P2p traffic control configuration example, Network requirements, Configuration steps – H3C Technologies H3C SecPath F1000-E User Manual
Page 663: Table 3
5
Table 3 Traffic statistics items
Item Description
Zone
Displays the security zone for which traffic statistics is
performed.
Protocol
Displays the protocol for which traffic statistics is
performed.
Received Packet(s)
Displays the number of packets of this protocol
received in this zone.
Received Byte(s)
Displays the number of bytes of packets of this
protocol received in this zone.
Sent Packet(s)
Displays the number of packets of this protocol sent
from this zone.
Sent Byte(s)
Displays the number of bytes of packets of this
protocol sent from this zone.
P2P traffic control configuration task list
.
P2P Traffic Control Configuration Example
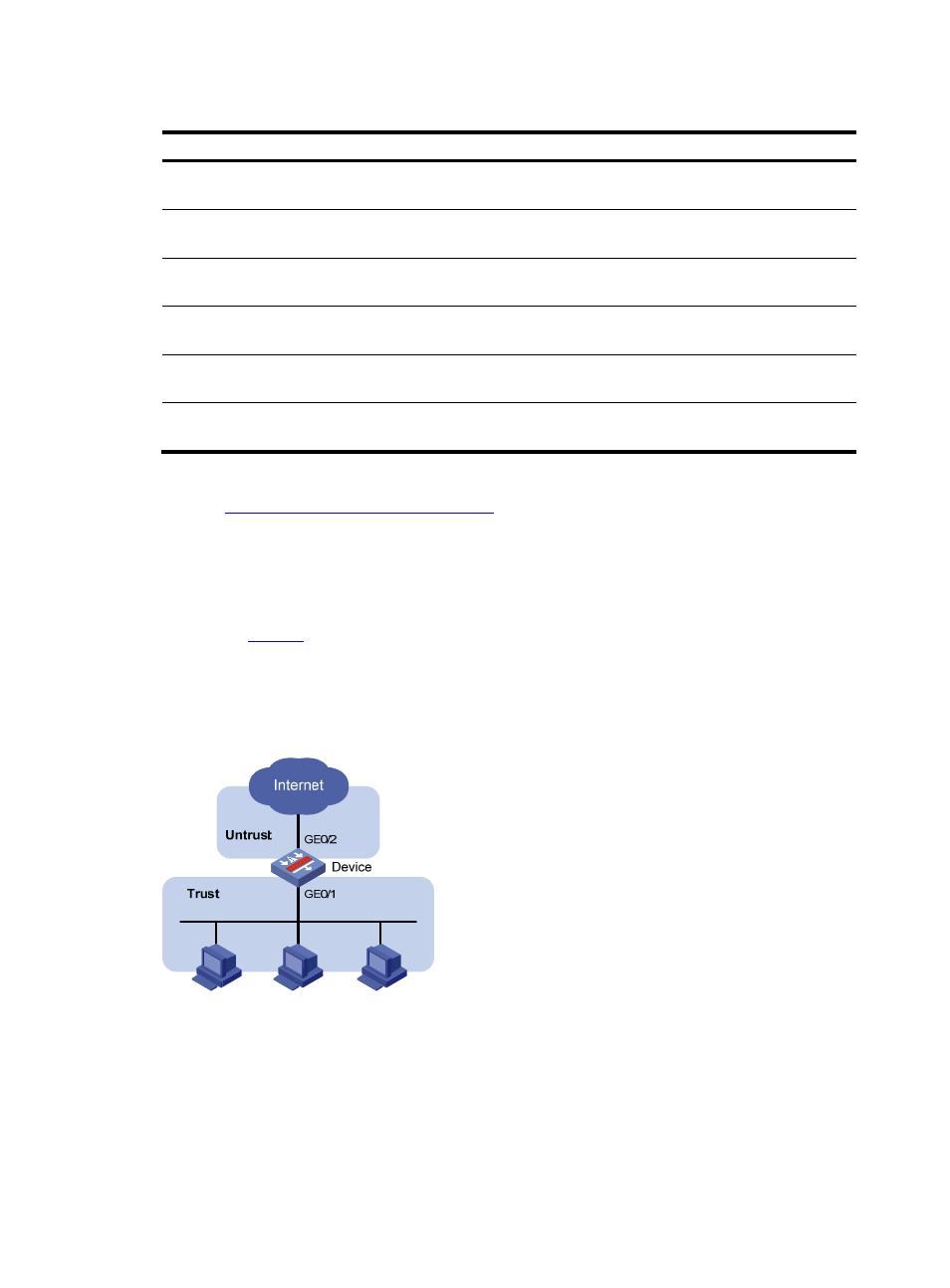
Network requirements
As shown in
, an internal network connects to the Internet via Device. The internal network is in
the trust zone of Device and the Internet is in the untrust zone of Device.
Perform configuration on Device to prevent hosts in the internal network from using the BitTorrent or
eMult/eDonkey client to download files.
Figure 6 Network diagram for P2P traffic control configuration
Configuration steps
# Configure security zones for interfaces (omitted).
# Load the signature file meta_newemule.mtd.
•
Select Identification > P2P Identify > File Load from the navigation tree.
