Brocade Mobility Access Point System Reference Guide (Supporting software release 5.5.0.0 and later) User Manual
Page 356
346
Brocade Mobility Access Point System Reference Guide
53-1003100-01
5
Select Add to create a new NAT policy that can be applied to a profile. Select Edit to modify or
override the attributes of a existing policy or select Delete to remove obsolete NAT policies from the
list of those available to a profile.
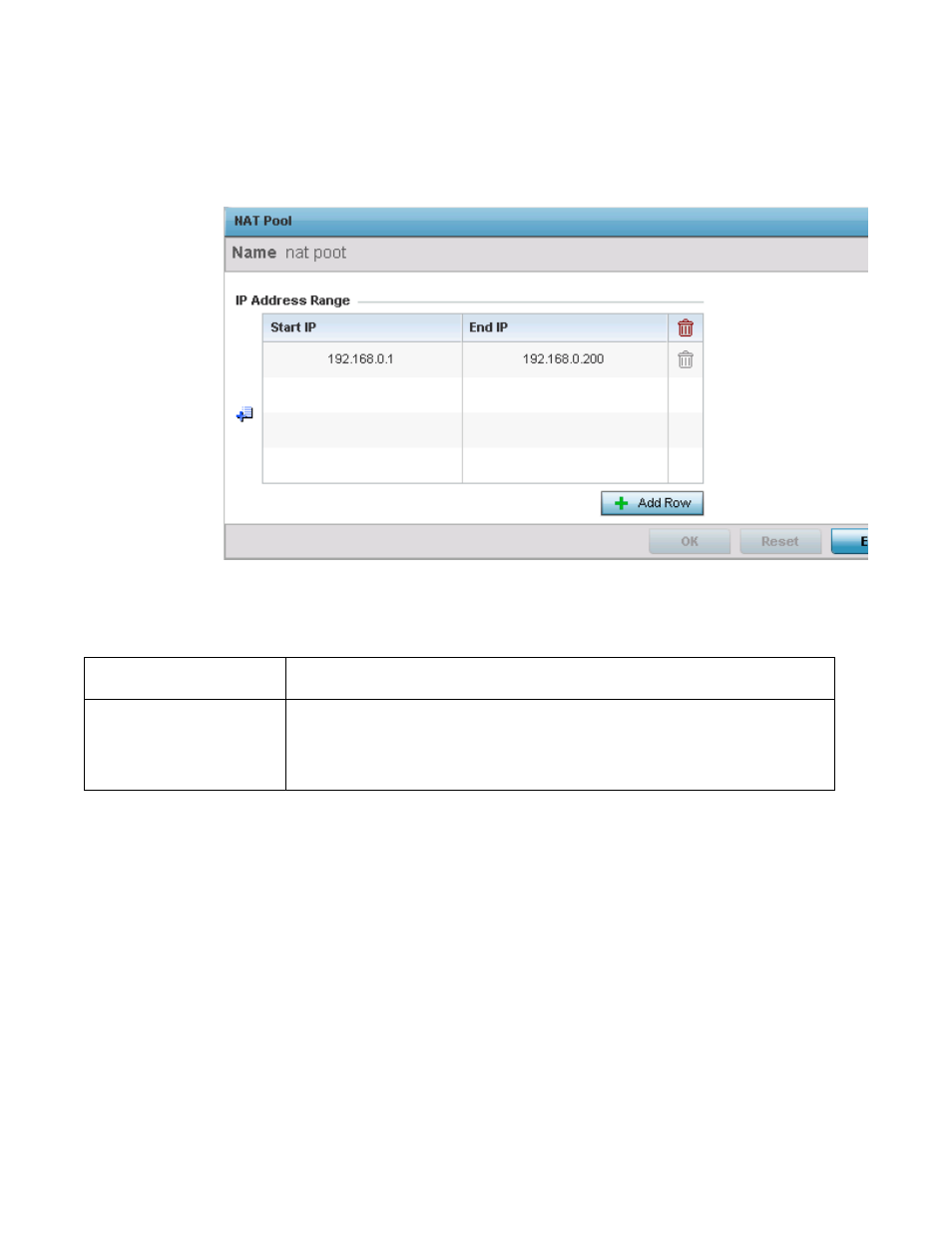
FIGURE 187
Device Overrides - Security - NAT Pool screen
If adding a new NAT policy or editing the configuration of an existing policy, define the following
parameters:
Select the + Add Row button as needed to append additional rows to the IP Address Range table.
Select OK to save the changes or overrides made to the profile’s NAT Pool configuration. Select
Reset to revert to the last saved configuration.
Select the Static NAT tab. The Source tab displays by default.
The Source tab displays existing static NAT configurations. Existing static NAT configurations are
not editable, but new configurations can be added or existing ones deleted as they become
obsolete.
Static NAT creates a permanent, one-to-one mapping between an address on an internal network
and a perimeter or external network. To share a Web server on a perimeter interface with the
Internet, use static address translation to map the actual address to a registered IP address. Static
address translation hides the actual address of the server from users on insecure interfaces.
Casual access by unauthorized users becomes much more difficult. Static NAT requires a
dedicated address on the outside network for each host.
Name
If adding a new NAT policy, provide a name to help distinguish it from others with similar
configurations. The length cannot exceed 64 characters.
IP Address Range
Define a range of IP addresses hidden from the public Internet. NAT modifies network address
information in the defined IP range while in transit across a traffic routing device. NAT only
provides IP address translation and does not provide a firewall. A branch deployment with NAT by
itself will not block traffic from being potentially routed through a NAT device. Consequently, NAT
should be deployed with a stateful firewall.
