4 mercury t2, 1 general description – Teledyne LeCroy USB Protocol Suite User Manual (Voyager_Advisor T3_Mercury) User Manual
Page 30
Teledyne LeCroy Corporation
Mercury T2
30
USB Protocol Suite User Manual
1.4 Mercury
T2
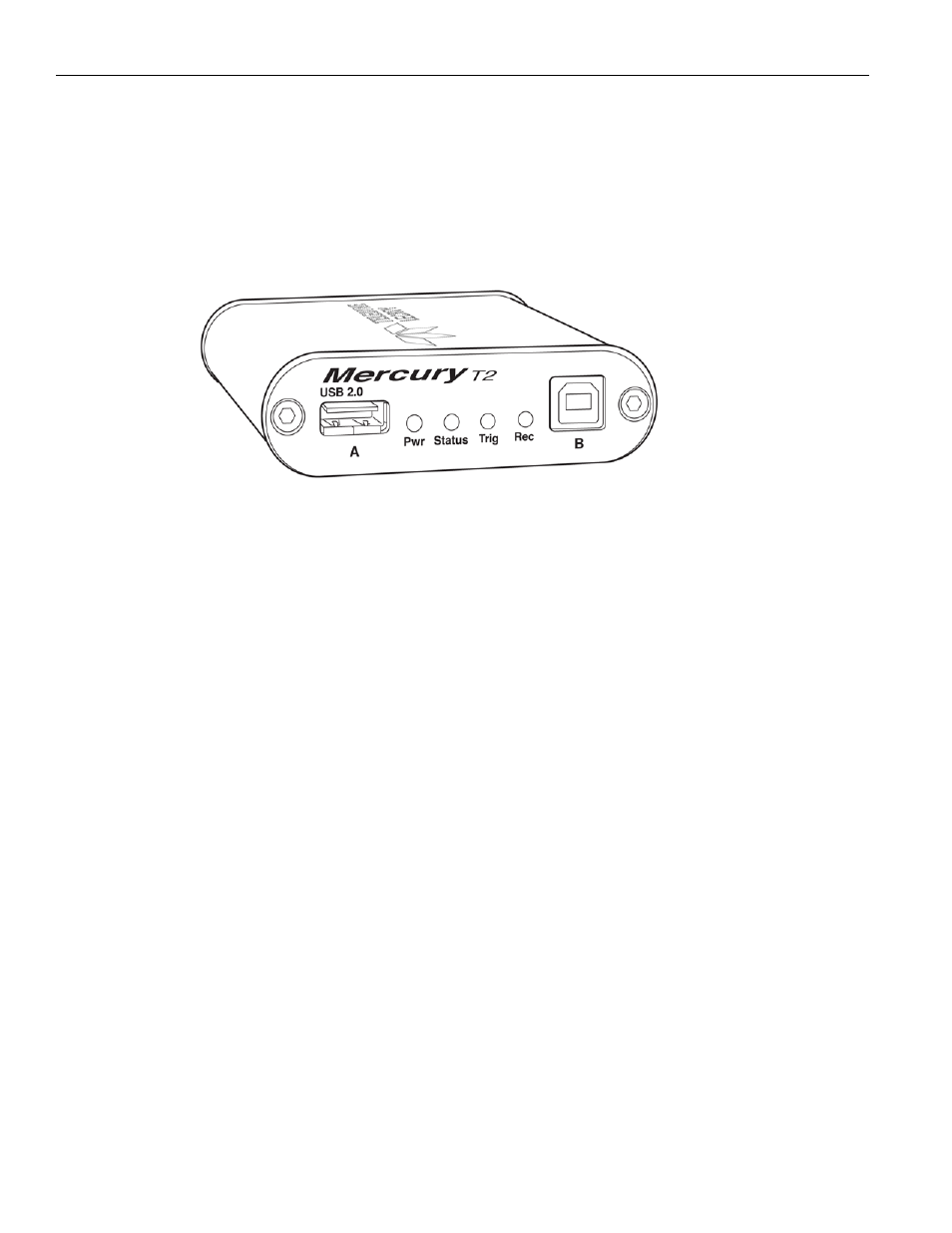
The Teledyne LeCroy Mercury T2™ USB 2.0 Protocol Analyzer is a verification system for
USB development and testing. It supports USB 2.0. It is designed to record USB traffic and
graphically present the logical transactions and events. It connects to a laptop or desktop
host machine via USB 2.0. The Mercury T2 is powered by the USB cable, so no additional
power cord is needed.
Figure 1.6: Mercury T2
The system can monitor traffic between USB 2.0 links using standard high‐speed
compliant cables.
The total length of the cables between the Host Under Test and the Device Under Test
should be kept to < 4 feet.
Please see the Readme file on the installation CD for the latest information on host
machine requirements and supported operating systems.
1.4.1
General Description
The Analyzer connects to a portable or desktop host machine through its USB port. The
host machine configures and controls the Analyzer. The “CATC Trace™” user interface is
an industry standard for documenting the performance of high‐speed serial protocols.
The USB protocol Analyzer provides traffic capture and analysis. Hardware triggering
allows capture of real‐time events. Hardware filtering allows filtering different packet
types in or out of the recording. Filtering also allows you to preserve recording memory,
for extended recording time.
The trace viewer application displays recorded data in colored graphics. The application
has advanced search and viewing capabilities that allow you to quickly locate specific
data, errors, and other conditions.
The system functions with any host machine having the Microsoft
®
Windows
®
XP,
Windows 8, or Windows 7 (32 or 64) operating system and a functional USB interface.
The system provides on‐the‐fly detection of, and triggering on, such events as Tokens and
Errors. Whether recording manually or with a specified trigger condition, the system
continuously records the link data, in a wrap‐around fashion, until manually stopped or
until the system detects the Trigger Event and records the specified post‐trigger amount
of link data.
