Scheduling a security configuration deployment – Brocade Network Advisor SAN + IP User Manual v12.3.0 User Manual
Page 1018
946
Brocade Network Advisor SAN + IP User Manual
53-1003155-01
Security configuration deployment
22
5. Click the Snapshot Use check box and click the ellipsis button to select the product monitoring
template.
NOTE
The Snapshot Use check box is only available for IronWare products.
The Pre-Post Snapshot Properties dialog box displays.
6. Select the product monitoring template you want to use from the CLI Template list.
7. Select one or more of the following to capture snapshots:
•
Select the Pre-deployment check box to capture a snapshot of the product’s configuration
prior to deployment of the security configuration.
•
Select the Post-deployment check box to capture a snapshot of the product’s configuration
after deployment of the security configuration.
If you select the Post-deployment check box, enter the amount of time (between 1 and
300 seconds) you want the application to wait before capturing the snapshot in the Delay
field.
8. Select one or more ports or products to which you want to deploy the configuration in the
Available Targets list and click the right arrow button to move them to the Selected Targets list.
9. Click OK on the Deploy to Products - Layer 2 ACL dialog box.
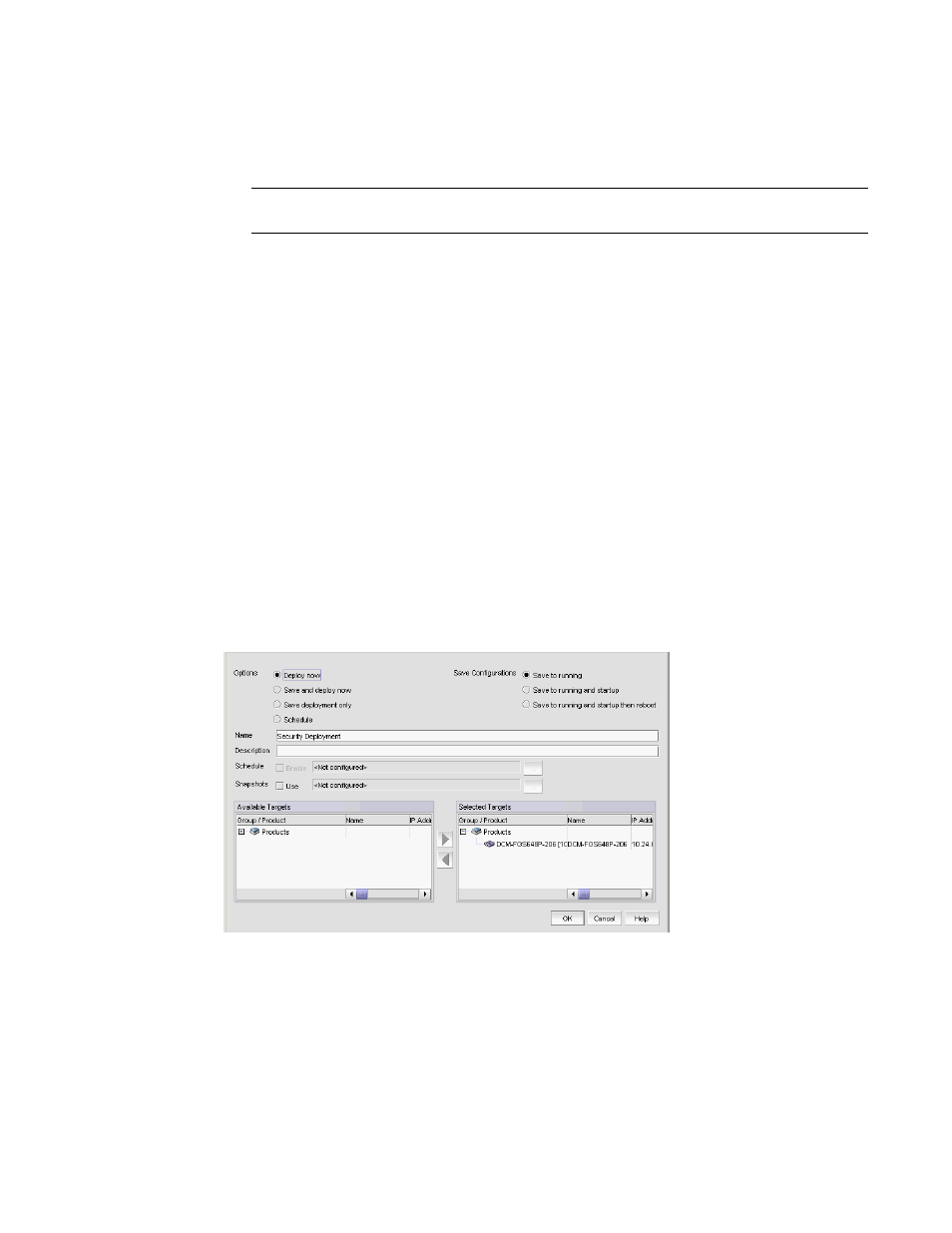
Scheduling a security configuration deployment
To schedule a security configuration deployment, complete the following steps.
FIGURE 369
Deploy to Product/Ports dialog box
1. Select Configure > Security > Layer 2 ACL > Product.
The Device_Name - Layer 2 ACL Configuration dialog box displays.
