How organizational policies are authenticated, Create a user security policy – Adobe Acrobat 9 PRO Extended User Manual
Page 251
245
USING ACROBAT 9 PRO EXTENDED
Security
Last updated 9/30/2011
•
User policies are policies created and applied by individuals. If you apply the same security settings to numerous
documents, you can save time by creating a user policy. Then, apply the user policy to documents. User policies for
passwords and public key certificates are stored on your local computer. With access to Adobe LiveCycle Rights
Management ES, you can create a user policy that’s stored on Adobe LiveCycle Rights Management ES. That policy
is available only to you.
How organizational policies are authenticated
In addition to reusing security settings, policies stored on Adobe LiveCycle Rights Management ES enable you to
expire and revoke documents (no matter how many copies were created or distributed). You can also maintain
accountability by auditing users who open protected documents.
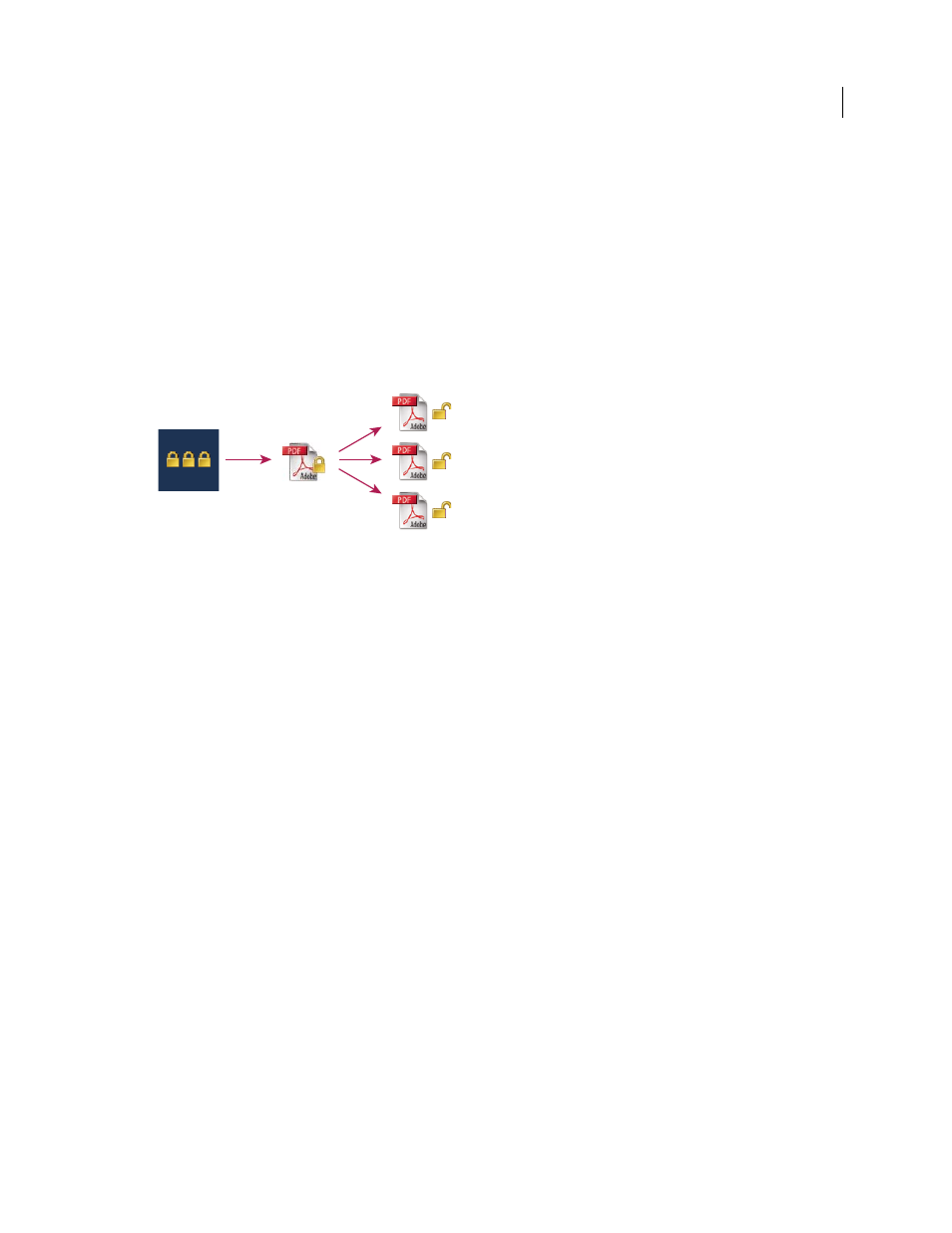
Security policies
A. Policies are stored on server. B. Policies are applied to a PDF. C. Users can open, edit, and print a document only if permitted by policy.
Setting up server-based security policies involves four main stages:
Configure the Adobe LiveCycle Rights Management ES
The system administrator of your company or group usually
configures Adobe LiveCycle Rights Management ES, manages accounts, and sets up organizational policies. For more
information on configuring Adobe LiveCycle Rights Management ES, see the Adobe website.
Publish a document with a security policy
An author creates a PDF and applies a policy stored on Adobe LiveCycle
Rights Management ES to the PDF. The server generates a license and unique encryption key for the PDF. Acrobat
embeds the license in the PDF and encrypts it using the encryption key. The author or administrator can use this
license to track and audit the PDF.
View a document with a policy applied
When users try to open the secure PDF in Acrobat 9 (or Reader 9), they must
authenticate their identities. If the user is granted access to the PDF, the PDF is decrypted and opens with whatever
permissions are specified in the policy.
Administer events and modify access
By logging in to an Adobe LiveCycle Rights Management ES account, the author
or administrator can track events and change access to policy-secured PDFs. Administrators can view all PDF and
system events, modify configuration settings, and change access to policy-secured PDFs.
Create a user security policy
User policies can use passwords, certificates, or Adobe LiveCycle Rights Management ES to authenticate documents.
The policies for password and certificate security can be stored on a local computer. Security policies created by using
Adobe LiveCycle Rights Management ES are stored on a server, so you can audit actions and change security settings
dynamically. You can use Adobe LiveCycle Rights Management ES if your company has licensed the software and
made it available to you.
A
B
C
