Avaya 580 User Manual
Page 425
Document No. 10-300077, Issue 2
13-5
Configuring Access Lists
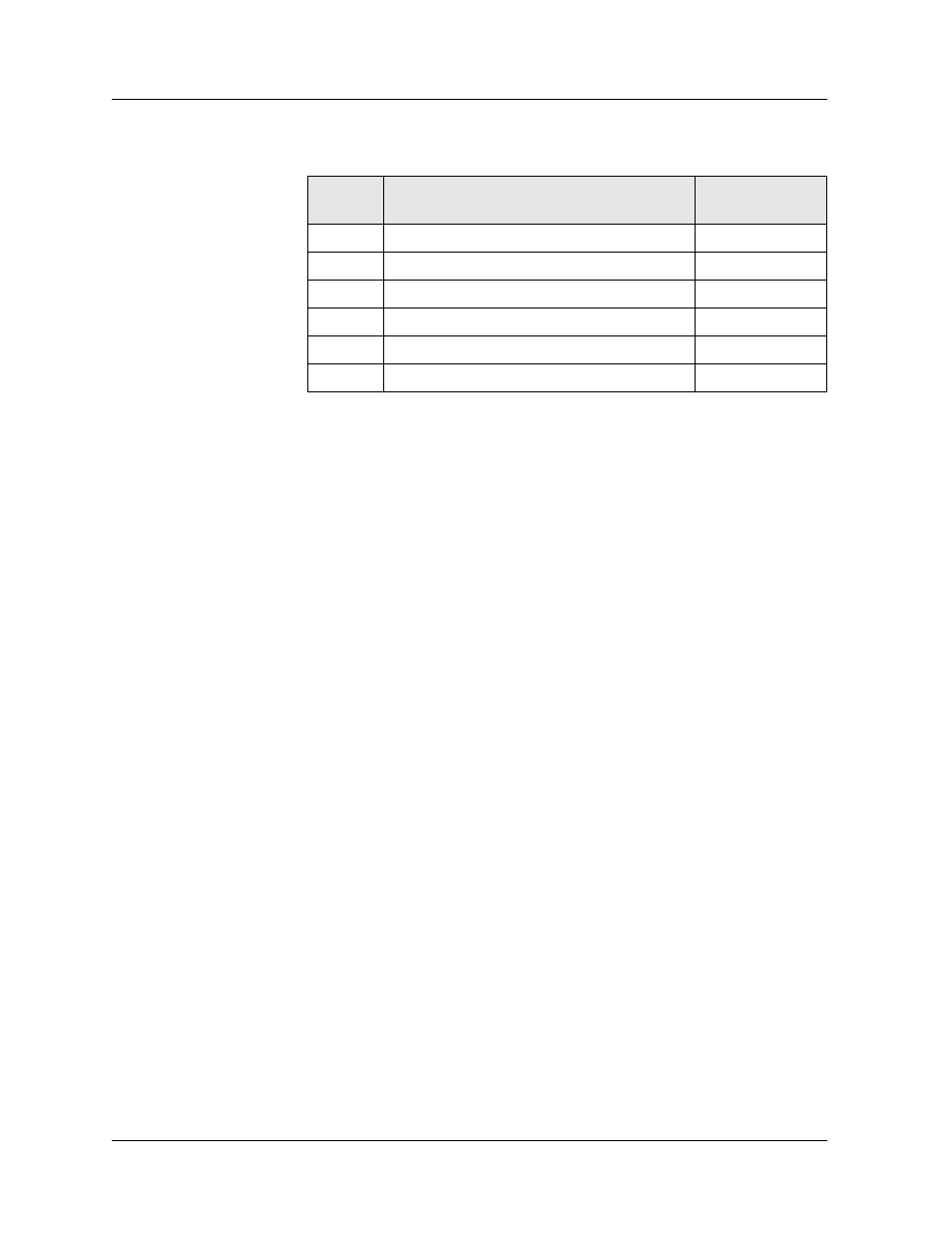
The rules for implementing the above restrictions would be as follows:
Rules 1 and 2 collectively manage Web traffic to and from the Web server
(WS). Rule 1 says that any source address can get to the Web server’s IP
address using destination port 80. Because the TCP Established criteria is
unchecked, hosts from any network can send a TCP “call setup” message as
a first step in requesting a Web page.
Rule 2 says that the Web server may respond to any (TCP) Web request.
Although it can send a message back to any address from any source port,
only messages that are in response to a Web request will be forwarded
because TCP Established is checked and the source port criteria is specified.
Rules 3 and 4 handle traffic from the Web server that is not in response to a
Web request. Rule 3 gives the Web server access to the rest of the Inside
networks. And Rule 4 blocks the Web server from getting to the rest of the
networks (Outside).
Rule 5 gives the hosts on the Inside network access to any network.
Rule 6 blocks any other host from using resources on any of the Inside
networks.
* Note: In this simple example, pseudo-rules are used. In practice, the
pseudo-rule “allow WS to IN” would require that you create
rules that forward traffic from the Web server’s IP address to
each network on the Inside explicitly. If you had 30 inside
networks, you’d create 30 rules. This is where a subnetted
network would be powerful; because you could summarize
subnets into a few rules.
Rule #
Rule
TCP
Established
1
allow Any to call WS dest port 80
Un-Checked
2
allow WS to respond
Checked
3
allow WS to IN
Un-Checked
4
deny WS to Any (Outside)
Un-Checked
5
allow IN to Any
Un-Checked
6
deny remaining traffic from Outside to Any
Un-Checked
