Westermo RedFox Series User Manual
Page 779
Westermo OS Management Guide
Version 4.17.0-0
the most common use is to encapsulate IP packets, creating an IP over IP tunnel.
WeOS only supports the encapsulation of IP packets in GRE.
GRE works by adding a special (GRE) header in front of the encapsulated packet
containing a checksum
, payload type (0x800 for IP) and some flags. The GRE
header is preceded by an outer IP header used to route the packet between the
tunnelling endpoints.
The GRE protocol is stateless. It does not provide any security features at all; it
lacks encryption and authentication, and it does not detect lost packets, replay
attacks or other spoof attacks.
You can add security, if needed, by using GRE within an IPsec VPN tunnel (
) or by using some kind of secure protocol (such as HTTPS or SSH) for the
data routed through the tunnel.
GRE tunnels are configured in two steps. First you need to define the tunnel
with its endpoints and other related settings (described further
). By configuring the tunnel, a new (GRE) network interface is created
automatically. The second step is to configure the created GRE interface. See
for information about configuring interfaces, including the GRE inter-
faces.
34.1.2
Defining GRE tunnel endpoints
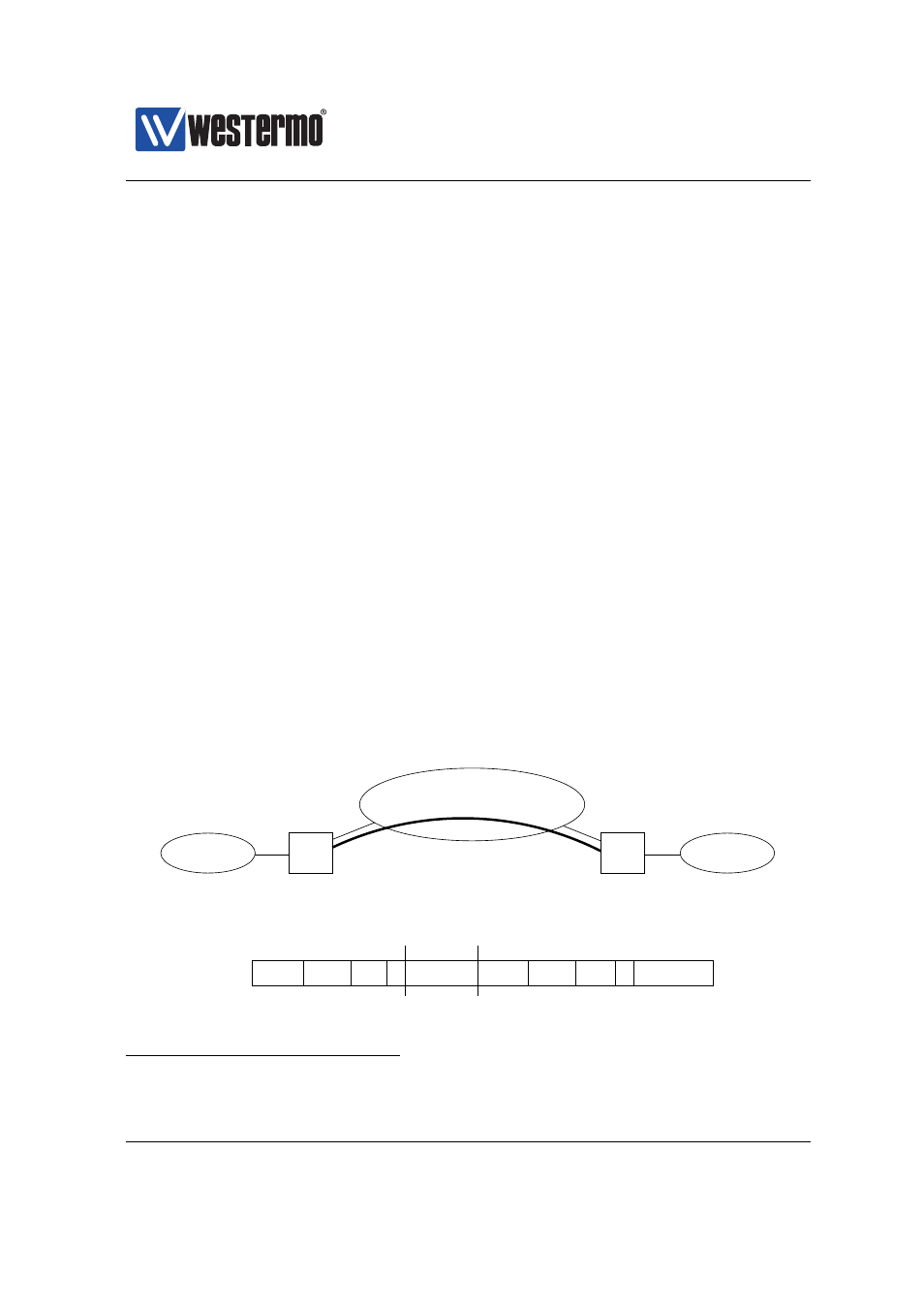
IP−Src
Outer IP Hdr
IP−Dst
TTL ...
GRE Hdr
...
IP−Dst IP−Src TTL
...
Data
...
GRE Payload (Inner IP packet)
Tunnel Endpoint
IP Address e.f.g.h
Tunnel Endpoint
IP Address a.b.c.d
Local
Subnet−A
Alice
Local
Subnet−B
Bob
Internet
Figure 34.1: GRE tunnel example.
1
The GRE checksum is optional. WeOS does not include a checksum in transmitted GRE packets
➞ 2015 Westermo Teleindustri AB
779
