Wireless intrusion detection – Brocade Mobility RFS7000-GR Controller System Reference Guide (Supporting software release 4.1.0.0-040GR and later) User Manual
Page 537
Brocade Mobility RFS7000-GR Controller System Reference Guide
523
53-1001944-01
Wireless IDS
C
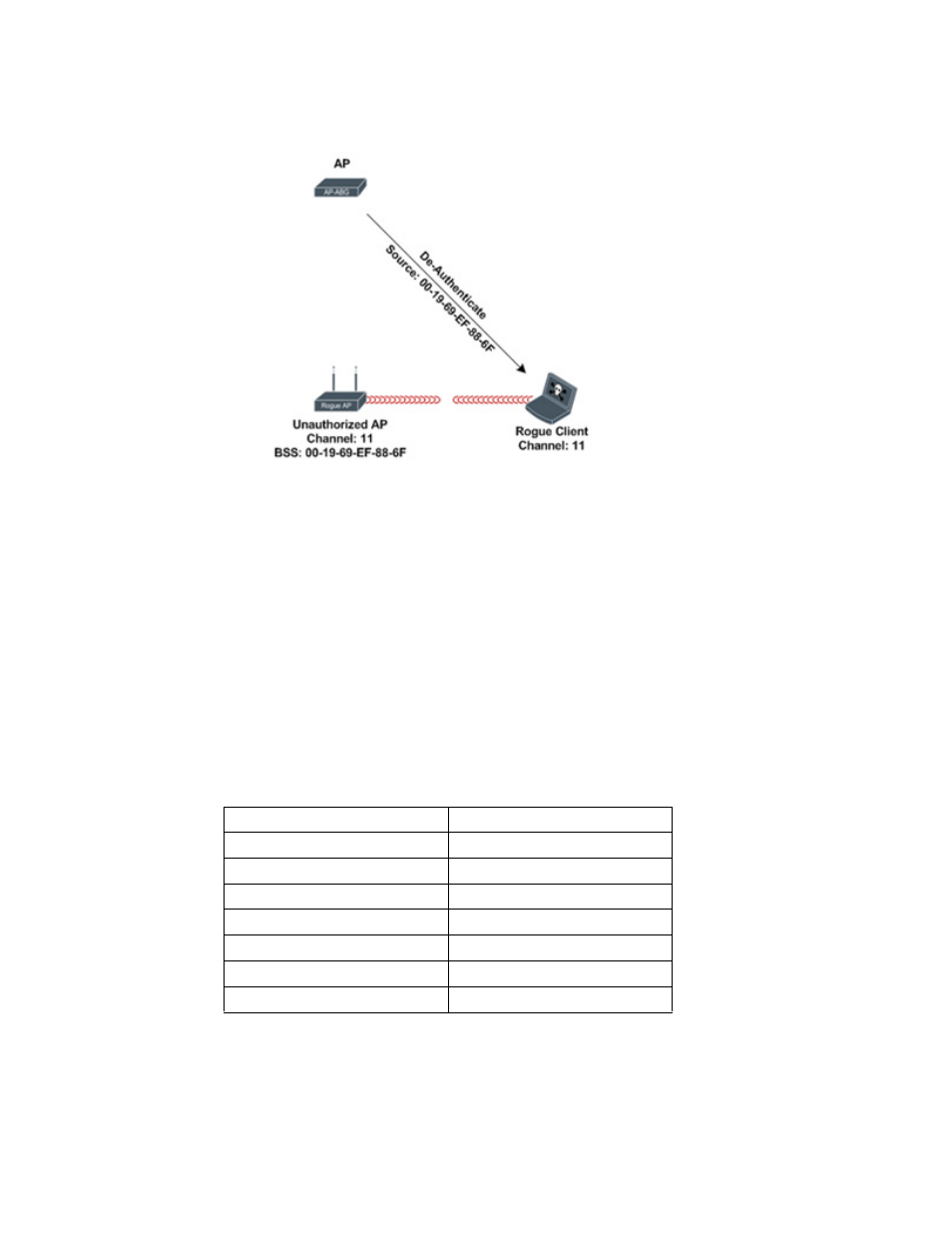
Unauthorized AP containment can be performed by adding APs in the unauthorized AP list to a
containment list. Once added the Brocade Mobility RFS7000-GR Controller will co-ordinate
mitigation using Brocade Mobility 7131N-FGR Access Points by sending broadcast 802.11
de-authentication frames to each MU spoofing the unauthorized APs MAC address. Depending on
the site, one or more Brocade Mobility 7131N-FGR Access Point can be used to perform
containment and the results will vary depending on the MU driver.
Wireless Intrusion Detection
A Brocade Mobility RFS7000-GR Controller can also be configured to monitor and alert
administrators about unauthorized attempts to access the WLAN. Unauthorized attempts are
generally accompanied by malicious MUs attempting to identify network vulnerabilities.
Integrated intrusion detection can be enabled on the RF Switch to provide monitoring for basic
attacks without the need of dedicated IPS system or monitoring APs. When intrusion violations
occur and a configured threshold is exceeded, the RF Switch generates an alarm and mitigates by
blacklisting the MU for a definable length of time.
Excessive Probes
TKIP Countermeasures
Excessive Association
Invalid Frame Length
Excessive Disassociation
Excessive EAP NAKS
Excessive Authentication Failure
Invalid 802.1x Frames
Excessive Crypto Replays
Invalid Frame Type
Excessive 802.11 Replays
Beacon with Broadcast ESSID
Excessive Decryption Failures
Frames with Known Bad ESSID
Excessive Unassociated Frames
Unencrypted Traffic
