6 cache data integrity – NEC Network Controller uPD98502 User Manual
Page 174
CHAPTER 2 V
R
4120A
174
Preliminary User’s Manual S15543EJ1V0UM
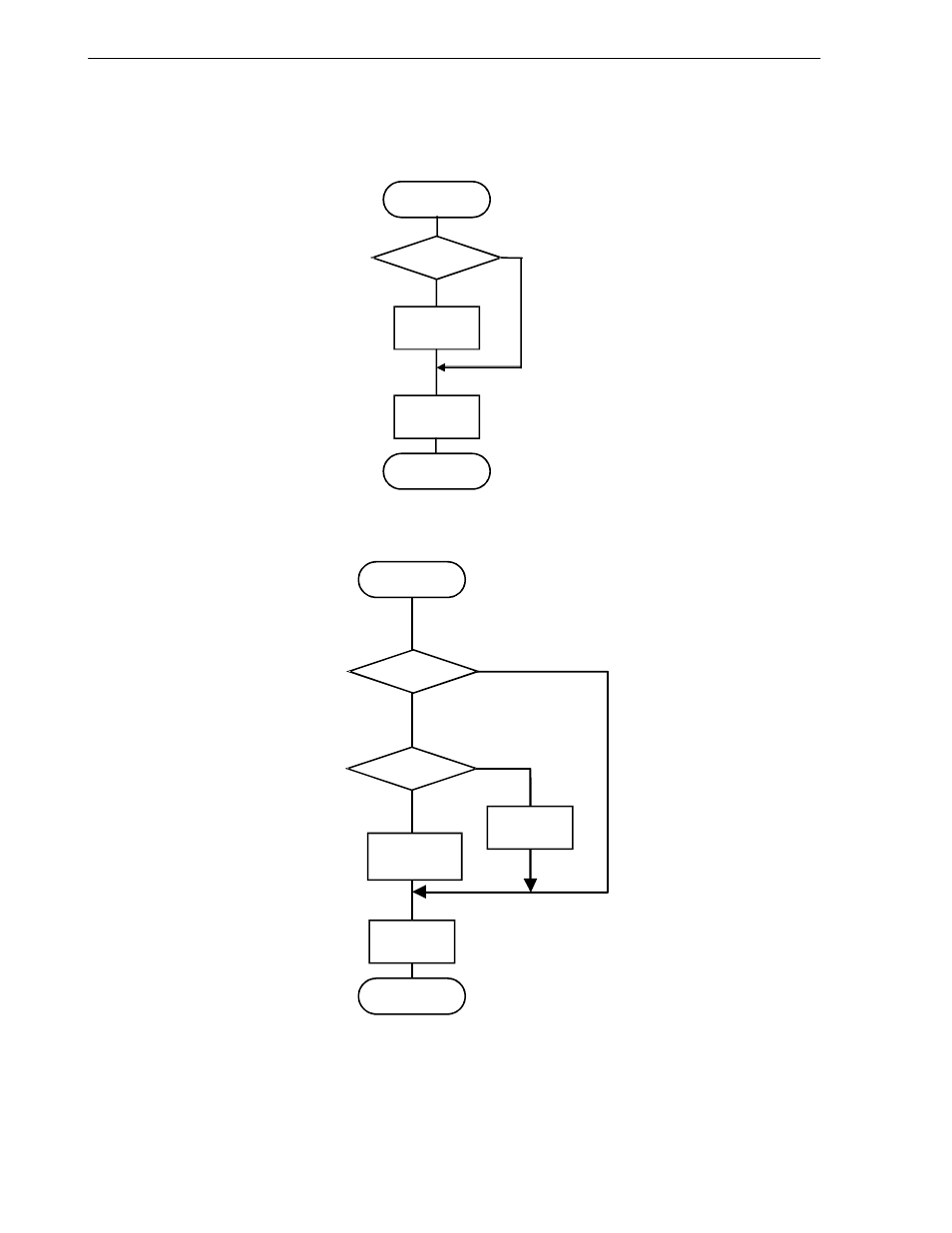
2.7.6 Cache data integrity
Figures 2-72 to 2-86 shows checking operations for various cache accesses.
Figure 2-72. Data Check Flow on Instruction Fetch
Start
Data Fetch
END
Tag Check
Refill (See
Figure 2-85)
Hit
Miss
Figure 2-73. Data Check Flow on Load Operations
Start
Write-back and
Refill (see
Data Load to
Register
END
Hit
V = 0 (invalid)
or
W = 0 (clean)
Miss or
Invalid
V bit, W bit
V = 1 (valid) and
W = 1 (dirty)
Refill (see
Figure 2-85)
Tag Check
Figure 2-86)
