2 information transmission in the broadcast mode, 3 information transmission in the multicast mode – H3C Technologies H3C S3100 Series Switches User Manual
Page 229
Operation Manual – Multicast
H3C S3100-52P Ethernet Switch
Chapter 1 Multicast Overview
1-2
1.1.2 Information Transmission in the Broadcast Mode
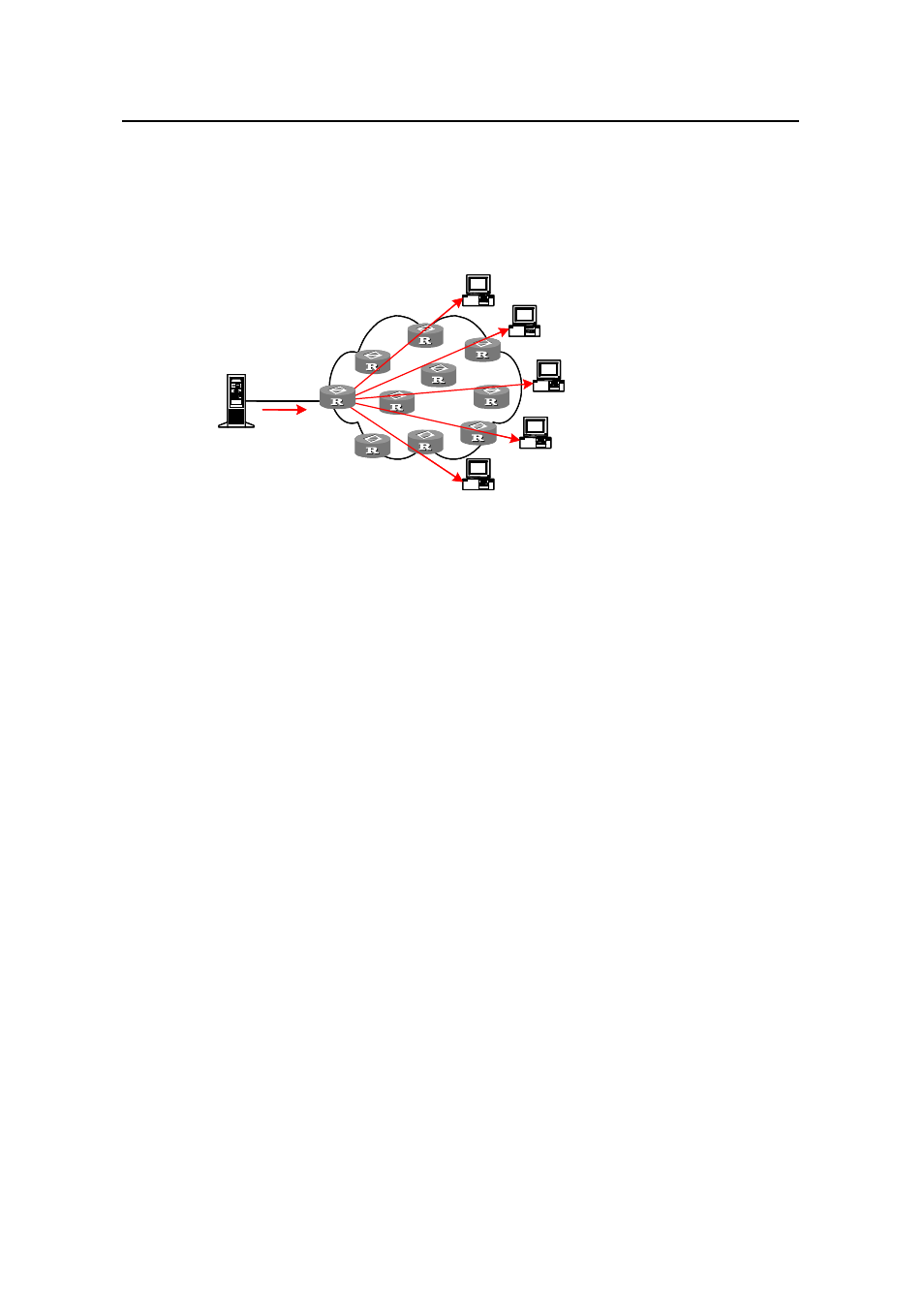
When you adopt broadcast, the system transmits information to all users on a network.
Any user on the network can receive the information, no matter the information is
needed or not. Figure 1-2 shows information transmission in broadcast mode.
Server
Broadcast
Us
Us
er A
User B
User C
User D
er E
Server
Broadcast
Server
Broadcast
Us
Us
er A
User B
User C
User D
er E
Figure 1-2
Information transmission in the broadcast mode
Assume that users B, D, and E need the information. The source server broadcasts this
information through routers, and users A and C on the network also receive this
information. The security and payment of the information cannot be guaranteed.
As we can see from the information transmission process, the security and legal use of
paid service cannot be guaranteed. In addition, when only a small number of users on
the same network need the information, the utilization ratio of the network resources is
very low and the bandwidth resources are greatly wasted.
Therefore, broadcast is disadvantageous in transmitting data to specified users;
moreover, broadcast occupies large bandwidth.
1.1.3 Information Transmission in the Multicast Mode
As described in the previous sections, unicast is suitable for networks with sparsely
distributed users, whereas broadcast is suitable for networks with densely distributed
users. When the number of users requiring information is not certain, unicast and
broadcast deliver a low efficiency.
Multicast solves this problem. When some users on a network require specified
information, the multicast information sender (namely, the multicast source) sends the
information only once. With tree-type routes established for multicast data packets
through a multicast routing protocol, the packets are duplicated and distributed at the
nearest nodes, as shown in Figure 1-3:
