Brocade Mobility Access Point System Reference Guide (Supporting software release 5.5.0.0 and later) User Manual
Page 174
164
Brocade Mobility Access Point System Reference Guide
53-1003100-01
5
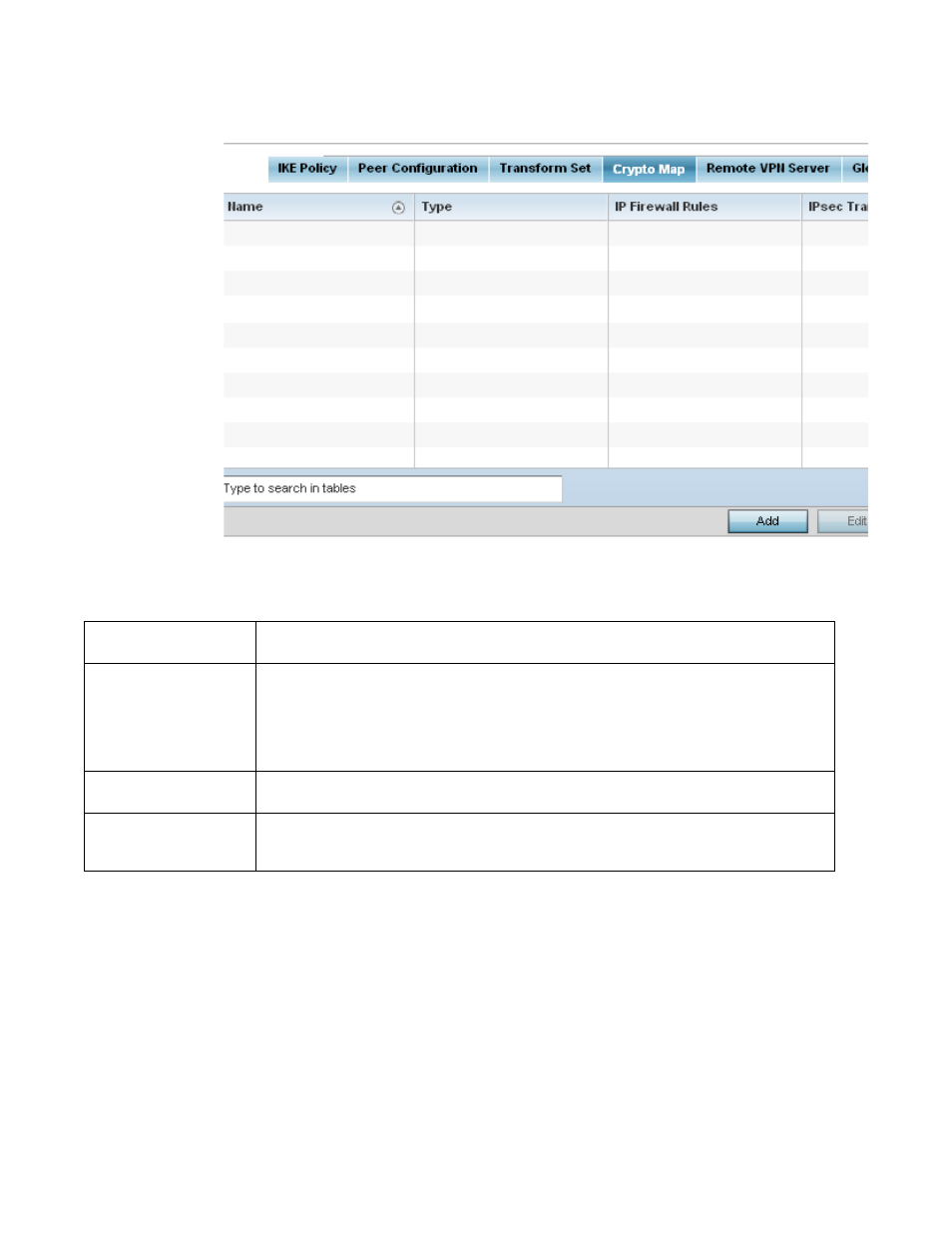
FIGURE 66
Profile Security - VPN Crypto Map tab
21. Review the following Crypto Map configuration parameters to assess their relevance:
22. If requiring a new crypto map configuration, select the Add button. If updating the configuration
of an existing crypto map, select it from amongst those available and select the Edit button.
23. If adding a new crypto map, assign it a name up to 32 characters as a unique identifier. Select
the Continue button to proceed to the VPN Crypto Map screen.
Name
Lists the 32 character maximum name assigned for each crypto map upon creation. This name cannot
be modified as part of the edit process.
Type
Displays the site-to-site-manual, site-to-site-auto or remote VPN configuration defined for each listed
crypto map configuration. With site-to-site deployments, an IPSEC Tunnel is deployed between two
gateways, each at the edge of two different remote networks. With remote VPN, an access point
located at remote branch defines a tunnel with a security gateway. This facilitates the endpoints in the
branch office to communicate with the destination endpoints (behind the security gateway) in a secure
manner.
IP Firewall Rules
Lists the IP firewall rules defined for each displayed crypto map configuration. Each firewall policy
contains a unique set of access/deny permissions applied to the VPN tunnel and its peer connection.
IPSec Transform Set
Displays the transform set (encryption and has algorithms) applied to each listed crypto map
configuration. Thus, each crypto map can be customized with its own data protection and peer
authentication schemes.
