Configuring udp flood detection – H3C Technologies H3C SecPath F1000-E User Manual
Page 624
4
NOTE:
•
In a security zone, you can configure multiple protected hosts and one global connection rate
threshold.
•
For a host, the host-specific setting overrides the global setting of the security zone in case conflict
occurs.
Configuring UDP Flood Detection
NOTE:
UDP flood detection is mainly intended to protect servers and is usually configured for an internal zone.
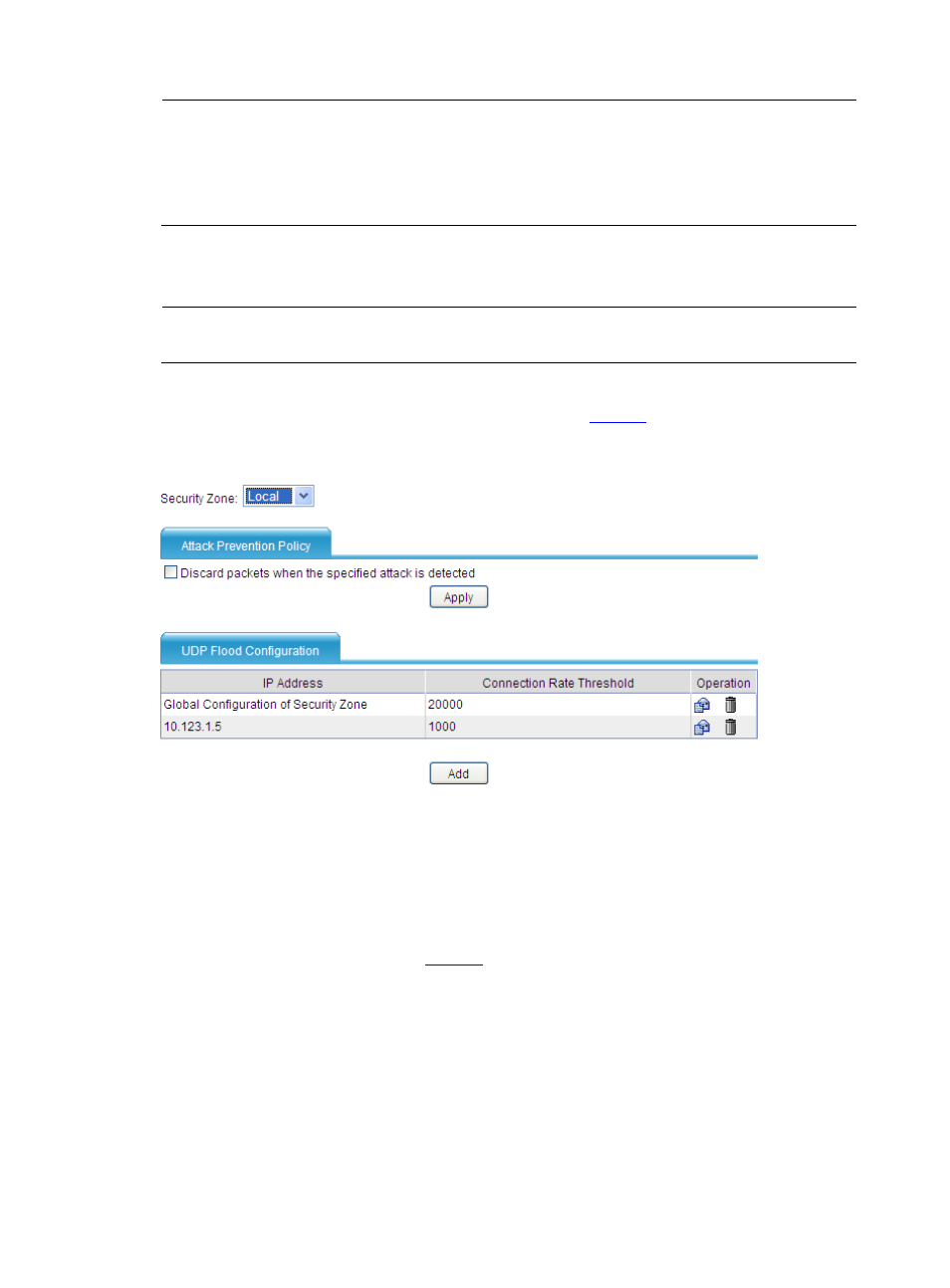
From the navigation tree, select Intrusion Detection > Traffic Abnormality > UDP Flood to
enter the UDP flood detection configuration page, as shown in
. You can select a security zone
and then view and configure UDP flood detection rules for the security zone.
Figure 3 UDP flood detection configuration page
Do the following to configure UDP flood detection:
1.
In the Attack Prevention Policy area, specify the protection action to be taken upon detection
of a UDP flood attack. If you do not select the Discard packets when the specified attack
is detected option, the device only collects UDP flood attack statistics.
2.
In the UDP Flood Configuration area, view the configured UDP flood detection rules, or click
Add to enter the page shown in
to configure a UDP flood detection rule.
