Vpn configuration - example – Brocade Mobility 7131 Access Point Product Reference Guide (Supporting software release 4.4.0.0 and later) User Manual
Page 241
Brocade Mobility 7131 Access Point Product Reference Guide
229
53-1002517-01
6
4. Click Ok to return to the VPN screen. Click Apply to retain the settings made on the IKE Settings
screen.
5. Click Cancel to return to the VPN screen without retaining the changes made to the IKE
Settings screen.
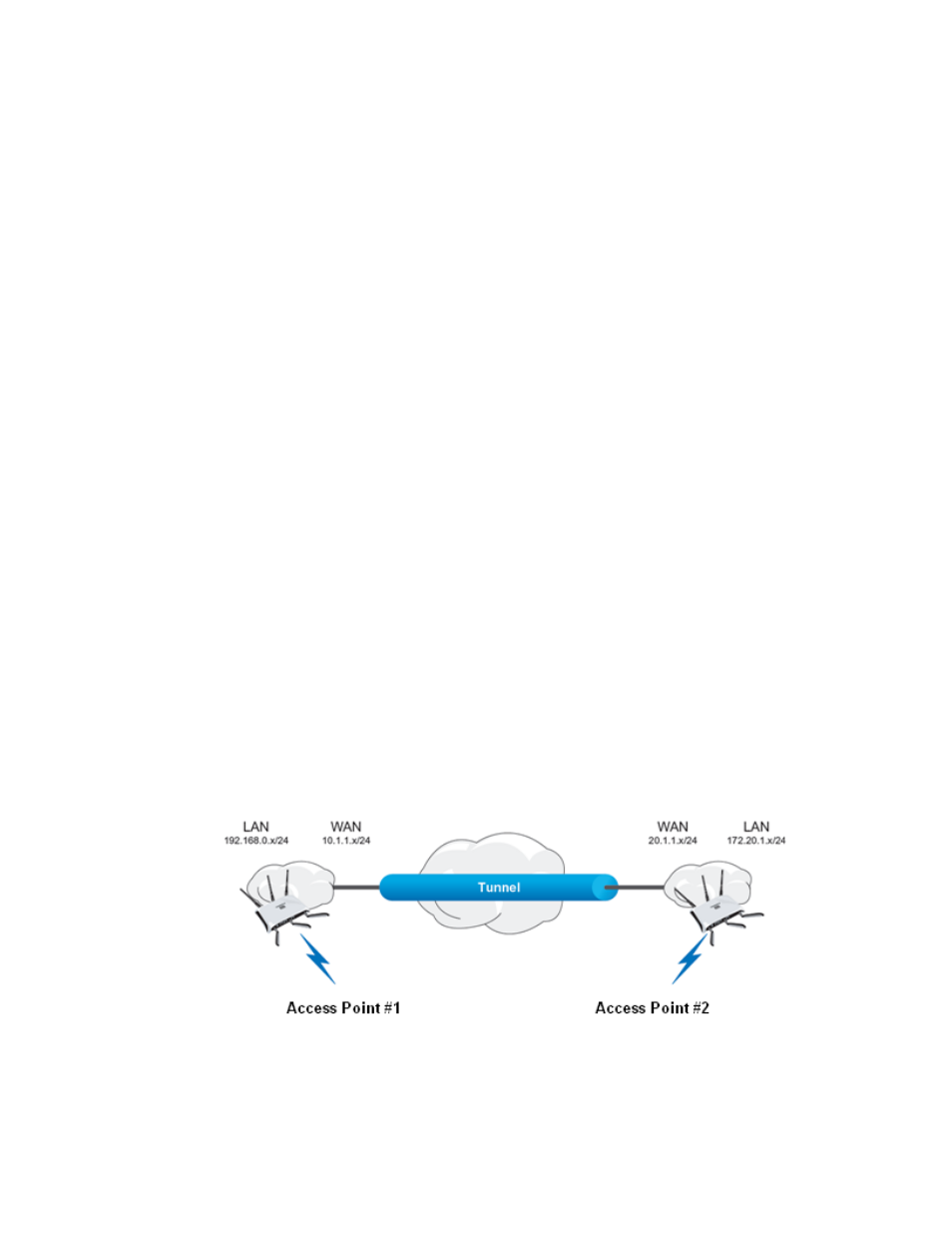
VPN Configuration - Example
The VPN topology used in this example is as follows:
To set the configuration on the access points:
IKE Encryption
Algorithm
Select the encryption and authentication algorithms for the VPN tunnel from the drop-down
menu.
•
DES - Uses the DES encryption algorithm. No keys are required to be
manually provided.
•
3DES - Enables the 3DES encryption algorithm. No keys are required to
be manually provided.
•
AES 128-bit - Uses the Advanced Encryption Standard algorithm with
128-bit. No keys are required to be manually provided.
•
AES 192-bit - Enables the Advanced Encryption Standard algorithm with
192-bit. No keys are required to be manually provided.
•
AES 256-bit - Uses the Advanced Encryption Standard algorithm with
256-bit. No keys are required to be manually provided.
Key Lifetime
The number of seconds the key is valid. At the end of the lifetime, the key is renegotiated.
The Mobility 7131 Access Point forces renegotiation every 3600 seconds. There is no way
to change the renegotiation value. If the IKE Lifetime is greater than 3600, the keys still get
renegotiated every 3600 seconds.
Diffie Hellman Group
Select a
Diffie-Hellman Group
to use. The Diffie-Hellman key agreement protocol allows
two users to exchange a secret key over an insecure medium without any prior secrets. Two
algorithms exist, 768-bit and 1024-bit. Select one of the following options:
•
Group 1 - 768 bit - Somewhat faster than the 1024-bit algorithm, but
secure enough in most situations.
•
Group 2 - 1024 bit - Somewhat slower than the 768-bit algorithm, but
much more secure and a better choice for extremely sensitive situations.
