Tcp proxy configuration, Overview, Introduction to syn flood attack – H3C Technologies H3C SecPath F1000-E User Manual
Page 643: Introduction to tcp proxy
1
TCP Proxy Configuration
Overview
Introduction to SYN Flood Attack
As a general rule, the establishment of a TCP connection is a three-way handshake:
1.
The request originator sends a SYN message to the target server.
2.
After receiving the SYN message, the target server establishes a TCP connection in the
SYN_RECEIVED state, returns a SYN ACK message to the originator, and waits for a response.
3.
After receiving the SYN ACK message, the originator returns an ACK message. Thus, the TCP
connection is established.
Attackers may exploit the TCP connection establishment to mount SYN flood attacks. Attackers send a
large number of SYN messages to the server to establish TCP connections, but they never make any
response to SYN ACK messages. As a result, a large amount of incomplete TCP connections are
established, making the server unable to handle services normally.
Introduction to TCP Proxy
The TCP proxy feature can protect the server from SYN flood attacks. The TCP client sets up a TCP
connection with the TCP server through a TCP proxy. The TCP proxy intercepts SYN requests from the TCP
clients and verifies whether the requests are SYN flood attack packets. If so, the TCP proxy drops the
requests, thus protecting the TCP server against SYN flood attacks.
TCP proxy can work in two modes:
•
Unidirectional proxy: Only processes packets from the TCP client
•
Bidirectional proxy: Processes packets from both the TCP client and TCP server.
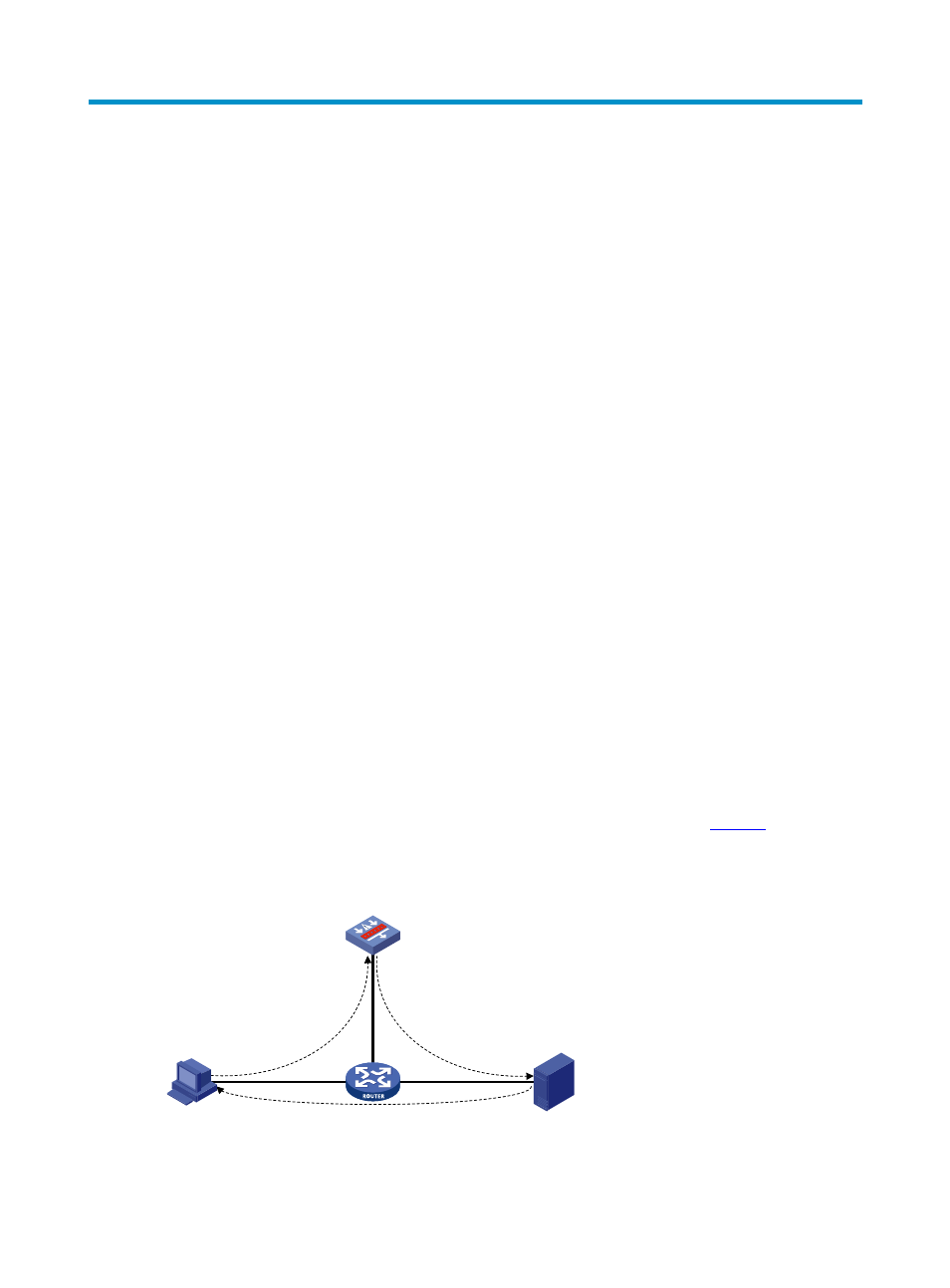
You can choose a proper mode according to your network scenario. As shown in
, packets from
the TCP client to the server go through the TCP proxy, while packets from the TCP server to the client are
transferred by the Router in between. Thus unidirectional proxy is required.
Figure 1 Network diagram for unidirectional proxy
TCP client
TCP proxy
TCP server
Router
