Figure 5 – H3C Technologies H3C SecPath F1000-E User Manual
Page 703
6
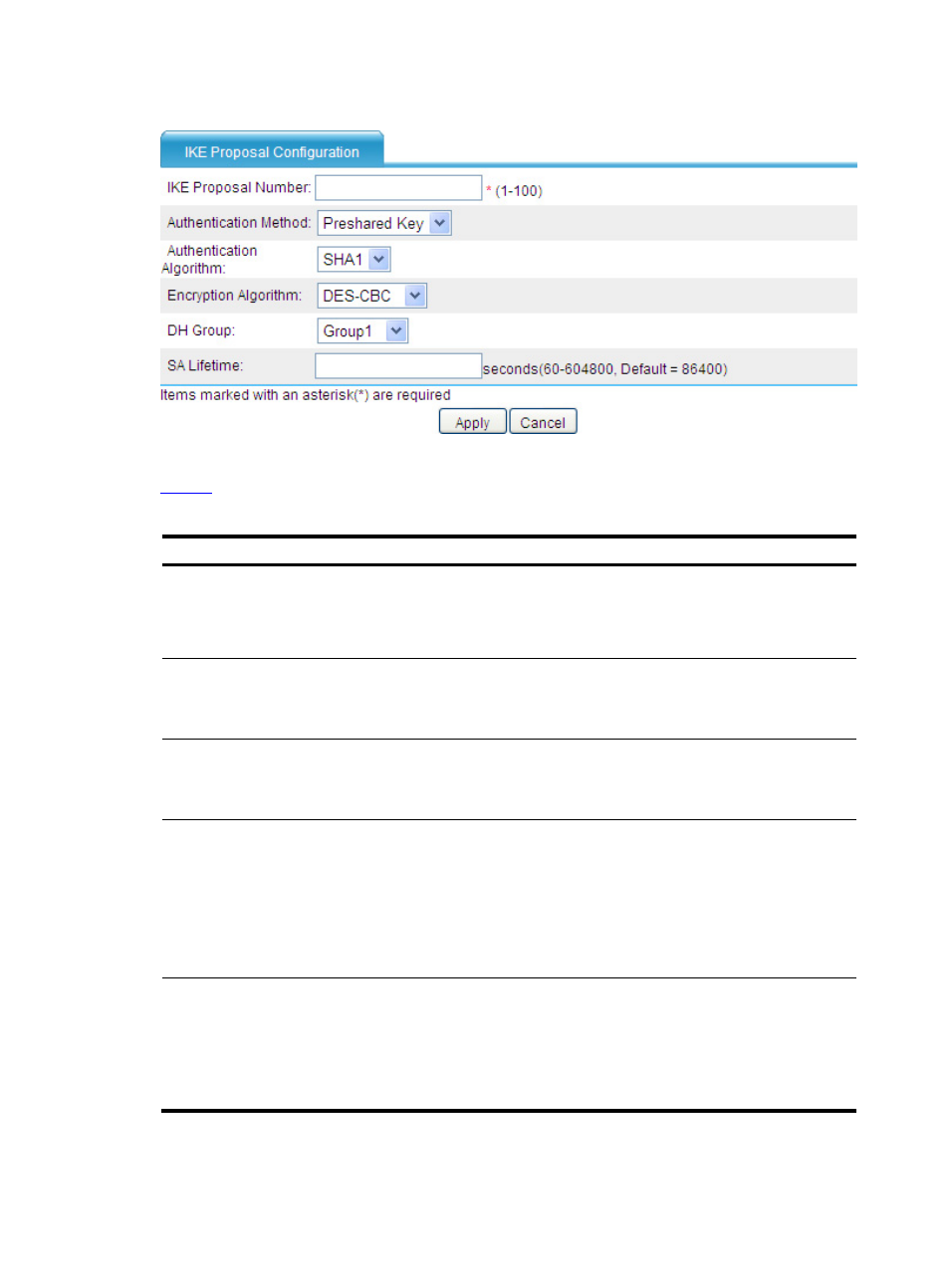
Figure 5 Add an IKE proposal
describes the configuration items for creating an IKE proposal.
Table 3 IKE proposal configuration items.
Item
Description
IKE Proposal
Number
Type the IKE proposal number.
The number also stands for the priority of the IKE proposal, with a smaller value meaning
a higher priority. During IKE negotiation, the system matches IKE proposals in order of
proposal number, starting from the smallest one.
Authentication
Method
Select the authentication method to be used by the IKE proposal.
Preshared Key: Uses the pre-shared key method.
RSA Signature: Uses the RSA digital signature method.
Authentication
Algorithm
Select the authentication algorithm to be used by the IKE proposal.
SHA1: Uses HMAC-SHA1.
MD5: Uses HMAC-MD5.
Encryption
Algorithm
Select the encryption algorithm to be used by the IKE proposal.
DES-CBC: Uses the DES algorithm in CBC mode and 56-bit keys for encryption.
3DES-CBC: Uses the 3DES algorithm in CBC mode and 168-bit keys for encryption.
AES-128: Uses the AES algorithm in CBC mode and 128-bit keys for encryption.
AES-192: Uses the AES algorithm in CBC mode and 192-bit keys for encryption.
AES-256: Uses the AES algorithm in CBC mode and 256-bit keys for encryption.
DH Group
Select the DH group to be used in key negotiation phase 1.
Group1: Uses the 768-bit Diffie-Hellman group.
Group2: Uses the 1024-bit Diffie-Hellman group.
Group5: Uses the 1536-bit Diffie-Hellman group.
Group14: Uses the 2048-bit Diffie-Hellman group.
