Captive portal deployment considerations – Brocade Mobility RFS Controller System Reference Guide (Supporting software release 5.5.0.0 and later) User Manual
Page 636
624
Brocade Mobility RFS Controller System Reference Guide
53-1003099-01
11
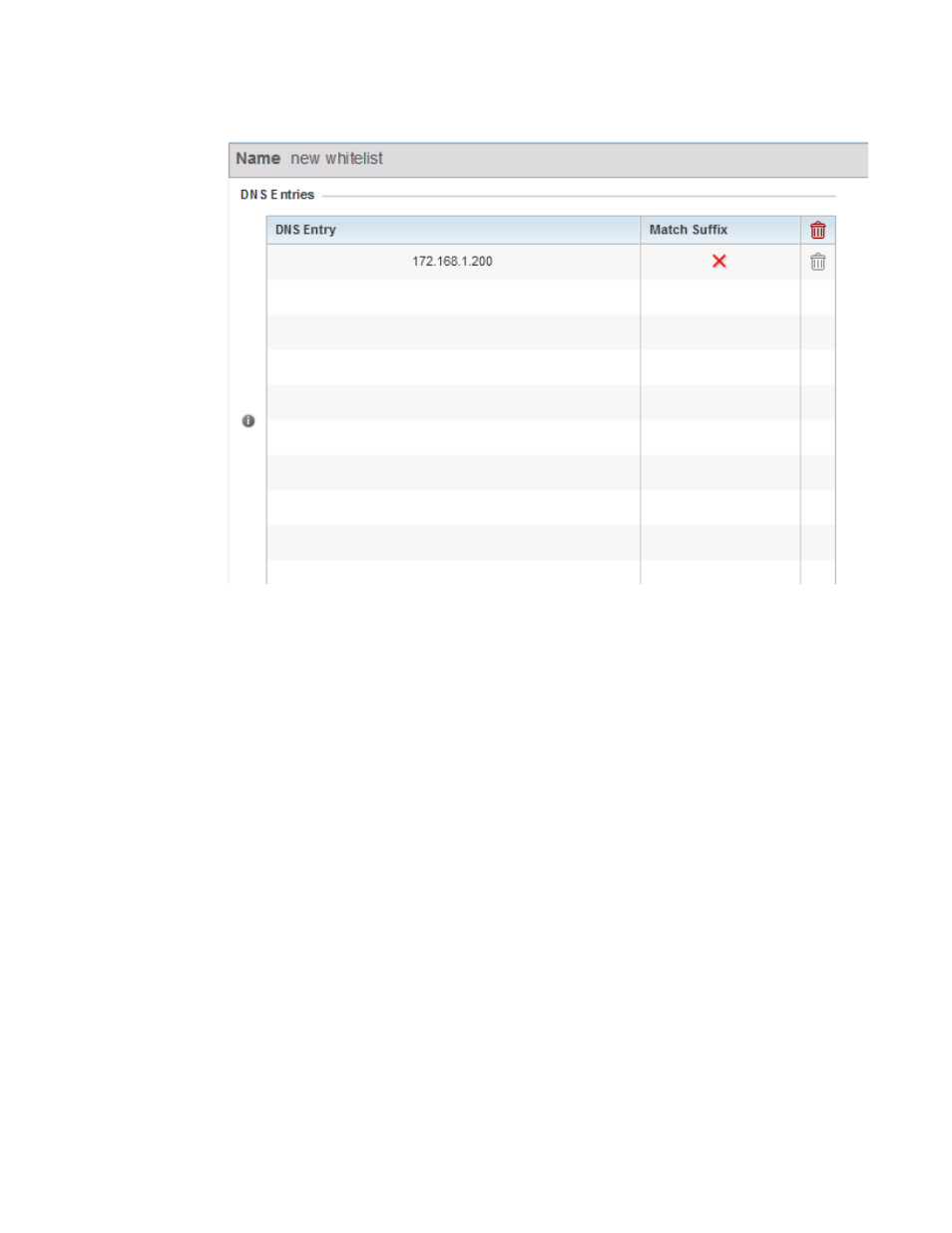
FIGURE 7
Captive Portal Whitelist screen
b. Provide a numerical IP address or Hostname within the DNS Entry parameter for each
destination IP address or host included in the Whitelist.
c. Use the Match Suffix parameter to match any hostname or domain name as a suffix. The
default setting is disabled.
d. If necessary, select the radio button of an existing Whitelist entry and select the - Delete
icon to remove the entry from the Whitelist.
Captive Portal Deployment Considerations
Before defining a captive portal configuration, refer to the following deployment guidelines to
ensure the configuration is optimally effective:
•
The architecture should consider the number of wireless clients allowed and the services
provided. Each topology has benefits and disadvantages which should taken into
consideration to meet each deployment's requirements.
•
Captive portal authentication uses secure HTTPS to protect user credentials, but doesn’t
typically provide encryption for user data once they have been authenticated. For private
access applications, Brocade recommends WPA2 (with a strong passphrase) be enabled to
provide strong encryption.
•
Brocade recommends guest user traffic be assigned a dedicated VLAN, separate from other
internal networks.
•
Guest access configurations should include firewall policies to ensure logical separation is
provided between guest and internal networks so internal networks and hosts are not
reachable from guest devices.
