Configuring tcp proxy, Configuration task list, Figure 4 – H3C Technologies H3C SecPath F1000-E User Manual
Page 645
3
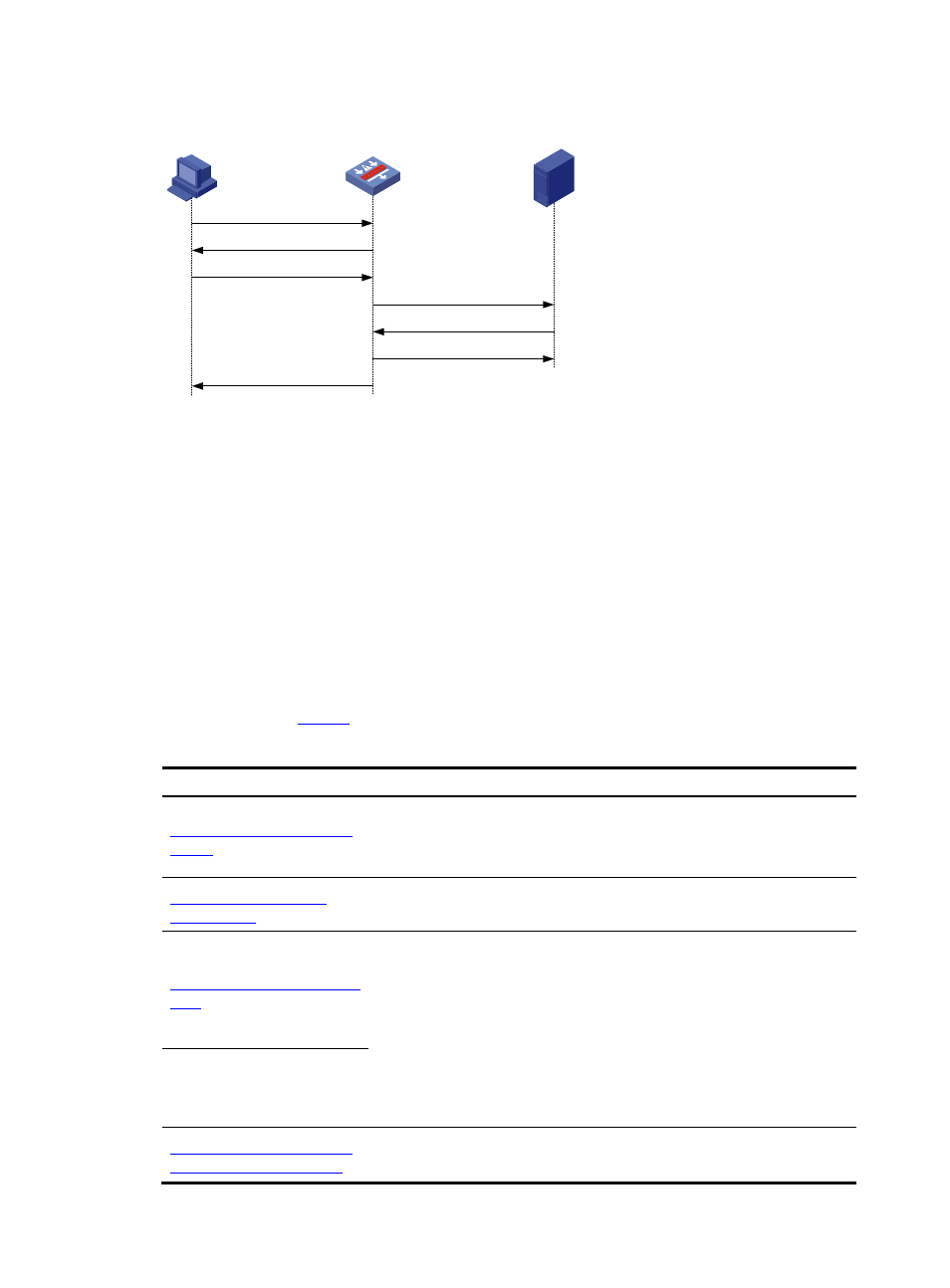
Figure 4 Data exchange process of bidirectional proxy
TCP client
TCP proxy
TCP server
1) SYN
2) SYN ACK (win=0)
4) SYN
5) SYN ACK (win=n)
7) ACK (win=n)
3) ACK
6) ACK
After receiving a SYN message from a client to the protected server (such a message matches a protected
IP address entry), the TCP proxy sends back a SYN ACK message with the window size being 0 on
behalf of the server. If the client is legitimate, the TCP proxy will receive an ACK message, and then sets
up a connection between itself and the server through a three-way handshake on behalf of the client.
As two TCP connections are established, different sequence numbers are used. They are translated by the
TCP proxy for data exchange between the client and the server.
Configuring TCP Proxy
Configuration Task List
Perform the tasks in
to configure TCP proxy.
Table 1 TCP proxy configuration task list
Task
Remarks
Performing Global TCP Proxy
Setting
Optional
The configuration is effect on all security zones.
By default, bidirectional proxy is used.
Enabling TCP Proxy for a
Security Zone
Required
By default, the TCP proxy feature is disabled globally.
Adding a Protected IP Address
Entry
Configure the Device to
Automatically Add a Protected
IP address Entry
At least one method is required.
You can add protected IP address entries by either of the methods:
•
Static: Add entries manually. By default, no such entries are configured in
the system.
•
Dynamic: Select Intrusion Detection > Traffic Abnormality > SYN
Flood, and then select the Add protected IP entry to TCP Proxy
check box. After the configuration, the TCP proxy-enabled device will
automatically add protected IP address entries when detecting SYN flood
attacks. For more information, see Intrusion Detection Configuration.
Displaying Information About
Protected IP Address Entries
Optional
You can view information about all protected IP address entries.
