Configuring arp attack defense, Arp attack defense configuration task list – H3C Technologies H3C S3600 Series Switches User Manual
Page 605
2-4
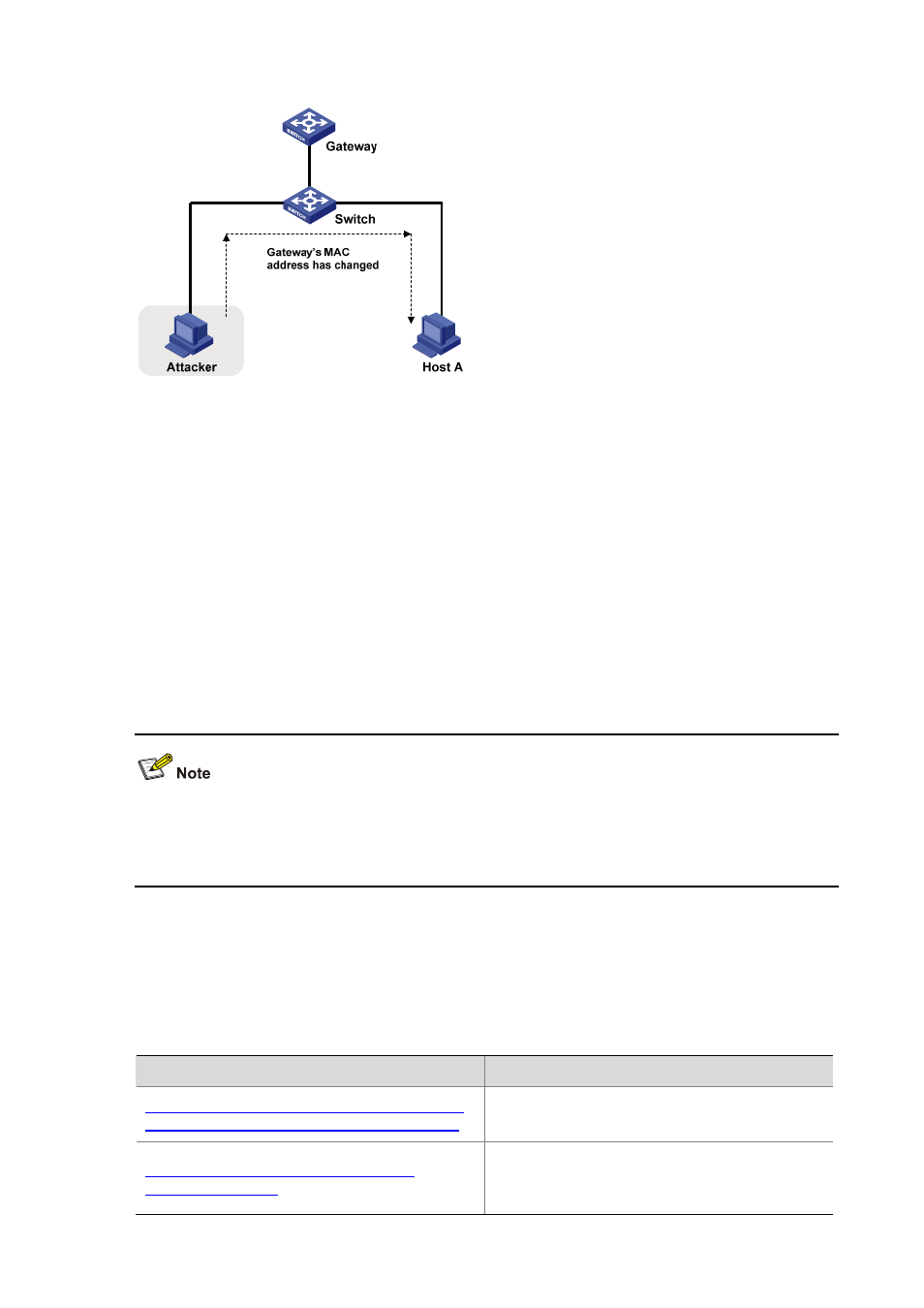
Figure 2-2 Gateway spoofing attack
To prevent gateway spoofing attacks, an S3600 series Ethernet switch can work as an access device
(usually with the upstream port connected to the gateway and the downstream ports connected to hosts)
and filter ARP packets based on the gateway’s address.
z
To filter APR attack packets arriving on a downstream port, you can bind the gateway’s IP address
to the downstream port (directly connected to hosts) of the switch. After that, the port will discard
ARP packets with the gateway’s IP address as the sender IP address, and permit other ARP
packets to pass.
z
To filter ARP attack packets arriving on the upstream port, you can bind the IP and MAC addresses
of the gateway to the cascaded port or upstream port of the access switch. After that, the port will
discard ARP packets with the sender IP address as the gateway’s IP address but with the sender
MAC address different from the gateway’s MAC address, and permit other ARP packets to pass.
An ARP trusted port has higher priority comparing with support for ARP packet filtering based on
gateway's address. That is, if you configure a cascaded port or an upstream port as an ARP trusted port,
the gateway's IP and MAC addresses configured on the port are ineffective.
Configuring ARP Attack Defense
ARP Attack Defense Configuration Task List
Complete the following tasks to configure ARP attack defense:
Task
Remarks
Configuring the Maximum Number of Dynamic
ARP Entries that a VLAN Interface Can Learn
Optional
The switch serves as a gateway.
Configuring ARP Source MAC Address
Consistency Check
Optional
The switch serves as a gateway or an access
device.
