Verify the configuration, Applying rsa digital signature in ike negotiation, Network requirements – H3C Technologies H3C SecPath F1000-E User Manual
Page 799
25
•
Click Apply. When the system displays “Certificate request has been submitted”, click OK to
confirm.
# Retrieve the CRL.
•
After retrieving a local certificate, select VPN > PKI > CRL from the navigation tree.
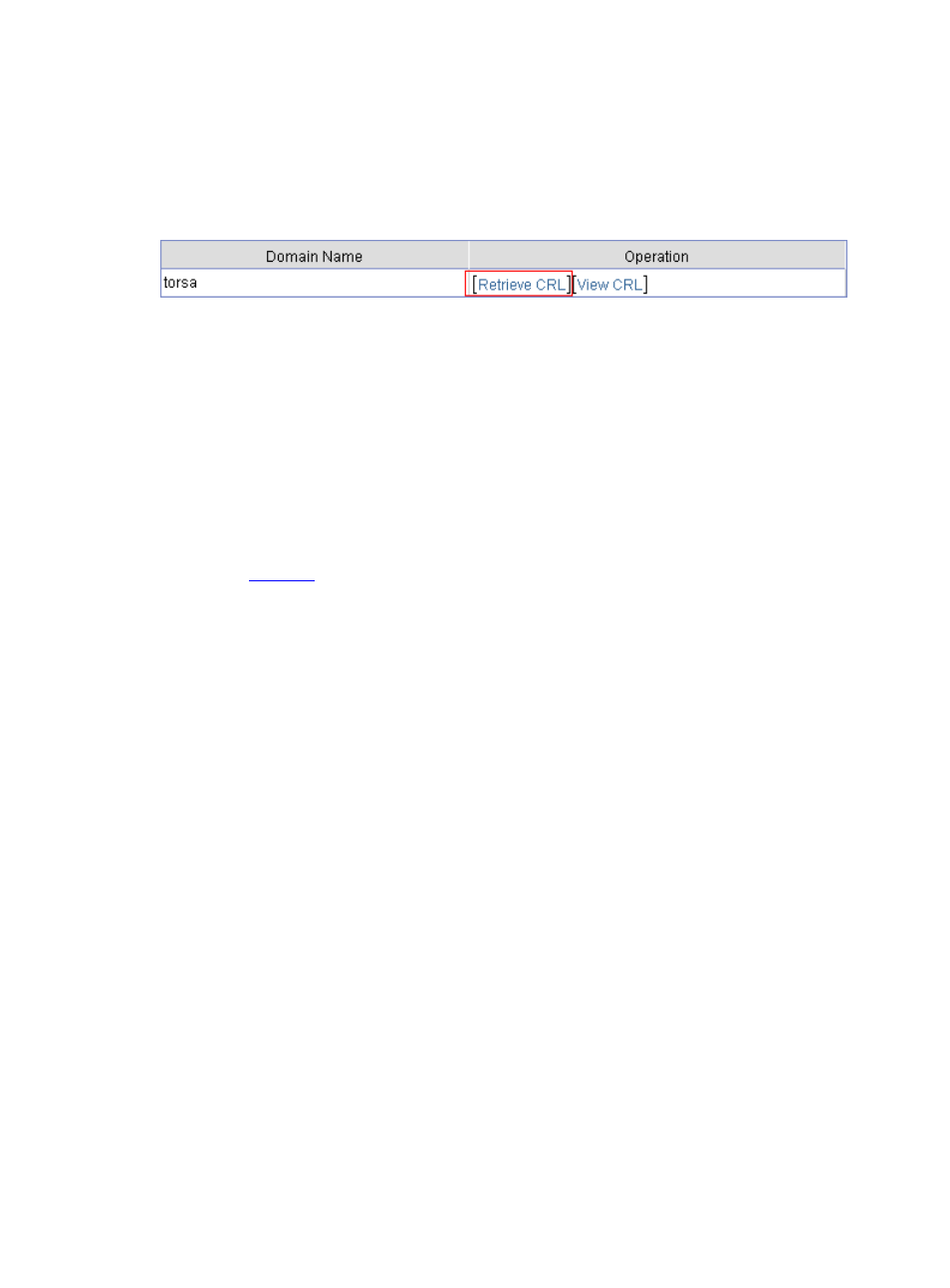
Figure 28 Retrieve CRL
•
•
Click Retrieve CRL of the PKI domain of torsa.
Verify the configuration
After the above configuration, select VPN > PKI > Certificate from the navigation tree to view detailed
information about the retrieved CA certificate and local certificate, or select VPN > PKI > CRL from the
navigation tree to view detailed information about the retrieved CRL.
Applying RSA Digital Signature in IKE Negotiation
Network requirements
As shown in
,
•
An IPsec tunnel is set up between Device A and Device B to secure the traffic between Host A on
subnet 10.1.1.0/24 and Host B on subnet 11.1.1.0/24.
•
Device A and Device B use IKE for IPsec tunnel negotiation and RSA digital signature of a PKI
certificate system for identity authentication.
•
Device A and Device B use different CAs. They may also use the same CA as required.
