Functions of ike in ipsec – H3C Technologies H3C SecPath F1000-E User Manual
Page 699
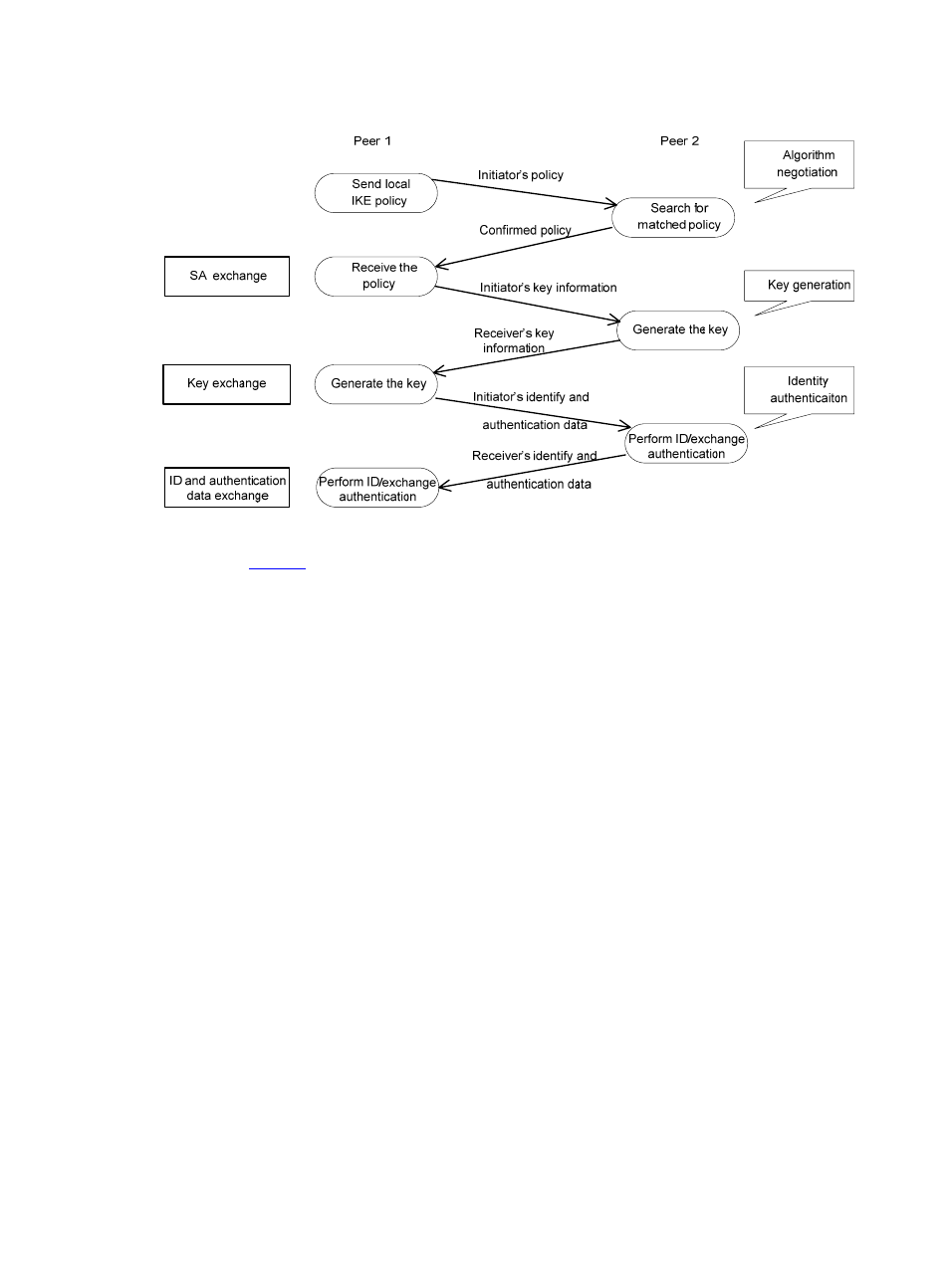
2
Figure 1 IKE exchange process in main mode
As shown in
, the main mode of IKE negotiation in phase 1 involves three pairs of messages:
•
SA exchange, used for negotiating the security policy.
•
Key exchange, used for exchanging the Diffie-Hellman public value and other values like the
random number. Key data is generated in this stage.
•
ID and authentication data exchange, used for authentication of identity and exchanged data in
phase 1.
The main difference between main mode and aggressive mode is that aggressive mode does not provide
identity protection and only exchanges the above three messages. As aggressive mode exchanges less
information and features higher negotiation speed, it applies to scenarios where the requirement for
identity protection is lower. For scenarios with higher requirement for identity protection, main mode is
recommended.
Functions of IKE in IPsec
•
IKE automatically negotiates IPsec parameters such as the keys, reducing the manual configuration
complexity greatly.
•
IKE always performs DH exchange when establishing an SA, ensuring that each SA has a key with
no relation with any other key.
•
IPsec uses the sequence number, a 32-bit value in the AH or ESP header, for anti-replay. If the value
overflows, a new SA needs to be established for anti-replay, in which procedure IKE is required.
•
Identity authentication and management of peers influence IPsec deployment. A large-scale IPsec
deployment needs the support of certificate authorities (CAs) or other institutes which manage
identity data centrally.
•
IKE allows for end-to-end dynamic authentication.
