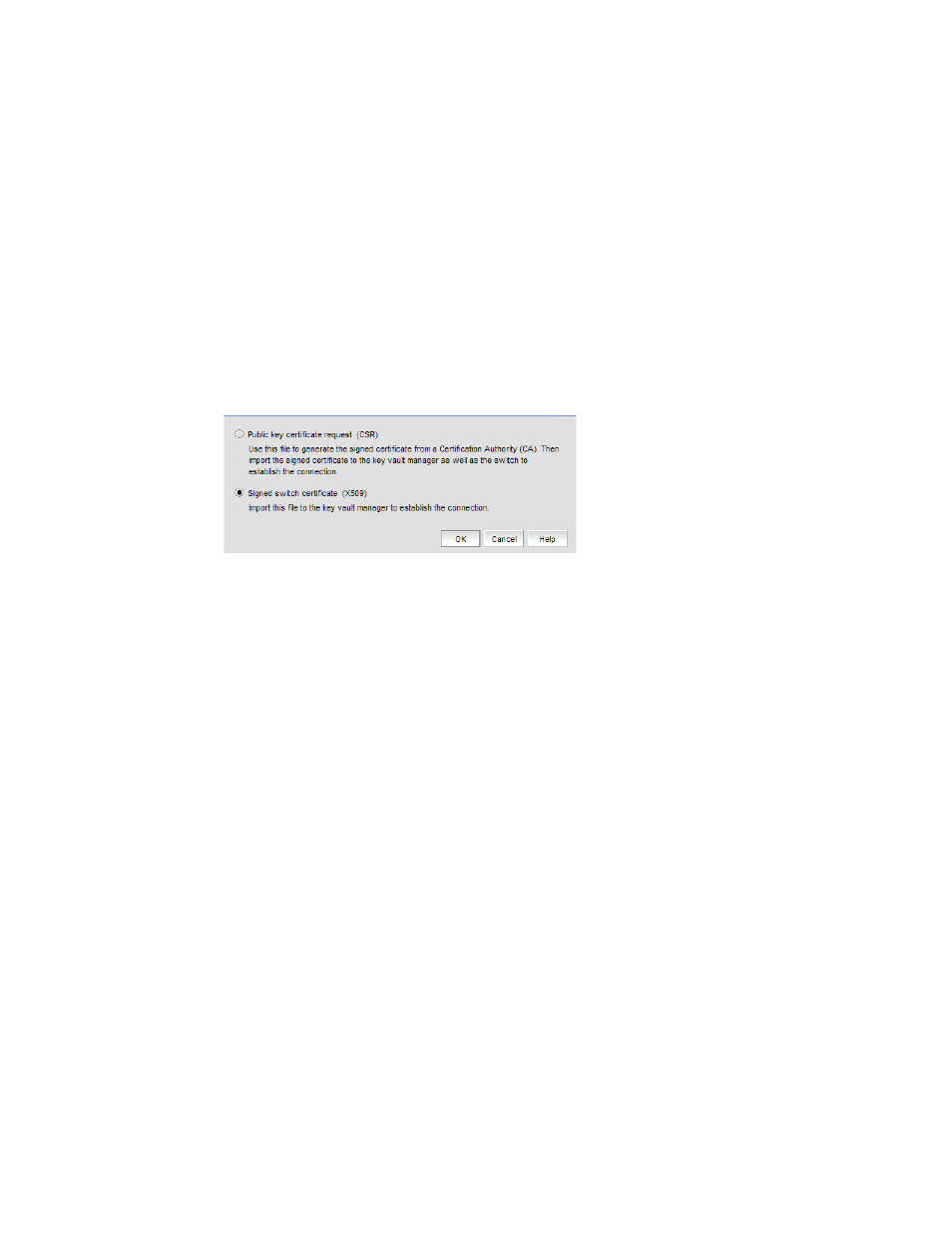
The Export Switch Certificate dialog box allows you to export a switch public key certificate
signing request (CSR) to a location you specify. (Refer to
Figure 387
.) The procedures for
submitting a CSR for signing are determined by the Certificate Authority (CA).
The CSR must be submitted to a Certificate Authority CA for signing, then imported into the
switch and the key vault. The signed switch certificate may be imported directly by a key vault.
FIGURE 387
Export switch certificate dialog box
3. Select Signed switch certificate (X.509), which allows you to export a signed switch certificate
to a location of your choosing. The default location is My Documents on your client PC. In most
cases, this certificate file should be in privacy email (.pem) format.
4. Click OK.
You are prompted to save the CSR, which can be saved to your SAN Management Program
client PC, or an external host of your choosing.
5. Register the signed KAC certificate that you exported from the member node with the NetApp
LKM/SSKM appliance.
LKM/SSKM key vault high availability deployment
LKM/SSKM appliances can be clustered to provide high availability capabilities. You can deploy
and register one LKM/SSKM with an encryption switch or blade and later deploy and register
another LKM/SSKM at any time if LKM/SSKMs are clustered or linked together. Refer to
LKM/SSKM documentation to link or cluster the LKM/SSKMs.
When LKM/SSKM appliances are clustered, both LKM/SSKMs in the cluster must be registered
and configured with the link keys before starting any crypto operations. If two LKM/SSKM key
vaults are configured, they must be clustered. If only a single LKM/SSKM key vault is configured, it
may be clustered for backup purposes, but it is not directly used by the switch.
When dual LKM/SSKMs are used with the encryption switch or blade, the dual LKM/SSKMs must
be clustered. There is no enforcement done at the encryption switch or blade to verify whether or
not the dual LKM/SSKMs are clustered, but key creation operations will fail if you register
non-clustered dual LKM/SSKMs with the encryption switch or blade.
