Figure 1-2, Software configuration management overview – HP Integrity NonStop H-Series User Manual
Page 41
Introduction to DSM/SCM
DSM/SCM User’s Guide — 529846-014
1 - 8
Installing and Configuring Software
The temporary file naming allows files to be applied while the system is running without
interfering with the existing files on the running system. If the system needs to be
backed out to the previous revision, ZPHIRNM is run during the Backout process to
give the actual file names back to the files from the previous revision. The renaming
process reduces application downtime and allows for a quick backout by rerunning
ZPHIRNM and specifying the previous SYSnn.
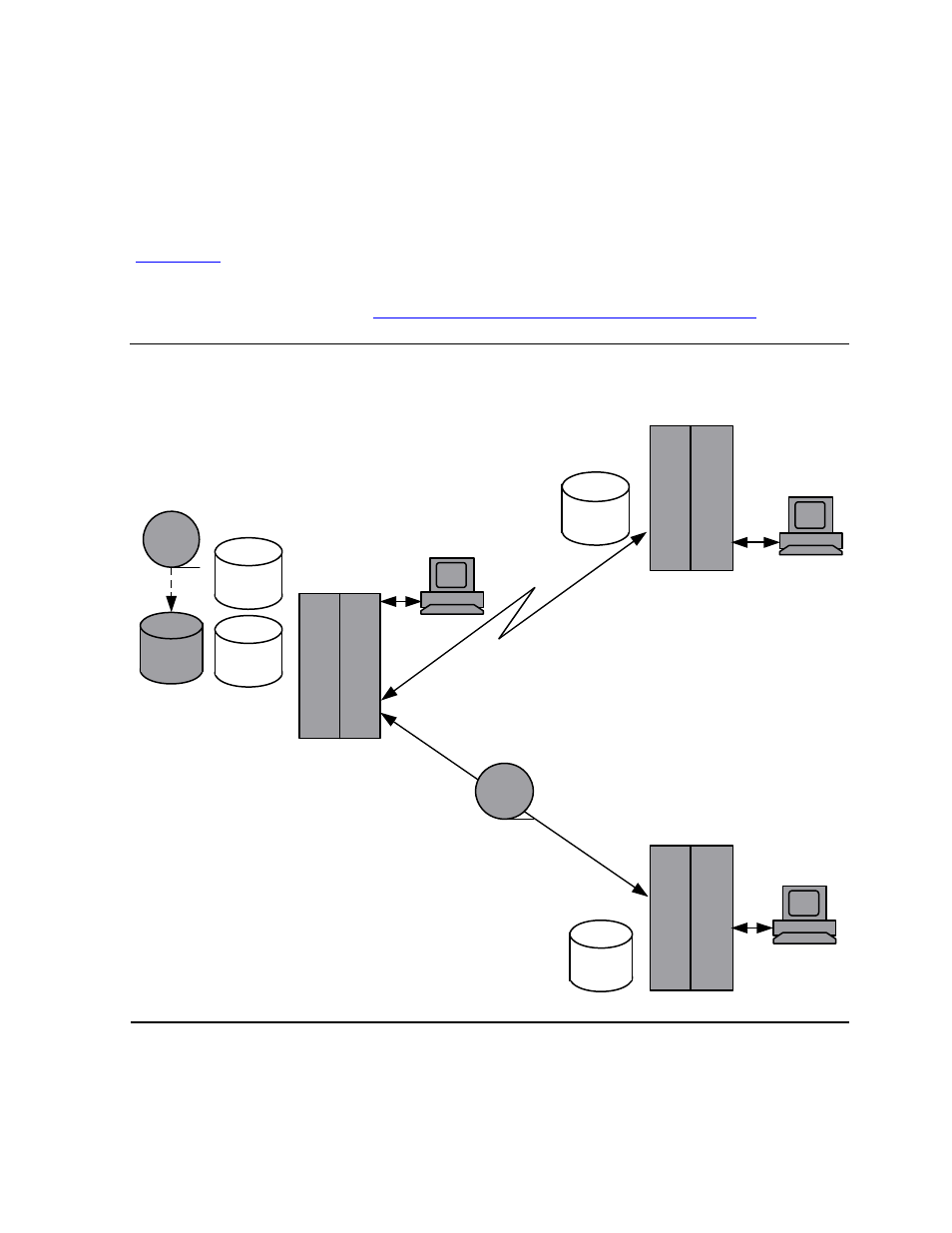
is an overview of the software configuration management process in a
typical DSM/SCM usage pattern, applied to networked and non-networked systems.
For detailed procedures, see
Part III, Software Installation and Management
Figure 1-2. Software Configuration Management Overview
1. Receive software inputs into
the Archive (on host):
RVUs
SPRs
Third-party software
Customer software
2. Create a new software revision
(on host):
Review softdocs.
Create new revision from an
existing revision.
3. Build a configuration revision
(on host):
DSM/SCM builds SRLs or DLLs.
DSM/SCM packages software into
activation package on disk or tape.
4. Apply the configuration revision
(on target):
DSM/SCM puts new software into TSVs
or TDLs. DSM/SCM creates snapshot to
update host database.
5. Activate the software on the target
system:
Operator follows planner
instructions.
\A Host system
\B Target system
\C Target system
Target
Interface
Target
Interface
Tape
Planner
Interface
Tape
Expand
\A
Target
database
Host
database
Archive
VST003.vsd
\B
Target
database
Receive target snapshot into host
database (on host):
Automatic during Apply if target is
connected through Expand.
\C
Target
database
