Ip access-group – Enterasys Networks X-Pedition XSR CLI User Manual
Page 634
General Security Commands
16-90 Configuring Security
Example
The example below enables protection from land attack and large ICMP packets. Synflood
protection will trigger for more than 7 sessions. Protection against large ICMP packets will trigger
for packets larger than 2,000 bytes.
XSR(config)#hostdos land
XSR(config)#hostdos largeicmp 2000
ip access-group
This command applies access list restrictions to an interface.
Syntax
ip access-group access list-number {in | out}
Syntax of the “no” Form
The no form of this command removes the specified access group:
no ip access-group access list-number {in | out}
Mode
Interface configuration:
XSR(config-if<xx>)#
Example
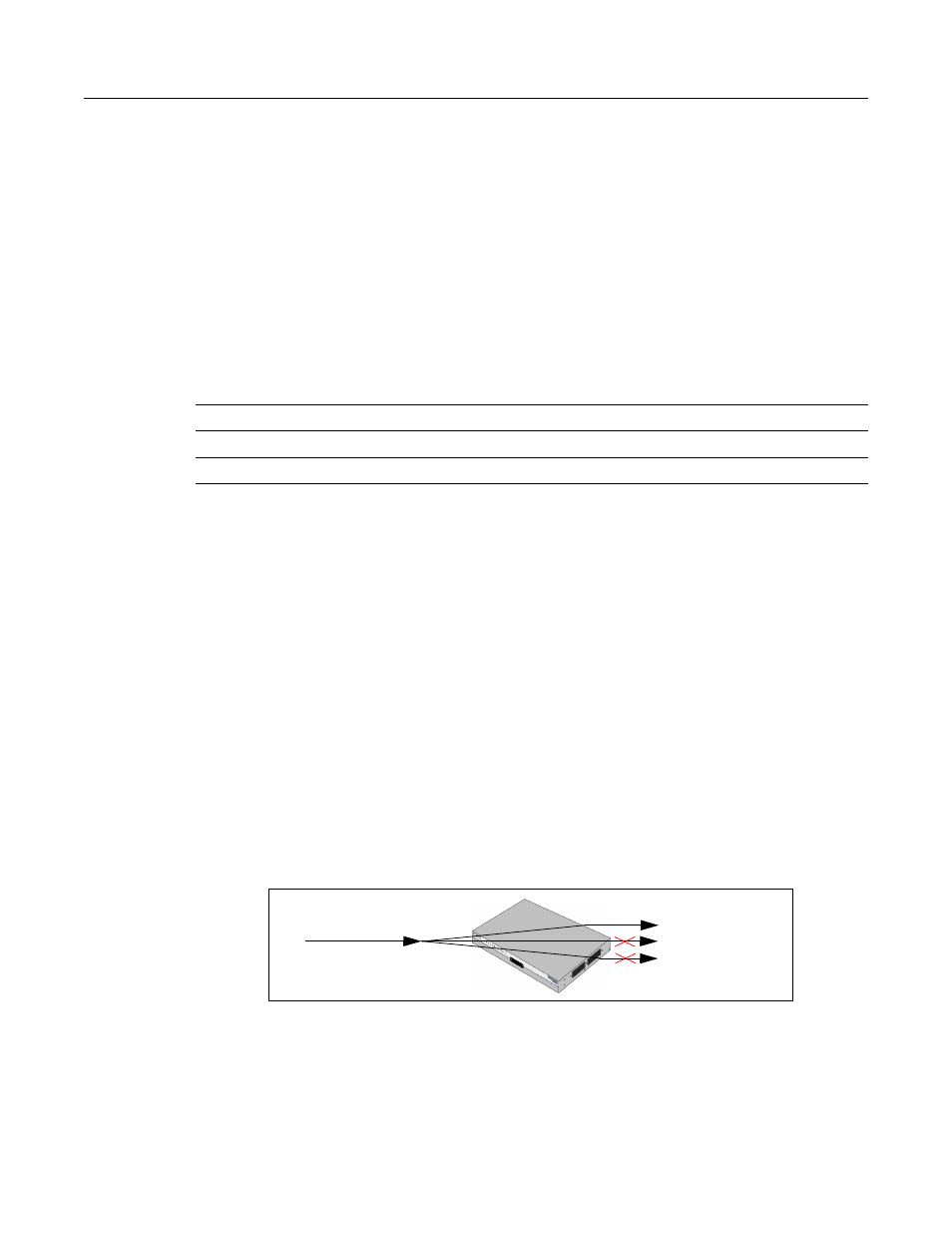
The following example, as illustrated in
, applies ACL 101 to all inbound packets on
interface FastEthernet 1. ACL 101 will route only packets with a destination of network 192.5.34.0.
All packets with other destinations received on FastEthernet 1 will be dropped.
XSR(config)#access-list 101 permit any 192.5.34.0 0.0.0.255
XSR(config)#interface FastEthernet 1
XSR(config-if
Figure 16-1 IP Access-Group Example
list-number
Number of an access list, ranging from 1 to 199.
in
Filters on inbound packets
out
Filters on outbound packets
Eth1
192.5.34.0
192.6.34.0
192.7.34.0
Router 1
