Overriding a profile’s nat configuration – Brocade Mobility Access Point System Reference Guide (Supporting software release 5.5.0.0 and later) User Manual
Page 354
344
Brocade Mobility Access Point System Reference Guide
53-1003100-01
5
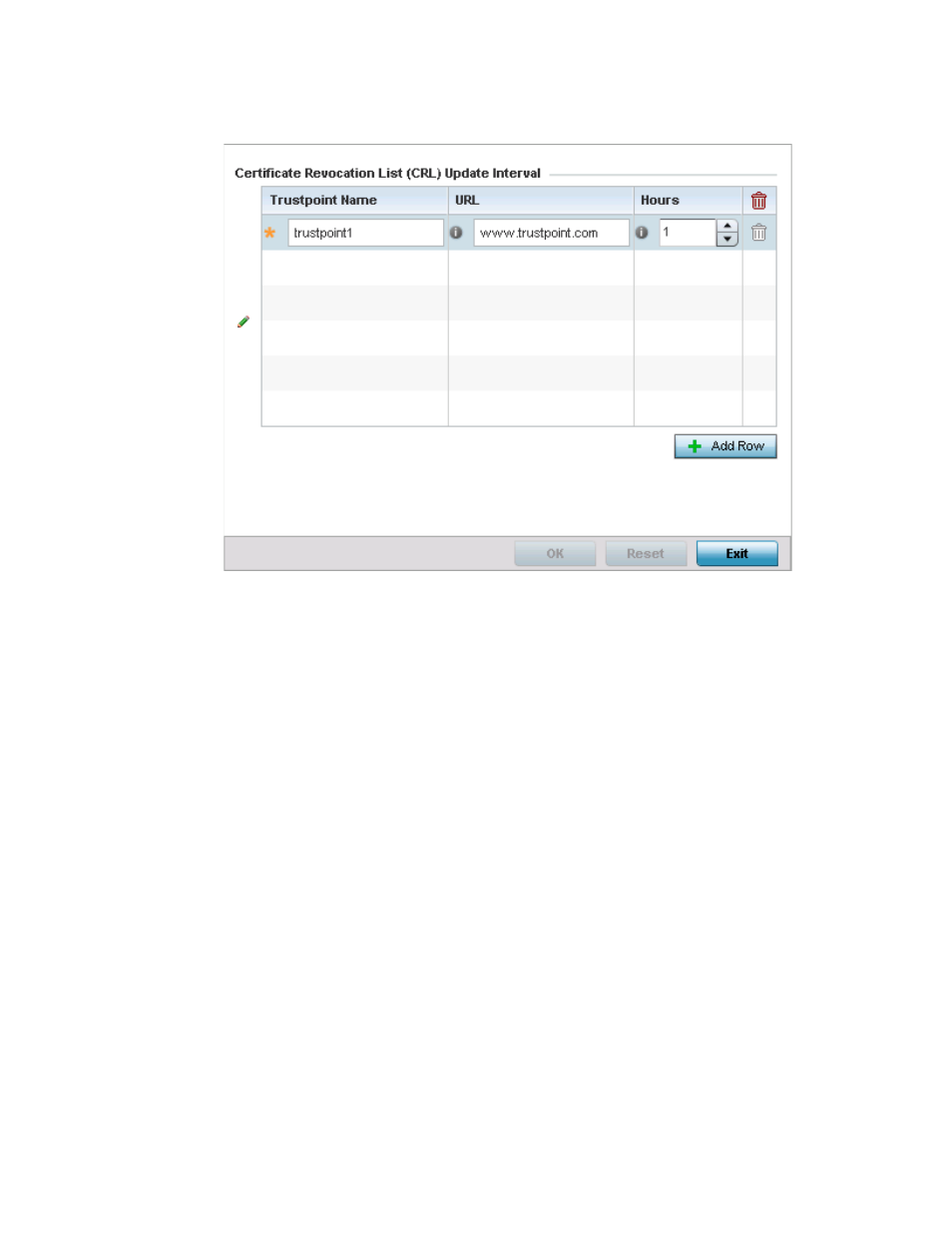
FIGURE 185
Device Overrides - Certificate Revocation screen
Select the + Add Row button to add a column within the Certificate Revocation List (CRL) Update
Interval table to quarantine certificates from use in the network.
Additionally, a certificate can be placed on hold for a user defined period. If, for instance, a private
key was found and nobody had access to it, its status could be reinstated.
Provide the name of the trustpoint in question within the Trustpoint Name field. The name cannot
exceed 32 characters.
Enter the resource ensuring the trustpoint’s legitimacy within the URL field.
Use the spinner control within the Hours field to specify an interval (in hours) after which the
access point copies a CRL file from an external server and associates it with a trustpoint.
Select OK to save the changes and overrides made within the Certificate Revocation screen. Select
Reset to revert to the last saved configuration.
Overriding a Profile’s NAT Configuration
Overriding a Security Configuration
Network Address Translation (NAT) is a technique to modify network address information within IP
packet headers in transit across a traffic routing device. This enables mapping one IP address to
another to protect network address credentials. With typical deployments, NAT is used as an IP
masquerading technique to hide private IP addresses behind a single, public facing, IP address.
NAT is a process of modifying network address information in IP packet headers while in transit
across a traffic routing device for the purpose of remapping one IP address to another. In most
deployments, NAT is used in conjunction with IP masquerading which hides RFC1918 private IP
addresses behind a single public IP address.
