Security configuration deployment – Brocade Network Advisor SAN User Manual v12.3.0 User Manual
Page 714
662
Brocade Network Advisor SAN User Manual
53-1003154-01
Security configuration deployment
17
Security configuration deployment
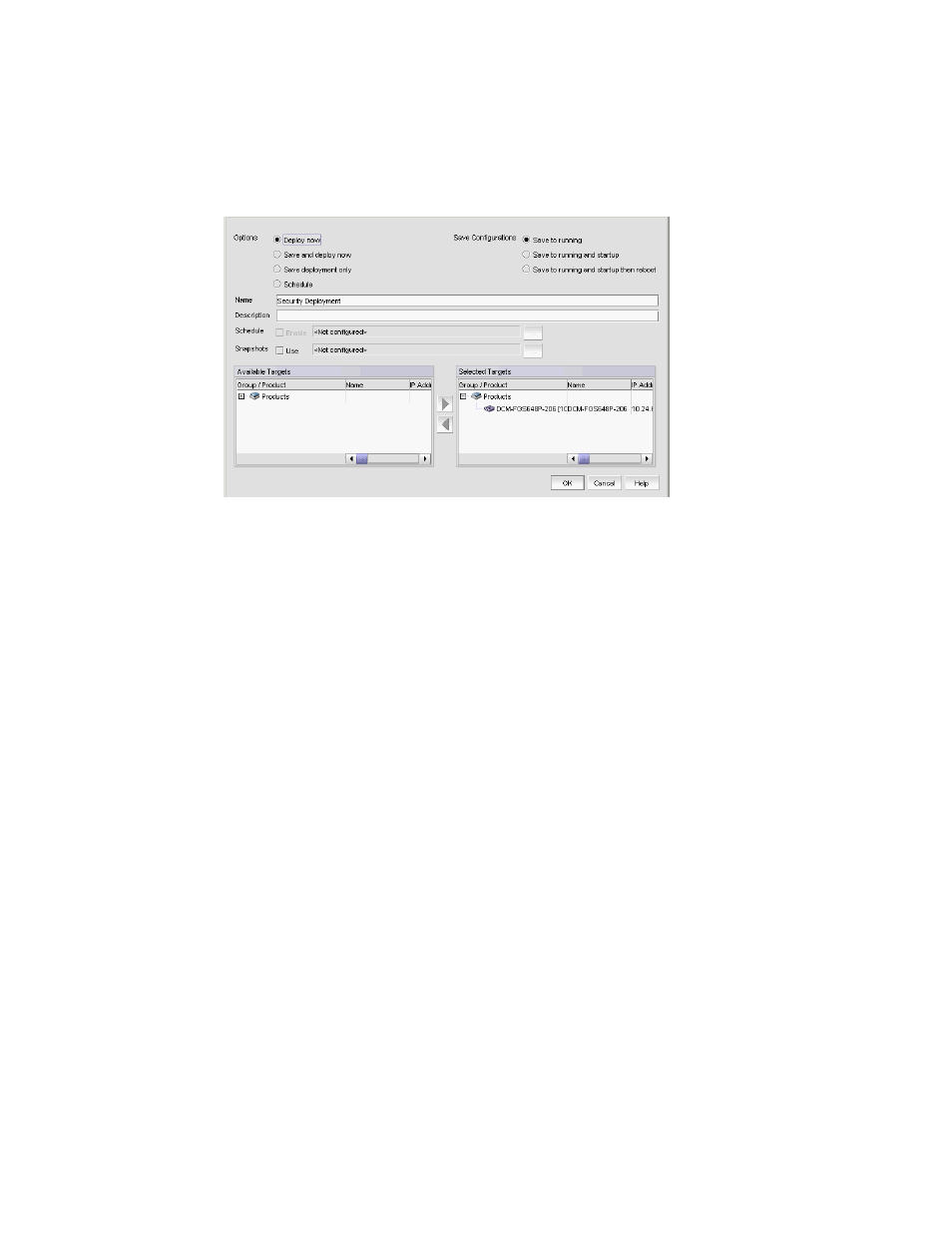
shows the standard interface used to deploy security configurations.
FIGURE 256
Deploy to Product/Ports dialog box
Before you can deploy a security configuration, you must create the security configuration. For
step-by-step instructions, refer to the following sections:
Security Management enables you to configure, persist, and manage a security configuration as a
“deployment configuration object”. A deployment configuration object is comprised of the following
parts:
•
Security configuration (Layer 2 ACL)
•
Target information
•
Deployment option
•
Persistence option
•
Scheduling option
•
Snapshot option
To create a deployment configuration object, you must save the deployment. Once you create a
deployment configuration object, you can access the security configuration from the Deployment
manager. For more information about the Deployment manager, refer to
