Configuration considerations – Brocade Multi-Service IronWare Multiprotocol Label Switch (MPLS) Configuration Guide (Supporting R05.6.00) User Manual
Page 194
170
Multi-Service IronWare Multiprotocol Label Switch (MPLS) Configuration Guide
53-1003031-02
Dynamic Bypass LSPs
1
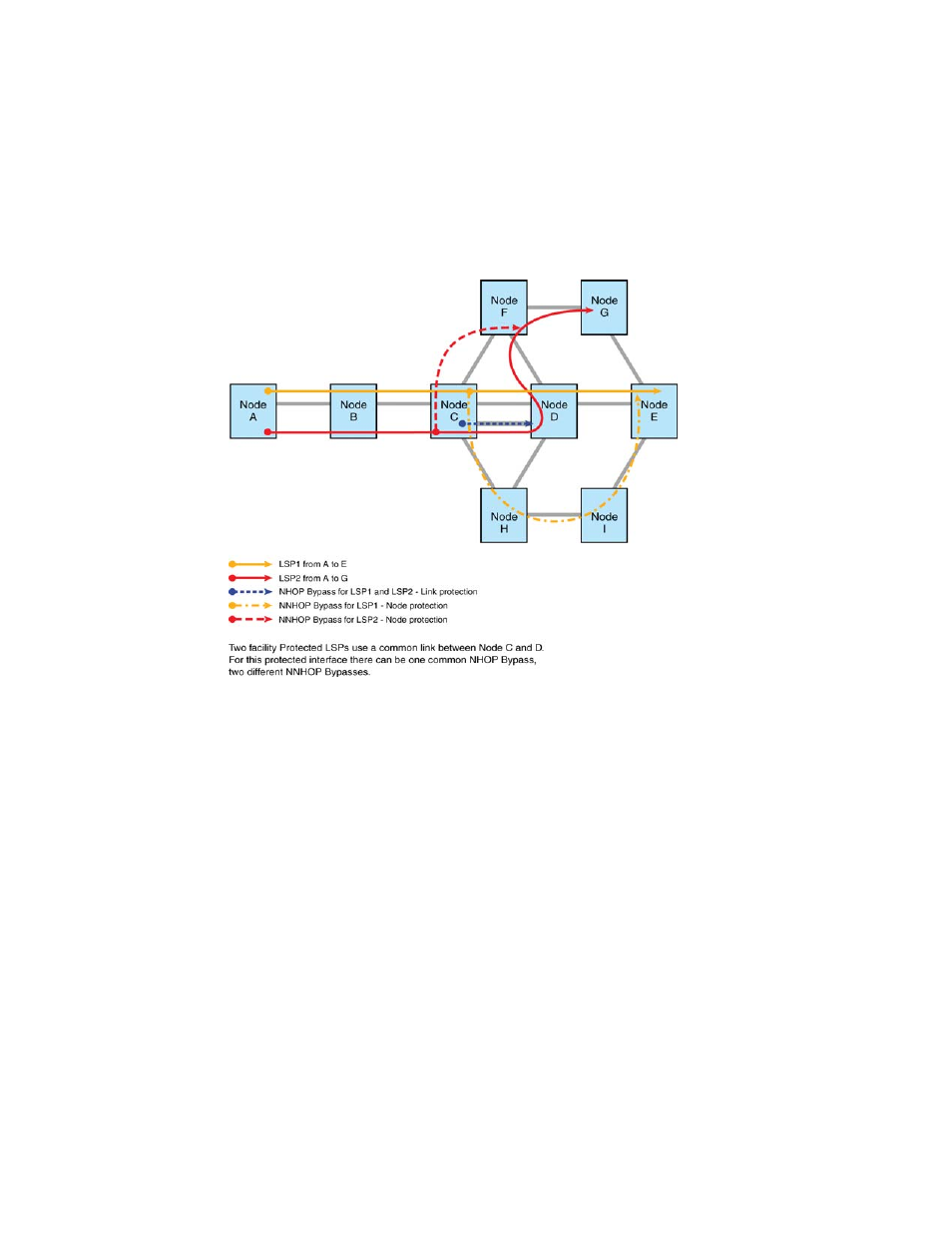
A link which is protected by the bypass LSP is called a protected-link, protected interface, or an
excluded interface. Multiple facility protected LSPs use a common downstream link which becomes
a protected link for all of them. This signifies that there is at least one dynamic bypass LSP to the
NHOP (node connected by the interface) and many NNHOP dynamic bypass LSPs based on the
path taken by the facility protected LSP. Similarly, there are bypass LSPs to several different
NNNHOP nodes.
FIGURE 24
Two facility protected LSPs using a common link
Configuration considerations
•
Dynamic bypass LSP modification (make-before-break (MBB)) is not supported except for a
case of re-optimization. When a new protected LSP requests more bandwidth, no automatic
MBB is performed for the existing dynamic bypass LSP. Re-optimization makes use of
make-before-break, to modify the LSP, so it can create the new instance of the dynamic bypass
LSP. The newly created dynamic bypass LSP uses the latest attributes from the global and
interface level dynamic bypass configurations. Re-optimization is carried out as to a
re-optimization timer expiry.
•
Dynamic bypass optimization with modified bandwidth is performed using MBB during the
optimization process (timer expiry or user initiated). No detour or backup re-optimization to
minimize dynamic bypass LSPs is completed in this release. Here, the ‘detour/backup
re-optimization’ does not refer to LSP path re-optimization; it refers to the realignment of
backup paths on the bypass LSPs so there is a minimum number of bypasses with optimal use
of their bandwidths.
•
One dynamic bypass is created and ten backups occupy this dynamic bypass.
•
A second dynamic bypass is created and the 11th backup occupies this dynamic bypass.
•
After some time, one backup from the first dynamic bypass goes away, which leave one
megabyte per second unoccupied in the first dynamic bypass.
