4 configuring hwtacacs accounting servers, 5 configuring shared keys for hwtacacs messages, Configuring – H3C Technologies H3C S3100 Series Switches User Manual
Page 335: Hwtacacs, Accounting servers, Configuring shared, Keys for hwtacacs, Messages
Operation Manual – AAA – RADIUS – HWTACACS
H3C S3100-52P Ethernet Switch
Chapter 1 AAA & RADIUS & HWTACACS
Configuration
1-36
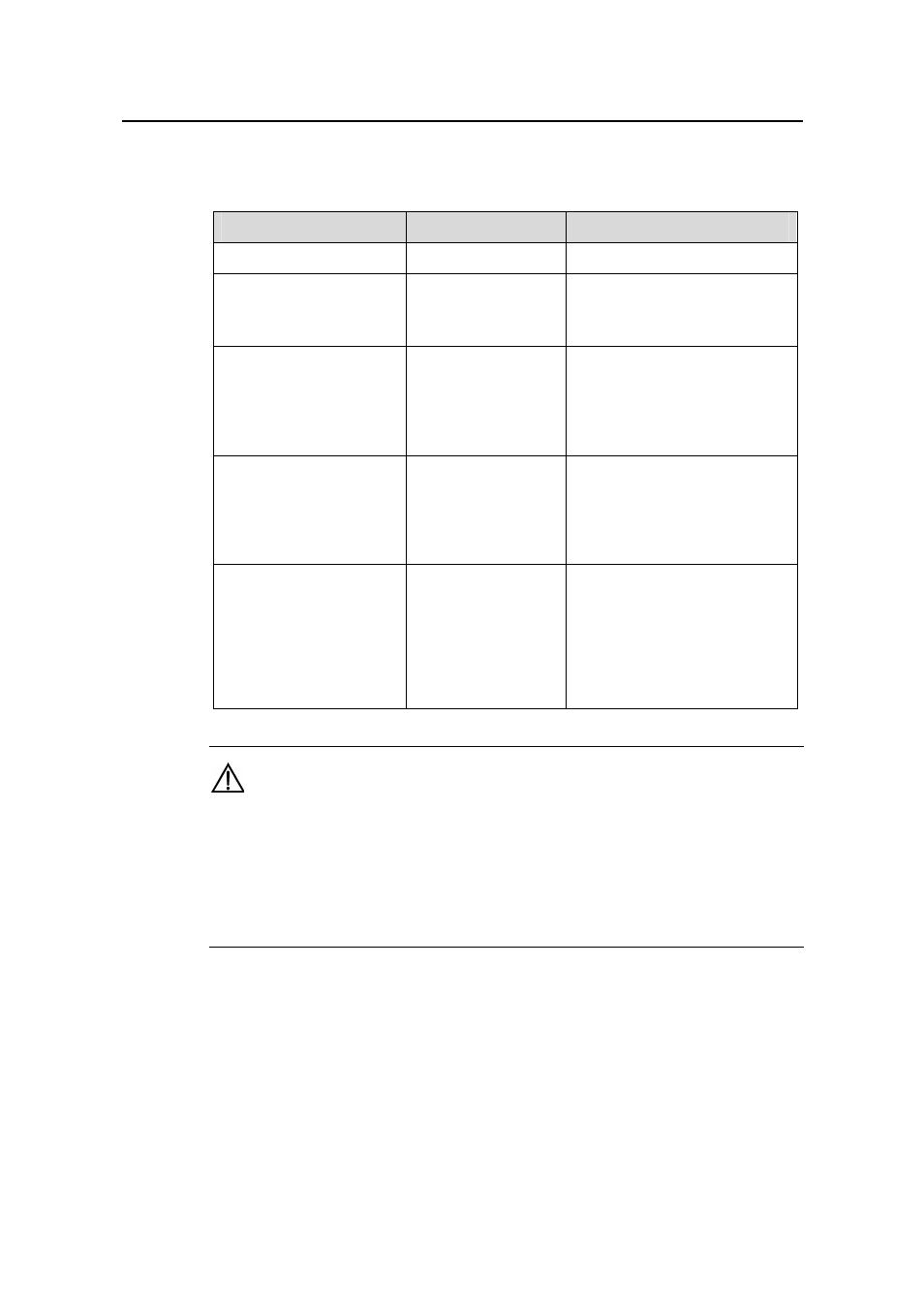
1.5.4 Configuring HWTACACS Accounting Servers
Table 1-27
Configure HWTACACS accounting servers
Operation
Command
Description
Enter system view
system-view
—
Create a HWTACACS
scheme and enter its view
hwtacacs scheme
hwtacacs-scheme-n
ame
Required
By default, no HWTACACS
scheme exists.
Set the IP address and
port number of the
primary TACACS
accounting server
primary
accounting
ip-address
[ port ]
Required
By default, the IP address of
the primary accounting server
is 0.0.0.0, and the port number
is 0.
Set the IP address and
port number of the
secondary TACACS
accounting server
secondary
accounting
ip-address
[ port ]
Required
By default, the IP address of
the secondary accounting
server is 0.0.0.0, and the port
number is 0.
Enable the
stop-accounting message
retransmission function
and set the maximum
number of transmission
attempts of a buffered
stop-accounting message
retry
stop-accounting
retry-times
Optional
By default, the stop-accounting
messages retransmission
function is enabled and the
system can transmit a buffered
stop-accounting request for
100 times.
Caution:
z
You are not allowed to configure the same IP address for both primary and
secondary accounting servers. If you do this, the system will prompt that the
configuration fails.
z
You can remove a server only when it is not used by any active TCP connection for
sending accounting messages.
1.5.5 Configuring Shared Keys for HWTACACS Messages
When using a TACACS server as an AAA server, you can set a key to improve the
communication security between the switch and the TACACS server.
The TACACS client and server adopt MD5 algorithm to encrypt HWTACACS messages
before they are exchanged between the two parties. The two parties verify the validity
of the HWTACACS messages received from each other by using the shared keys that
