Network requirements – H3C Technologies H3C SecPath F1000-E User Manual
Page 630
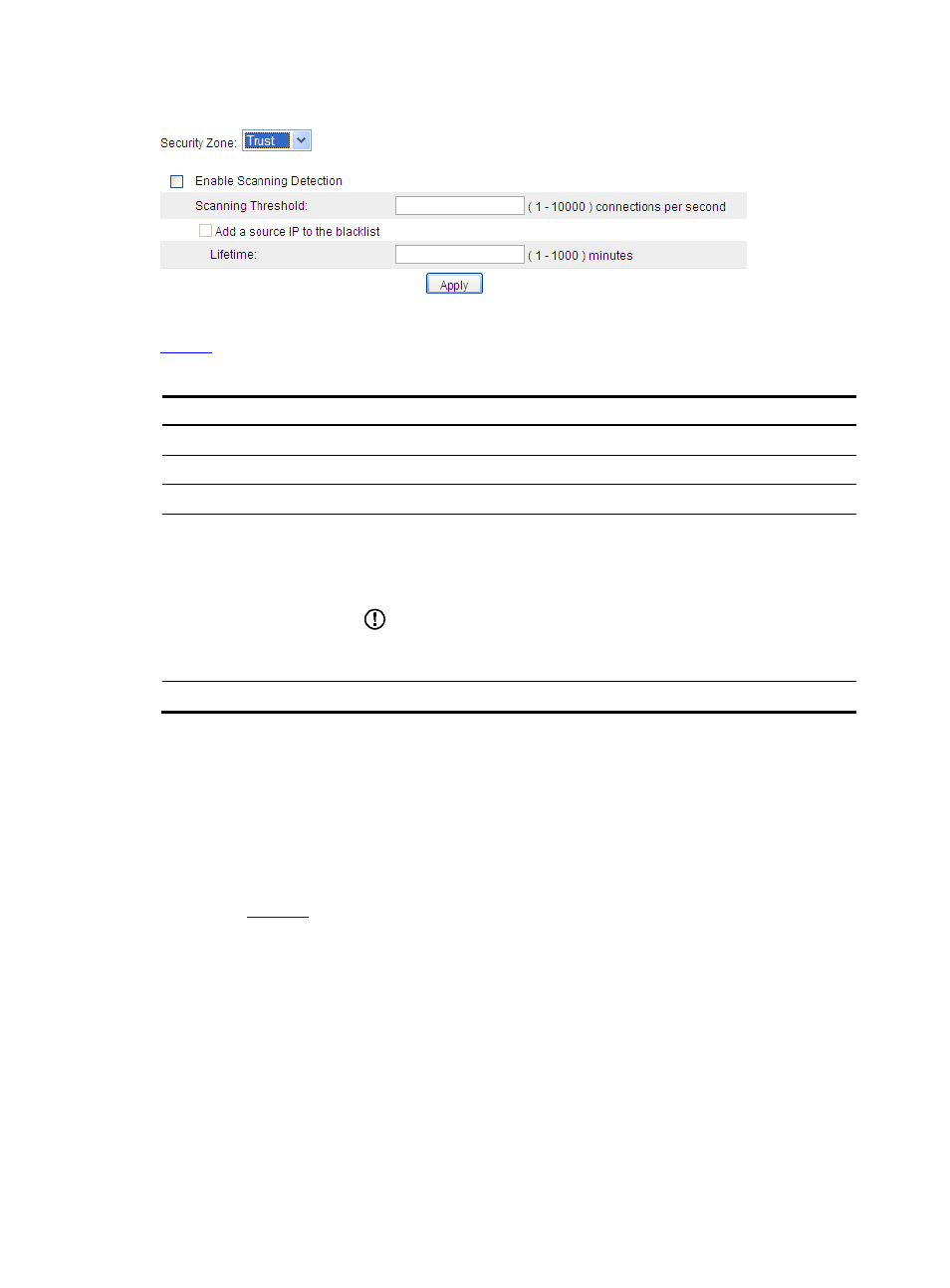
10
Figure 10 Scanning detection configuration page
lists the scanning detection configuration items.
Table 6 Scanning detection configuration items
Item
Description
Security Zone
Select a security zone to perform scanning detection configuration for it.
Enable Scanning Detection
Select this option to enable scanning detection for the security zone.
Scanning Threshold
Set the maximum connection rate for a source IP address.
Add a source IP to the
blacklist
Select this option to allow the system to blacklist a suspicious source IP
address.
If this option is selected, you can then set the lifetime of the blacklisted source IP
addresses.
IMPORTANT:
Only when the blacklist feature is enabled, can the scanning detection function
blacklist a suspect and discard subsequent packets from the suspect.
Lifetime
Set the lifetime of the blacklist entry.
Traffic Abnormality Detection Configuration
Example
Network requirements
As shown in
, the internal network is the trusted zone, the subnet where the internal servers are
located is the demilitarized zone (DMZ), and the external network is the untrusted zone. Configure the
device so that the device:
•
Protects the internal network against scanning attacks from the external network.
•
Limits the number of connections initiated by an internal host.
•
Limits the number of connections to the internal server.
•
Protects the internal server against SYN flood attacks from the external network.
To meet these requirements, you need to perform these configurations on the device:
•
Configure scanning detection for the untrusted zone, enable the function to add entries to the
blacklist, and set the scanning threshold to 4500 connections per second.
