Tcp proxy configuration example, Network requirements, Configuration procedure – H3C Technologies H3C SecPath F1000-E User Manual
Page 648
6
Item
Description
Lifetime(min)
Lifetime for the IP address entry under protection. This item is displayed as –
for static IP address entries.
When the time reaches 0, the protected IP address entry will be deleted.
Number of Rejected
Amount of requests for TCP connection requests matching the protected IP
address entry but were proved to be illegitimate.
TCP proxy configuration task list
TCP Proxy Configuration Example
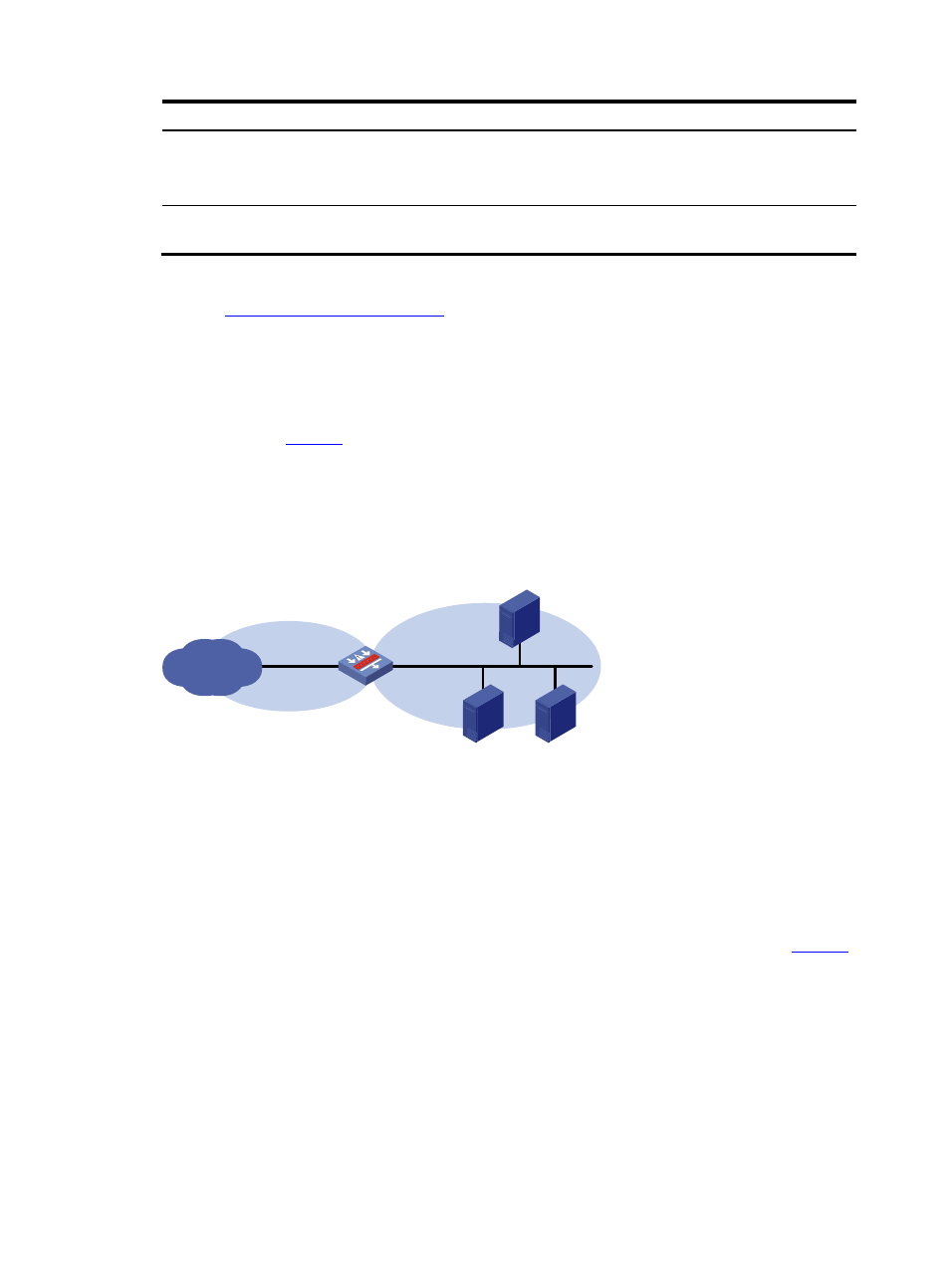
Network requirements
•
As shown in
, configure bidirectional TCP proxy on Device to protect Server A, Server B,
and Server C against SYN flood attacks.
•
Add a protected IP address entry for Server A manually and configure dynamic TCP proxy for the
other servers.
Figure 8 Network diagram for TCP proxy configuration
Device
GE0/1
10.0.0.1/24
GE0/2
20.0.0.1/24
IP network
Server A
Server C
Server B
20.0.0.10/24
Untrust
Trust
Configuration procedure
# Assign IP addresses for the interfaces and then add interface GigabitEthernet 1/1 to zone Untrust, and
GigabitEthernet 1/2 to zone Trust. (Omitted)
# Set the TCP proxy mode to bidirectional and enable TCP proxy for zone Untrust.
•
Select Intrusion Detection > TCP Proxy > TCP Proxy Configuration from the navigation
tree. Select the bidirectional mode and enable TCP proxy for zone Untrust as shown in
.
