6 xot, Xot protocol, 6 xot -8 – Nortel Networks 8000 User Manual
Page 211
Attention! The text in this document has been recognized automatically. To view the original document, you can use the "Original mode".
7 LAPB and X.25 configuration
Nortel Secure Router 8000 Series
Configuration -WAN Access
•
In round-robin mode, cyclic selection method is adopted to select the next interface or
the XOT Tunnel for every call request. For example, as shown in the above figure, if
hunt group hg1 adopts round-robin mode, calls are sent to Server A and Server B in turn.
•
The VC-number mode selects the interfaces with free logical channels in a hunt group
for every call request. For example, in the above figure, if the hunt group hg1 adopts
VC-number mode, there are 500 residual logical channels in the lines between Server A
and DCE and 300 residual logical channels in the lines between Server B and DCE. Thus,
all the first 200 calls are sent to Server A and the following calls are sent to Server A and
Server B in turn.
The X.25 hunt group supports synchronous serial interfaces and XOT Tunnels. It can
indiscriminately select the available lines between synchronous serial interfaces and XOT
Tunnels. But XOT Tunnels cannot calculate the number of logical channels; therefore it
cannot be added into a hunt group adopting VC-number selection policy.
7.1.6 XOT
XOT protocol
X.25 over TCP (XOT) is a protocol that carries X.25 packets over TCP, and implements the
interconnection of two X.25 networks through IP network. Figure 7-6 shows the practical
application environment.
The conventional X.25 protocol applies to the layer 3, namely, the network layer, of the OSI
seven-layer model, for which the LAPB protocol provides reliable data transmission link.
XOT builds a TCP tunnel connection between two X.25 networks, and the X.25 packets are
supported by TCP as data of application layer. See Figure 7-6 for the XOT typical application
diagram.
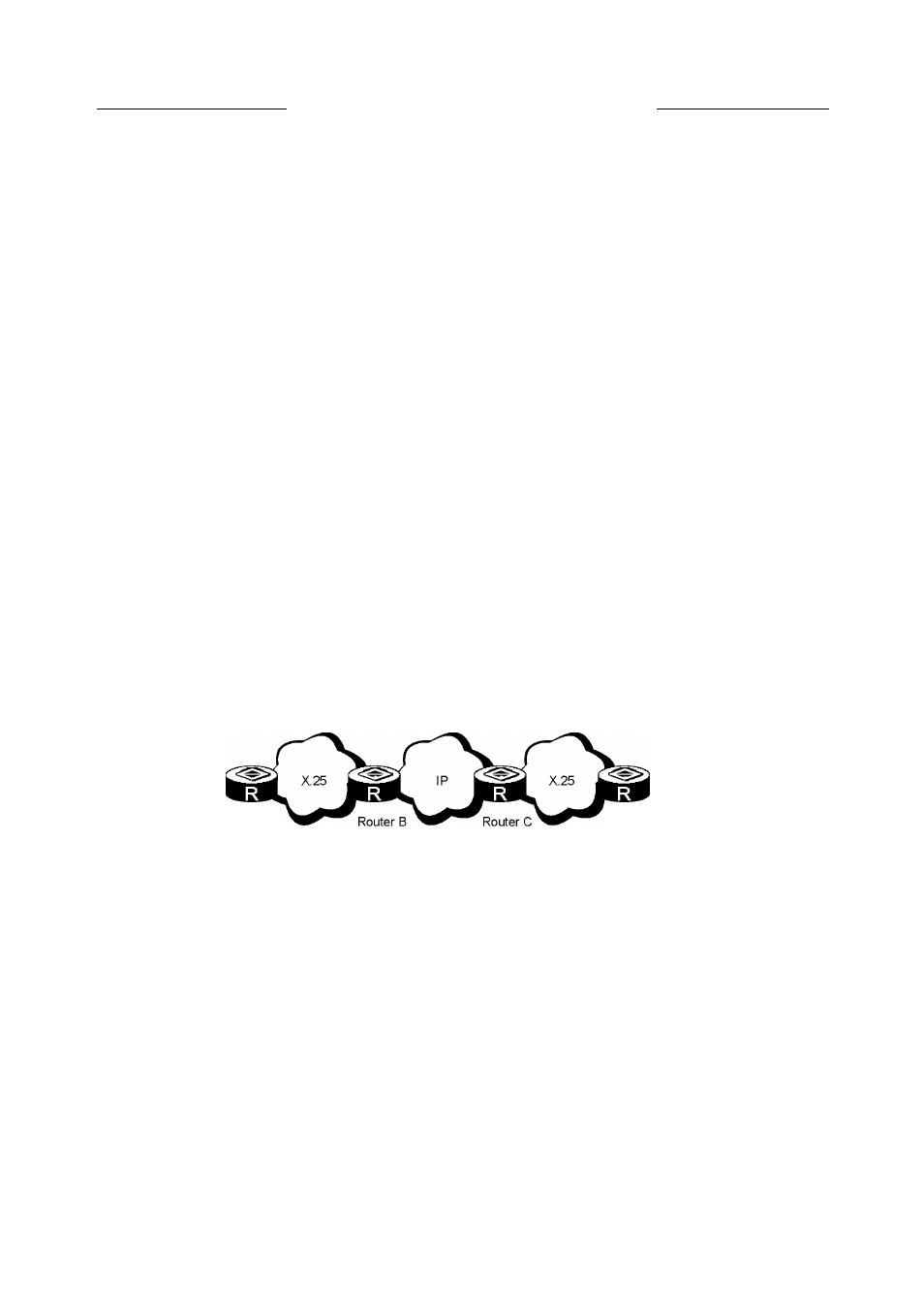
Figure 7-6
XOT typical application diagram
Router A
Router D
Consider the middle Router B, Router C and IP network as a large "X.25 switch", and
consider that the data is directly switched from Router A to Router D through this "switch".
As shown in Figure 7-6, the implementation theory of XOT is described below considering
SVC as an example:
When Router A has to transmit data, it first sends a request packet to set up a VC.
•
After Router B receives the call packet and judges that it is XOT application, it first sets
up a TCP connection with Router C. The router then attaches the XOT packet header to
X.25 call packet and encapsulates it in TCP to send the call packet to Router C.
•
Router C removes the TCP and XOT packet headers and sends the call request packet to
Router D through X.25 local switch.
•
After Router D receives the call request packet, it replies the call to confirm.
•
The link between Router A and Router D is set up and enters the data transmission status.
7-8
Nortel Networks Inc.
Issue 5.3 (30 March 2009)
