H3C Technologies H3C S3100 Series Switches User Manual
Page 488
Operation Manual – SSH Terminal Service
H3C S3100-52P Ethernet Switch
Chapter 1 SSH Terminal Service
1-2
Local switch
Local Ethernet
WAN
Server
PC
SSH
PC
Laptop
Laptop
PC
Laptop
Laptop
Workstation
Workstation
Remote Ethernet
Server
WAN
Server
PC
SSH
PC
Laptop
Laptop
WAN
Server
PC
SSH
PC
Laptop
Laptop
PC
Laptop
Laptop
Workstation
Workstation
Rem
Remote sw itch
SSH
ote Ethernet
Server
WAN
Server
PC
SSH
PC
Laptop
Laptop
PC
Laptop
Laptop
Workstation
Workstation
Remote Ethernet
Server
WAN
Server
PC
SSH
PC
Laptop
Laptop
WAN
Server
PC
SSH
PC
Laptop
Laptop
PC
Laptop
Laptop
Workstation
Workstation
Rem
SSH
ote Ethernet
Server
Local switch
Local Ethernet
WAN
Server
PC
SSH
PC
Laptop
Laptop
Local switch
Local Ethernet
WAN
Server
PC
SSH
PC
Laptop
Laptop
PC
Laptop
Laptop
Workstation
Workstation
Remote Ethernet
Server
WAN
PC
Laptop
Laptop
Workstation
Workstation
Remote Ethernet
Server
WAN
Server
PC
SSH
PC
Laptop
Laptop
WAN
Server
PC
SSH
PC
Laptop
Laptop
WAN
Server
PC
SSH
PC
Laptop
Laptop
PC
Laptop
Laptop
Server
PC
SSH
PC
Laptop
Laptop
PC
Laptop
Laptop
Workstation
Workstation
Rem
Remote sw itch
SSH
ote Ethernet
Server
WAN
Server
PC
SSH
Workstation
Workstation
Rem
Remote sw itch
SSH
ote Ethernet
Server
WAN
Server
PC
SSH
PC
Laptop
Laptop
PC
Laptop
Laptop
Workstation
PC
Laptop
Laptop
PC
Laptop
Laptop
Workstation
Workstation
Remote Ethernet
Server
WAN
Server
PC
SSH
PC
Laptop
Workstation
Remote Ethernet
Server
WAN
Server
PC
SSH
PC
Laptop
Laptop
WAN
Server
PC
SSH
PC
Laptop
Laptop
WAN
Server
PC
SSH Client
PC
Laptop
Laptop
PC
Laptop
Laptop
Workstation
Workstation
Rem
SSH Server
ote Ethernet
Server
Local switch
Local Ethernet
WAN
Server
PC
SSH
PC
Laptop
Laptop
Local switch
Local Ethernet
WAN
Server
PC
SSH
PC
Laptop
Laptop
PC
Laptop
Laptop
Workstation
Workstation
Remote Ethernet
Server
WAN
PC
Laptop
Laptop
Workstation
Workstation
Remote Ethernet
Server
WAN
Server
PC
SSH
PC
Laptop
Laptop
WAN
Server
PC
SSH
PC
Laptop
Laptop
WAN
Server
PC
SSH
PC
Laptop
Laptop
PC
Laptop
Laptop
Server
PC
SSH
PC
Laptop
Laptop
PC
Laptop
Laptop
Workstation
Workstation
Rem
Remote sw itch
SSH
ote Ethernet
Server
WAN
Server
PC
SSH
Workstation
Workstation
Rem
Remote sw itch
SSH
ote Ethernet
Server
WAN
Server
PC
SSH
PC
Laptop
Laptop
PC
Laptop
Laptop
Workstation
PC
Laptop
Laptop
PC
Laptop
Laptop
Workstation
Workstation
Remote Ethernet
Server
WAN
Server
PC
SSH
PC
Laptop
Workstation
Remote Ethernet
Server
WAN
Server
PC
SSH
PC
Laptop
Laptop
WAN
Server
PC
SSH
PC
Laptop
Laptop
WAN
Server
PC
SSH
PC
Laptop
Laptop
PC
Laptop
Laptop
Workstation
Workstation
Rem
SSH
ote Ethernet
Server
Local switch
Local Ethernet
WAN
Server
PC
SSH
PC
Laptop
Laptop
Local switch
Local Ethernet
WAN
Server
PC
SSH
PC
Laptop
Laptop
PC
Laptop
Laptop
Workstation
Workstation
Remote Ethernet
Server
WAN
PC
Laptop
Laptop
Workstation
Workstation
Remote Ethernet
Server
WAN
Server
PC
SSH
PC
Laptop
Laptop
WAN
Server
PC
SSH
PC
Laptop
Laptop
WAN
Server
PC
SSH
PC
Laptop
Laptop
PC
Laptop
Laptop
Server
PC
SSH
PC
Laptop
Laptop
PC
Laptop
Laptop
Workstation
Workstation
Rem
Remote sw itch
SSH
ote Ethernet
Server
WAN
Server
PC
SSH
Workstation
Workstation
Rem
Remote sw itch
SSH
ote Ethernet
Server
WAN
Server
PC
SSH
PC
Laptop
Laptop
PC
Laptop
Laptop
Workstation
PC
Laptop
Laptop
PC
Laptop
Laptop
Workstation
Workstation
Remote Ethernet
Server
WAN
Server
PC
SSH
PC
Laptop
Workstation
Remote Ethernet
Server
WAN
Server
PC
SSH
PC
Laptop
Laptop
WAN
Server
PC
SSH
PC
Laptop
Laptop
WAN
Server
PC
SSH Client
PC
Laptop
Laptop
PC
Laptop
Laptop
Workstation
Workstation
Rem
SSH Server
ote Ethernet
Server
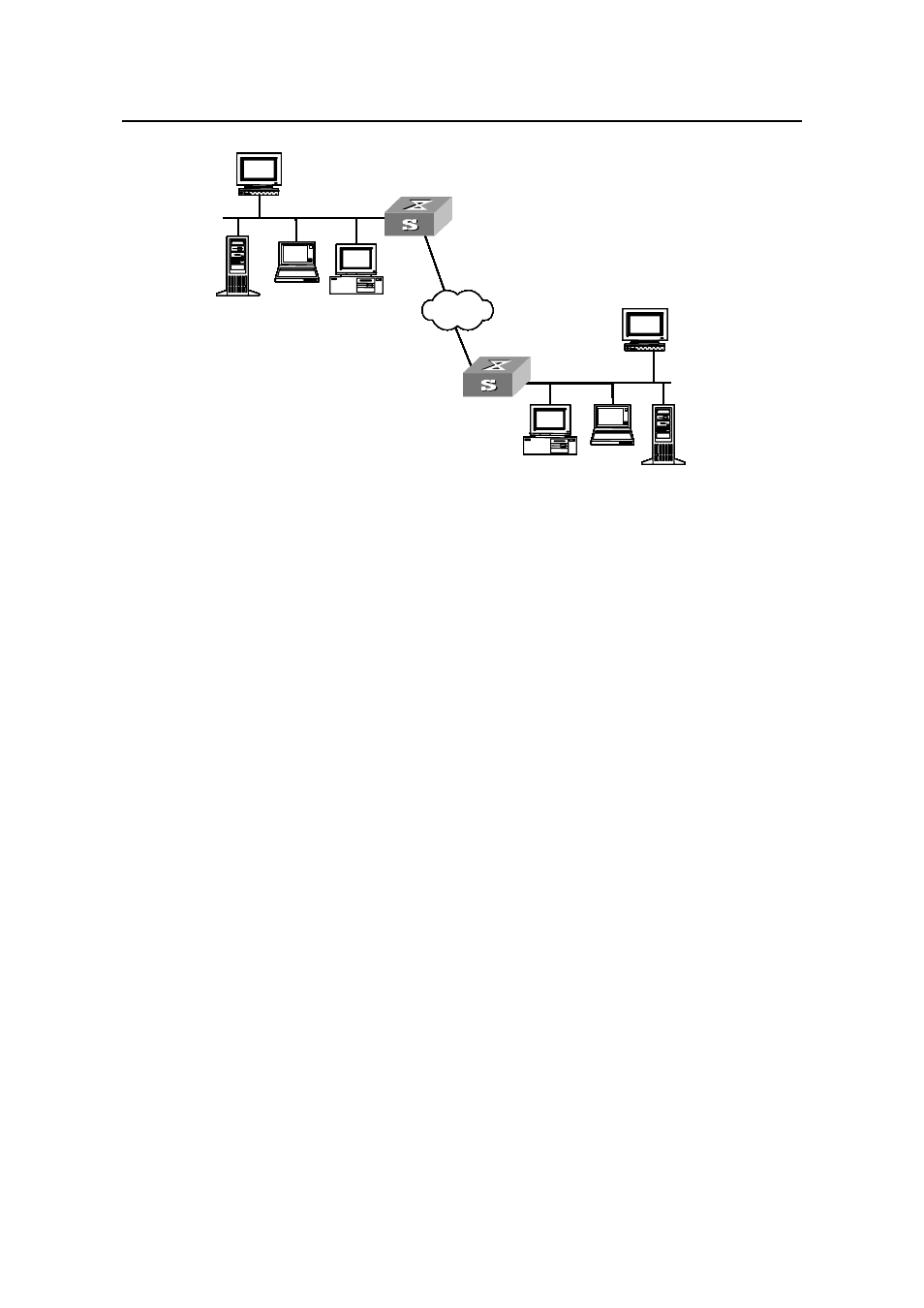
Figure 1-2
Establish SSH connection through a WAN
The communication process between a SSH client and server goes through the
following five stages.
1) Version negotiation stage:
z
The client sends a TCP connection request to the server.
z
When a TCP connection is established, the two ends begin to negotiate an SSH
version.
z
If they get a successful negotiation, they go to the key negotiation stage.
Otherwise the server terminates the TCP connection.
2) Key negotiation stage:
z
The server sends the public key in a randomly generated RSA key pair to the
client.
z
The client calculates a session key by using the public key received from the
server and a random number it generates randomly.
z
The client encrypts the random number with the public key from the server and
sends the result data to the server.
z
The server then decrypts the received data with the private key in the RSA key pair
to get the random number on the client.
z
The server calculates a session key by using the public key and the random
number through the same algorithm as the client.
Then, the server and the client get the same session key, and use it for data encryption
and decryption to secure their subsequent communication.
3) Authentication negotiation stage:
z
The client sends its username information to the server.
