Viewing ike sas – H3C Technologies H3C SecPath F1000-E User Manual
Page 708
11
Viewing IKE SAs
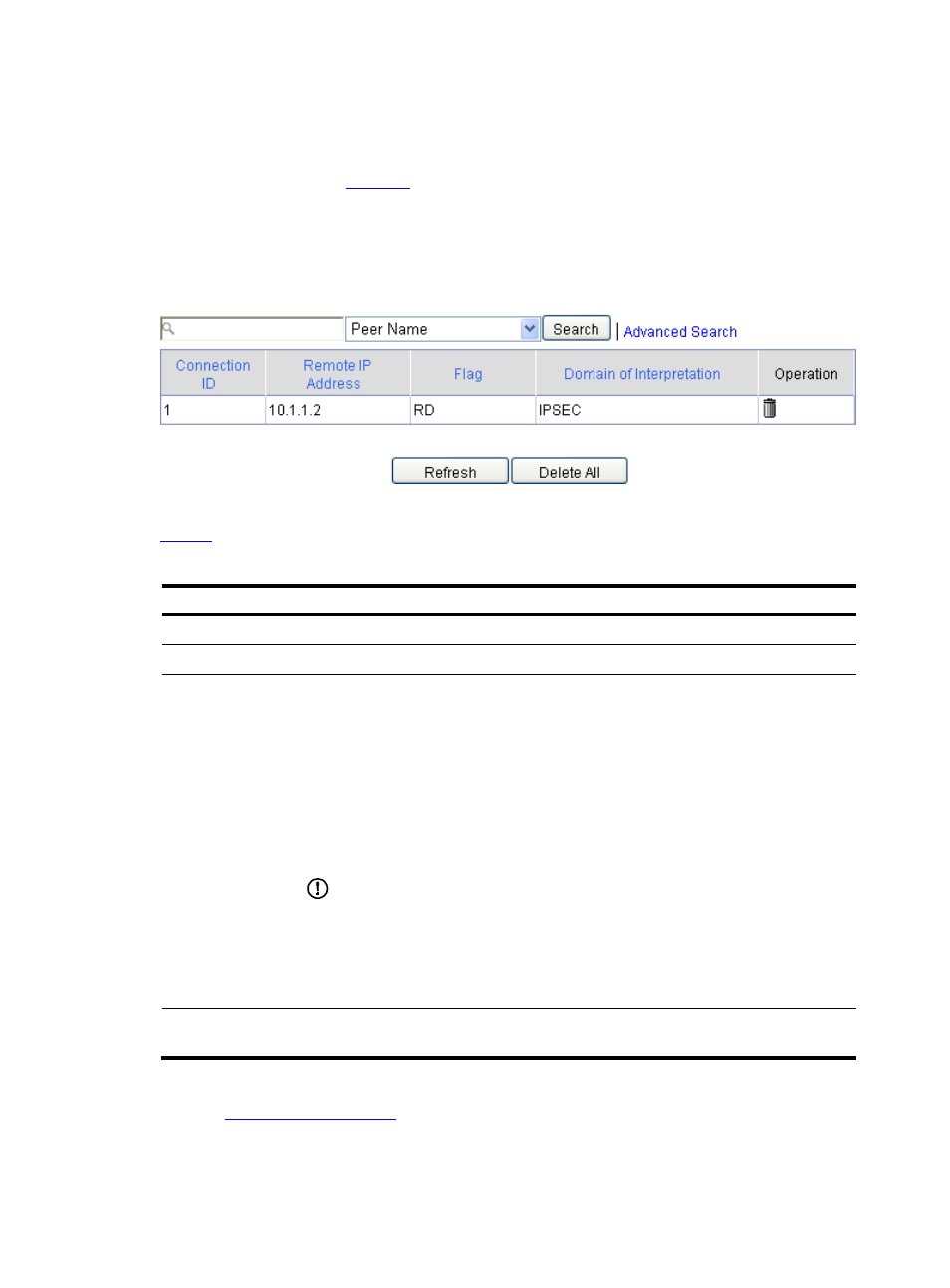
Select VPN > IKE > IKE SA from the navigation tree to display brief information about established
ISAKMP SAs, as shown in
. You can click Delete All to remove all ISAKMP SAs. Note that
when you clear a local IPsec SA, if the corresponding ISAKMP SA is still present, the local end will send
a Delete Message to the remote end across the ISAKMP SA, notifying the remote end to delete the
corresponding IPsec SA. If the corresponding ISAKMP SA is no longer present, the local end cannot
notify the remote end to clear the corresponding IPsec SA.
Figure 10 IKE SA list
describes the fields of IKE SA information.
Table 6 IKE SA information fields
Field
Description
Connection ID
Identifier of the ISAKMP SA
Remote IP Address Remote IP address of the SA
Flag
Status of the SA, which may be:
•
RD (ready): Indicates that the SA has already been established and is ready for use.
•
ST (stayalive): Indicates that the local end is the tunnel negotiation initiator.
•
RL (replaced): Indicates that the tunnel has been replaced and will be cleared soon.
•
FD (fading): Indicates that the soft lifetime expires but the tunnel is still in use. The
tunnel will be deleted when the hard lifetime expires.
•
TO (timeout): Indicates the SA has received no keepalive packets after the last
keepalive timeout. If no keepalive packets are received before the next keepalive
timeout, the SA will be deleted.
IMPORTANT:
IKE maintains the link status of an ISAKMP SA by keepalive packets. Generally, if the
peer is configured with the keepalive timeout, you need to configure the keepalive
packet transmission interval on the local end. If the peer receives no keepalive packet
during the timeout interval, the ISAKMP SA will be tagged with the TIMEOUT tag (if it
does not have the tag), or be deleted along with the IPsec SAs it negotiated (when it
has the tag already).
Domain of
Interpretation
Interpretation domain that the SA belongs to
.
