Top 10 attack destinations report, The execution results report, Integrating scc with sms – H3C Technologies H3C Intelligent Management Center User Manual
Page 970
956
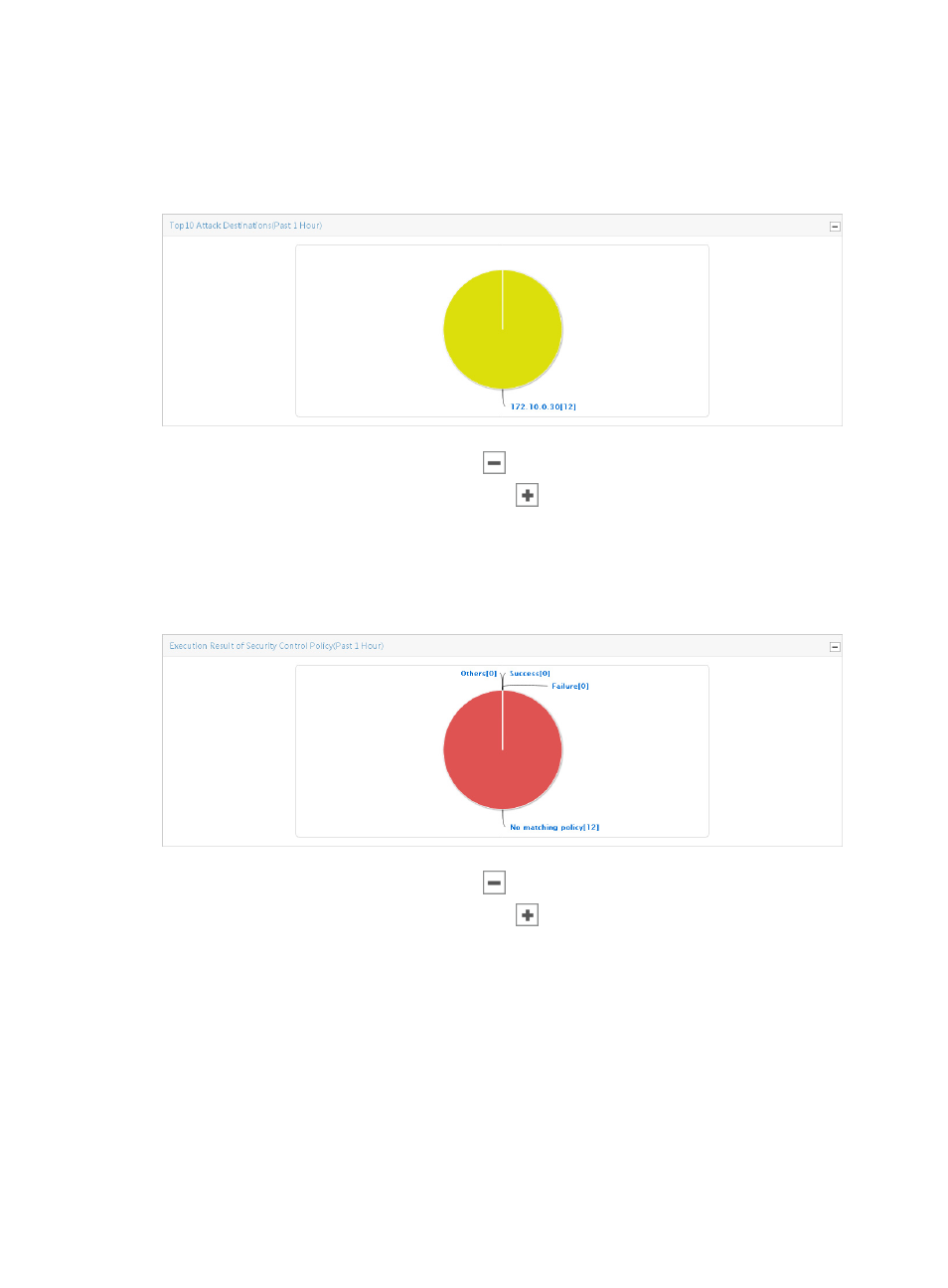
Top 10 attack destinations report
The Top 10 Attack Destinations report provides you with a pie chart displaying the distribution of attacks
by the attack destination IP address, as shown in
.
Figure 95 Top 10 attack destinations
•
To hide this graph, click the Collapse icon
located in the upper right corner of the graph.
•
To view a hidden graph, click the Expand icon
located in the upper right corner of the graph.
The execution results report
The Execution Result of Security Control Policy report provides you with a pie chart displaying the
distribution of execution results, as shown in
.
Figure 96 Execution result of security control policy
•
To hide this graph, click the Collapse icon
located in the upper right corner of the graph.
•
To view a hidden graph, click the Expand icon
located in the upper right corner of the graph.
Integrating SCC with SMS
The Security Management System (SMS) software is designed for network security monitoring and
management, enabling operators to obtain the status information and alarms from the security devices
on the network and manage the entire network security status in real time.
For unified management, you can integrate SCC with SMS and enter the SMS management page in
SCC to monitor the network-wide security devices.
