Ike configuration example, Network requirements, Configuration procedure – H3C Technologies H3C SecPath F1000-E User Manual
Page 709
12
IKE Configuration Example
Network requirements
•
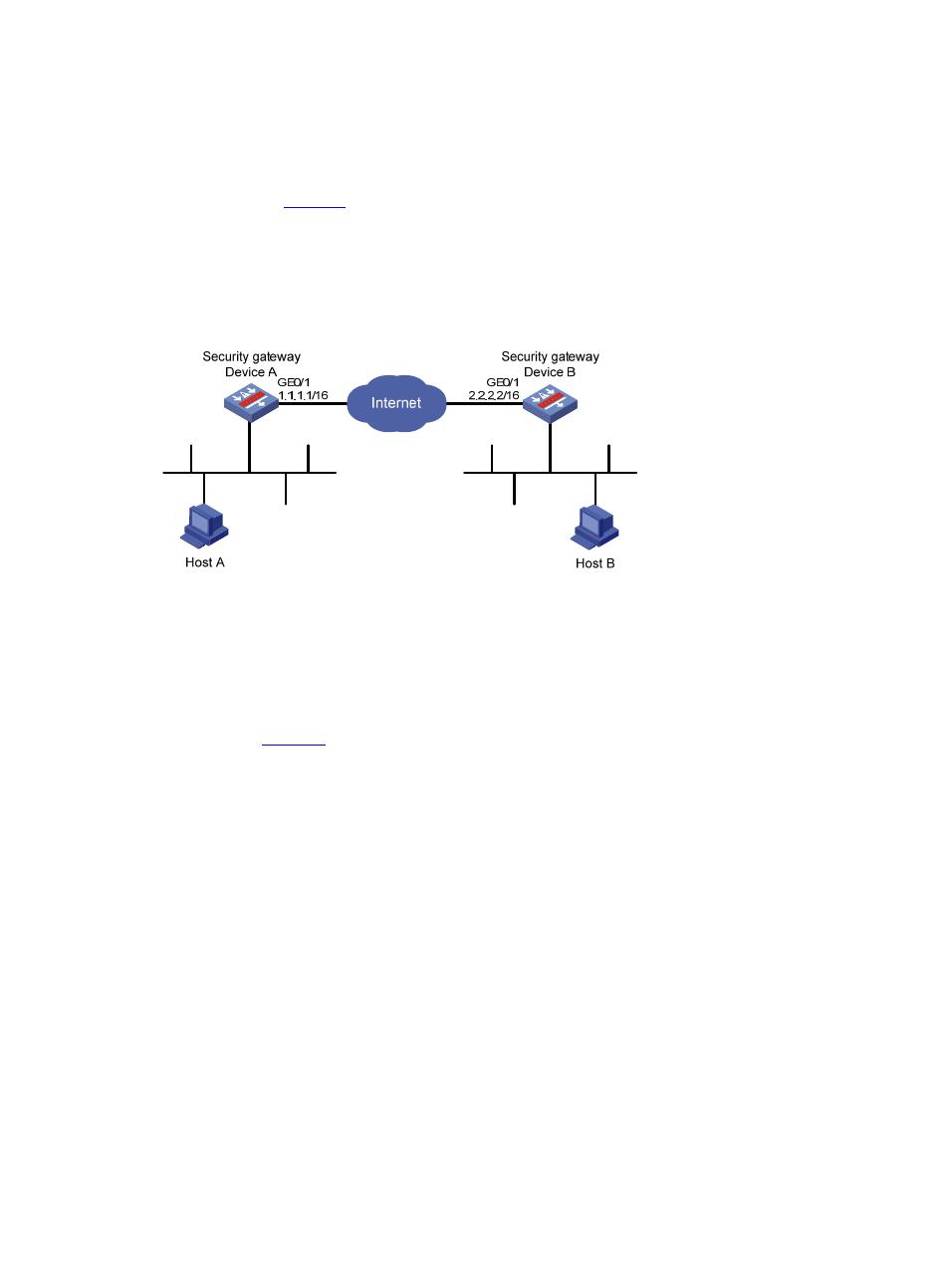
As shown in
, an IPsec tunnel is established through IKE negotiation between the security
gateways Device A and Device B to allow secure communication between Host A and Host B.
•
Device A is configured with an IKE proposal using the sequence number of 10 and the
authentication algorithm of MD5. Device B uses the default IKE proposal.
•
The two devices use the pre-shared key authentication method.
Figure 11 Network diagram for IKE configuration
Configuration procedure
Step1
Configure security gateway Device A
# Configure the IKE peer.
•
Select VPN > IKE > Peer from the navigation tree and then click Add. Perform the configurations
shown in
.
This manual is related to the following products:
