H3C Technologies H3C MSR 50 User Manual
Page 94
73
Item Description
TKIP CM Time
Set the TKIP countermeasure time.
By default, the TKIP countermeasure time is 0 seconds, that is, the TKIP
countermeasure policy is disabled.
If the TKIP countermeasure time is set to a value other than 0, the TKIP
countermeasure policy is enabled.
MIC is designed to avoid hacker tampering. It uses the Michael algorithm and is
extremely secure. When failures occur to MIC, the data may have been
tampered, and the system may be under attack. In this case, TKIP will enable the
countermeasure policy to prevent hackers from attacking. With the
countermeasure policy enabled, if more than two MIC failures occur within the
specified time, the TKIP disassociates all connected wireless clients and no new
associations are allowed within the TKIP countermeasure time.
Management Right
Web interface management right of online clients:
•
Disable—Disables the Web interface management right of online clients.
•
Enable—Enables the Web interface management right of online clients.
GTK Rekey Method
An AP generates a group transient key (GTK) and sends the GTK to a client
during the authentication process between an AP and the client through group
key handshake/the 4-way handshake. The client uses the GTK to decrypt
broadcast and multicast packets.
•
If Time is selected, the GTK is refreshed after a specified period of time.
•
If Packet is selected, the GTK is refreshed after a specified number of packets
are transmitted.
By default, the GTK rekeying method is time-based, and the interval is 86400
seconds.
GTK User Down Status
Enable refreshing the GTK when some client goes offline.
By default, the GTK is not refreshed when a client goes off-line.
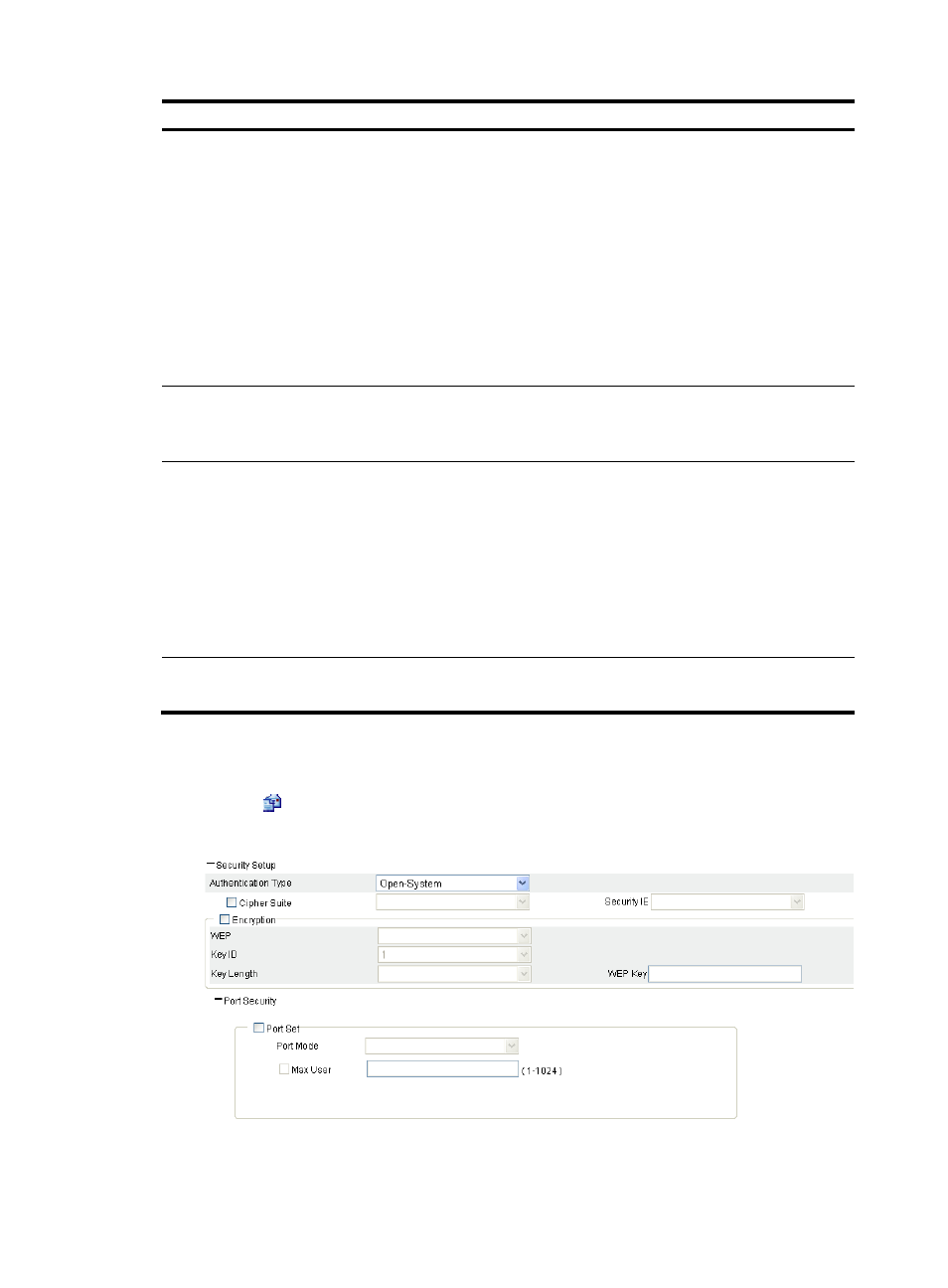
Configuring security settings for crypto type wireless service
1.
Select Interface Setup > Wireless > Access Service from the navigation tree.
2.
Click the
icon for the target crypto type wireless service.
Figure 47 Configuring security settings for crypto type wireless service
