Ipsec sa setup modes – H3C Technologies H3C SecPath F1000-E User Manual
Page 715
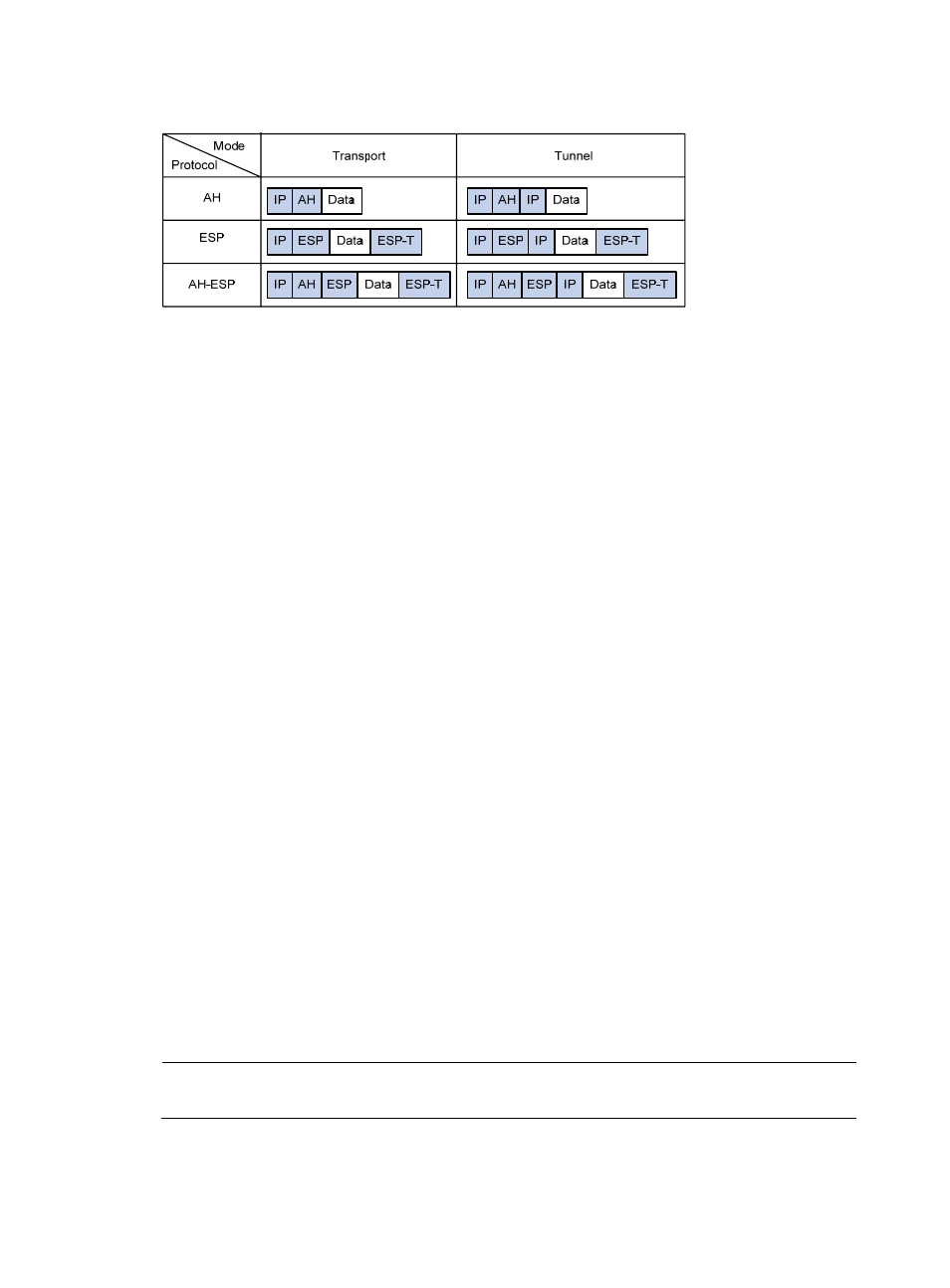
3
Figure 1 Encapsulation by security protocols in different modes
Authentication algorithms and encryption algorithms
1.
Authentication algorithms
IPsec uses hash algorithms to perform authentication. A hash algorithm produces a fixed-length digest for
an arbitrary-length message. IPsec peers respectively calculate message digests for each packet. If the
resulting digests are identical, the packet is considered intact.
IPsec supports two hash algorithms for authentication:
•
MD5, which takes as input a message of arbitrary length and produces a 128-bit message digest.
•
SHA-1, which takes as input a message of a maximum length less than the 64th power of 2 in bits
and produces a 160-bit message digest.
Compared with SHA-1, MD5 is faster but less secure.
2.
Encryption algorithms
IPsec mainly uses symmetric encryption algorithms, which encrypt and decrypt data by using the same
keys. Currently, three encryption algorithms are available for IPsec on the device:
•
Data Encryption Standard (DES), which encrypts a 64-bit plain text block with a 56-bit key. DES is
the least secure but the fastest algorithm. It is sufficient for general security requirements.
•
Triple DES (3DES), which encrypts plain text data with three 56-bit DES keys. The key length totals
up to 168 bits. It provides moderate security strength and is slower than DES.
•
Advanced Encryption Standard (AES), which encrypts plain text data with a 128-bit, 192-bit, or
256-bit key. AES provides the highest security strength and is slower than 3DES.
IPsec SA setup modes
You can set up IPsec SAs manually or in ISAKMP mode through IKE negotiation:
•
In manual mode, you must manually configure and maintain all SA settings. Advanced features like
periodical key update are not available. However, this mode implements IPsec independently of
IKE.
•
In ISAKMP mode, IKE automatically negotiates and maintains IPsec SAs for IPsec.
If the number of IPsec tunnels in your network is small, use the manual mode. If the number of IPsec
tunnels is large, use the ISAKMP mode.
NOTE:
At present, the Web interface supports only the ISAKMP mode.
