Relationship between ike and ipsec, Protocols, Configuring ike – H3C Technologies H3C SecPath F1000-E User Manual
Page 700: Configuration task list
3
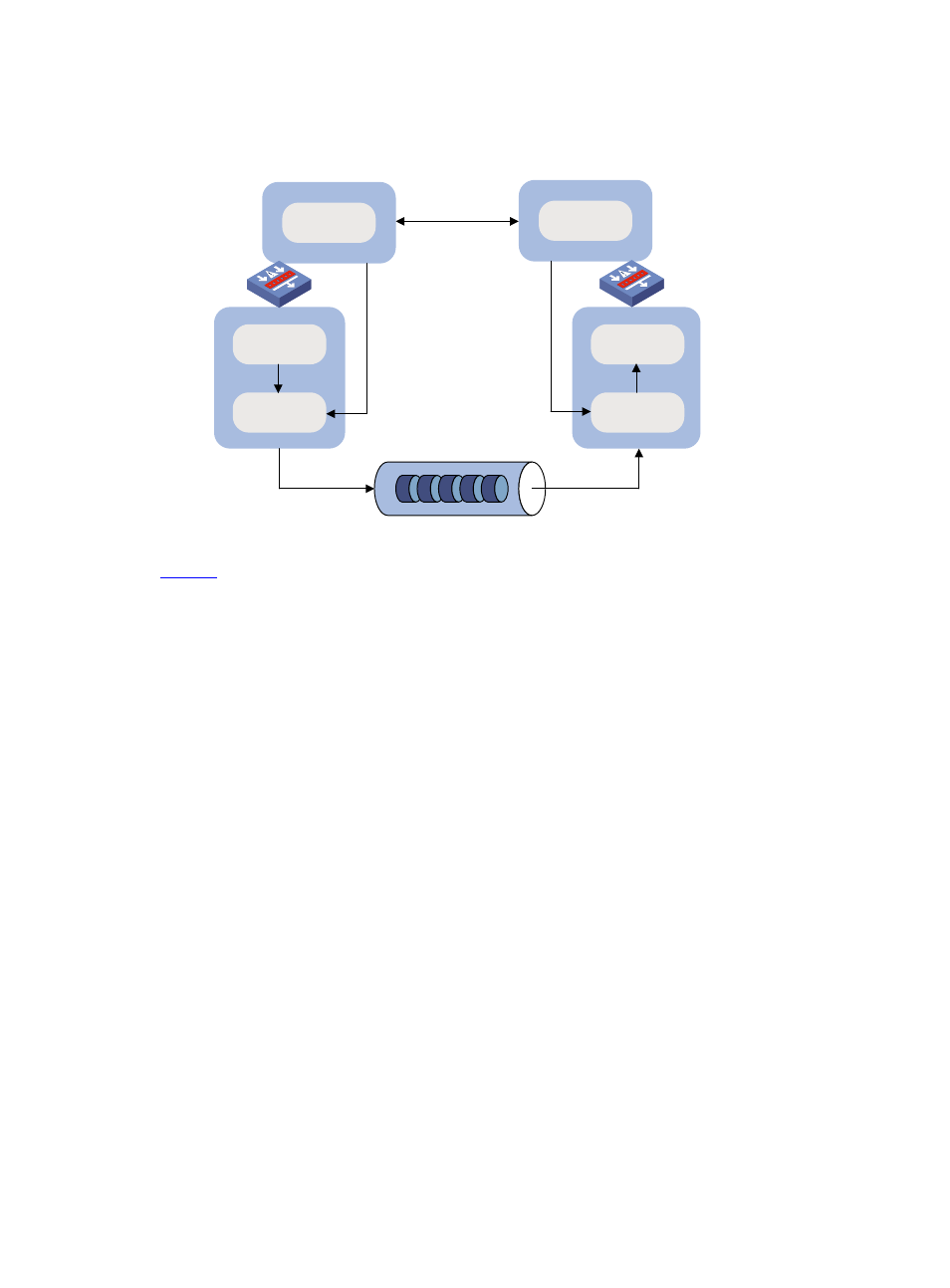
Relationship Between IKE and IPsec
Figure 2 Relationship between IKE and IPsec
IKE
TCP/UDP
IPsec
TCP/UDP
IPsec
IKE
SA
negotiation
SA
Device A
Encrypted IP packets
Device B
illustrates the relationship between IKE and IPsec:
•
IKE is an application layer protocol using UDP and functions as the signaling protocol of IPsec.
•
IKE negotiates SAs for IPsec and delivers negotiated parameters and generated keys to IPsec.
•
IPsec uses the SAs set up through IKE negotiation for encryption and/or authentication of IP
packets.
Protocols
IKE related protocols include:
•
RFC 2408: Internet Security Association and Key Management Protocol (ISAKMP)
•
RFC2409: The Internet Key Exchange (IKE)
•
RFC2412: The OAKLEY Key Determination Protocol
Configuring IKE
Configuration Task List
Before configuring IKE, you need to:
•
Determine the strength of the algorithms for IKE negotiation, namely the security protection level,
including the identity authentication method, encryption algorithm, authentication algorithm, and
DH group. Different algorithms provide different levels of protection. A stronger algorithm means
more resistant to decryption of protected data but requires more resources. Generally, the longer
the key, the stronger the algorithm.
•
Determine the pre-shared key or the PKI domain the certificate belongs to. For PKI configuration, see
PKI Configuration.
