CCTV Camera Pros Geovision 8.2 Multicam Digital Surveillance System User Manual
Page 29
Configuring Main System
1
Keep Pre-Record Files: Specify the number of video clips for pre-record. The maximum number
of video clips you can specify is 9, and the time range of one video clip is from 1 minute to 5
minutes. So the pre-recording time can be from 1 minute to 45 minutes. For the video clip, see
[EventLog Size] below.
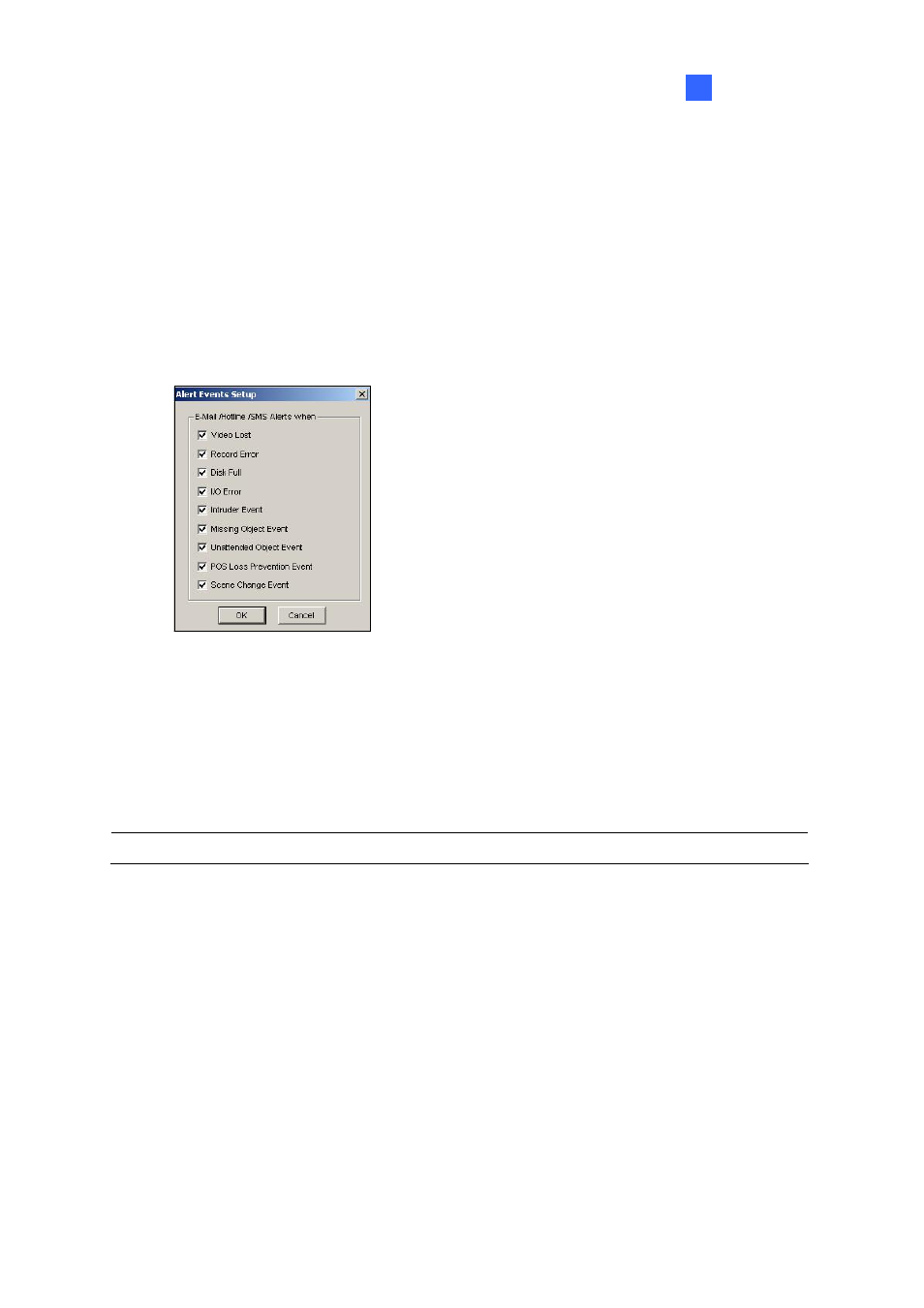
Send Event Alerts: Allows you to send out the assigned E-Mail/Hotline/SMS notification when
the selected alert conditions occur. To enable the function, follow the steps below.
1. Check
the
Send Event Alerts option, and click the Arrow button beside to display this dialog
box.
Figure 1-8
2. Select the desired alert events to send out the assigned notification, and then click OK for the
application.
The alert events of Intruder Event, Missing Object, Unattended Object, and POS Loss Prevention
Event are only available when the alarm settings are activated in Counter Application, Object
Monitor, and POS Application separately.
Note: To select the type of notification, see [Send Alerts Approach] earlier in this chapter.
[EventLog Size] Determines the amount of time (from 1 to 5 minutes) of each event file. If you select 5
Min, a 30-minute event will be chopped into six 5-minute event files; if you select 1 Min, a 30-minute
event will be chopped into thirty 1-minute event files. To decide what to set up here, consider how often
you back up your event files, and how intensive the activity is in your surveillance area. Smaller file
size makes backup process faster.
[Camera Scan] Select to rotate through screen divisions. Click the drop-down list and specify the
amount of time that elapses before switching to the next screen division group. Press the Arrow
button to select the mode of screen divisions.
[Video Record] Click to watermark all recorded videos. Watermark is a way to verify the authenticity
of video streams, and to ensure that they have not been tampered with or modified in any way. For
details, see Watermark Viewer in Chapter 10.
15
