Unauthorized access point detection, Unauthorized access point containment – Brocade Mobility RFS7000-GR Controller System Reference Guide (Supporting software release 4.1.0.0-040GR and later) User Manual
Page 536
522
Brocade Mobility RFS7000-GR Controller System Reference Guide
53-1001944-01
Wireless IDS
C
Unauthorized Access Point Detection
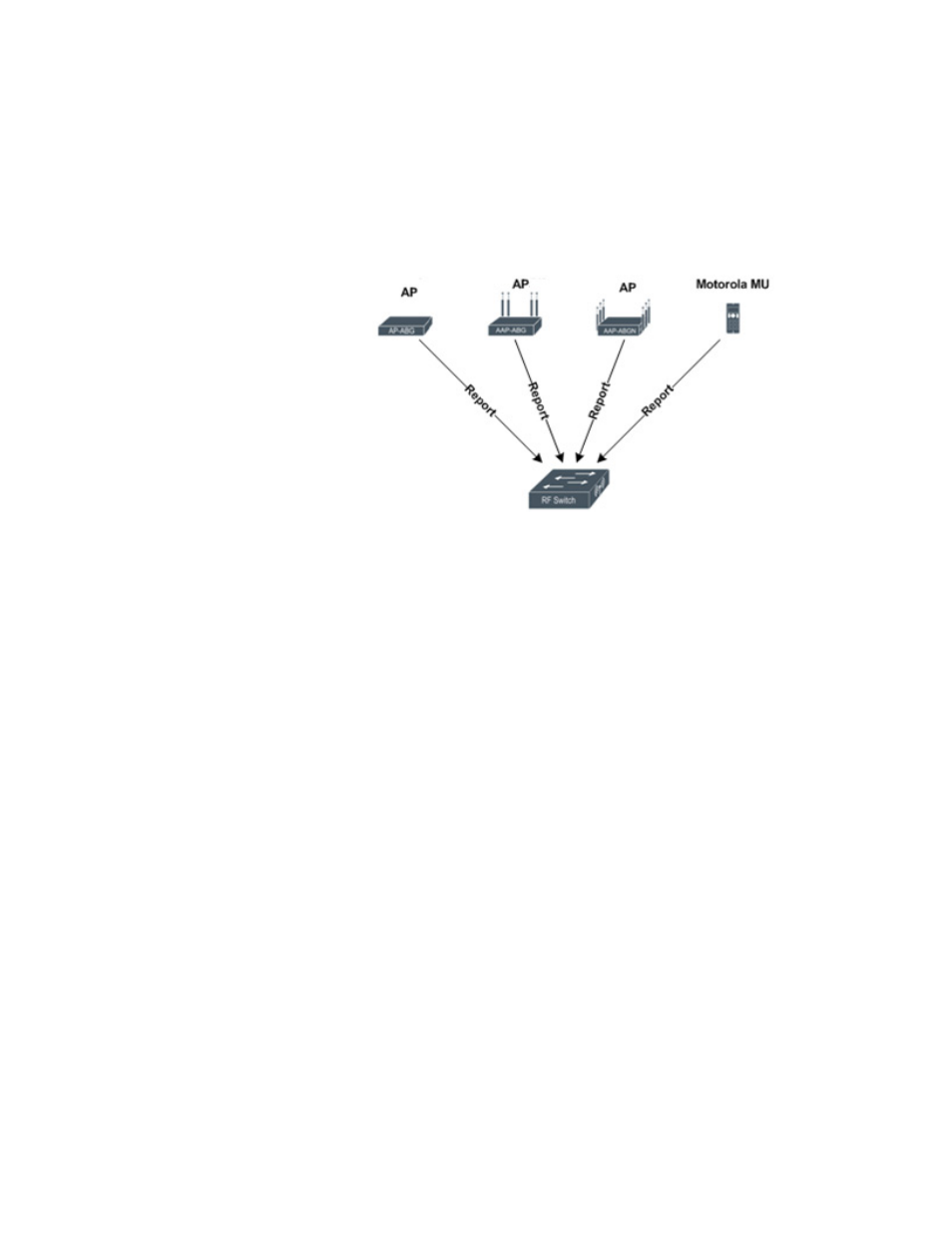
Unauthorized AP detection is a feature directly integrated into the RF switch. When enabled, it
allows the switch to monitor the RF environment for unauthorized APs. Unauthorized APs can be
reported to the RF switch from managed radios configured to perform scanning or from Brocade
Mobile Units (MUs) detecting and reporting visible APs when roaming.
Unauthorized AP scanning is supported on Brocade Mobiltiy 7131N-FGR Access Point radios
adopted by the Brocade Mobility RFS7000-GR Controller and is enabled on a per-radio bases. This
allows administrators to scan for APs throughout the network or specific areas depending on the
need. Each AP supports the following scanning modes:
•
Single Channel Scanning - Managed radios monitor the RF environment on the operating
channel while simultaneously servicing mobile users.
•
Detector - Managed radios monitors all channels in the regulatory domain but cannot service
mobile users.
When an AP is detected by a managed radio or Brocade MU, the RF switch will compare the
reported MAC address and ESSID against an allowed AP rules list. Allowed AP rules can be
configured on the RF Switch to exclude trusted or known APs which represent no threat to the
network from generating alarms. If a reported AP is matched by an allow rule, the AP is placed in an
approved list and no alarm generated. If a reported AP is not matched by a rule, the AP is placed in
an unapproved list and an alarm generated.
Detected APs remain in the an approved or unapproved list until timed out by the RF switch. APs
that continued to be detected remain in the approved or unapproved list while APs no longer
reported are removed from a list once the configured time-out period has expired.
Unauthorized Access Point Containment
APs categorized as unapproved represent a potential threat to the network. Unauthorized AP
containment can provide temporary mitigation against unauthorized APs by attempting to disrupt
communications with any associated MUs as well as attempting to prevent new MUs from
associating with the AP.
