Configuring 802.1x, 1x architecture, Access control methods – H3C Technologies H3C WX3000E Series Wireless Switches User Manual
Page 393
377
Configuring 802.1X
802.1X is a port-based network access control protocol initially proposed by the IEEE 802 LAN/WAN
committee for the security of wireless LANs (WLANs). It has been widely used on Ethernet networks for
access control.
802.1X controls network access by authenticating the devices connected to 802.1X-enabled LAN ports.
You can also configure the port security feature to perform 802.1X. Port security combines and extends
802.1X and MAC authentication. It applies to a network, a WLAN, for example, that requires different
authentication methods for different users on a port. Port security is beyond the scope of this chapter. It
is described in Security Configuration Guide for the product.
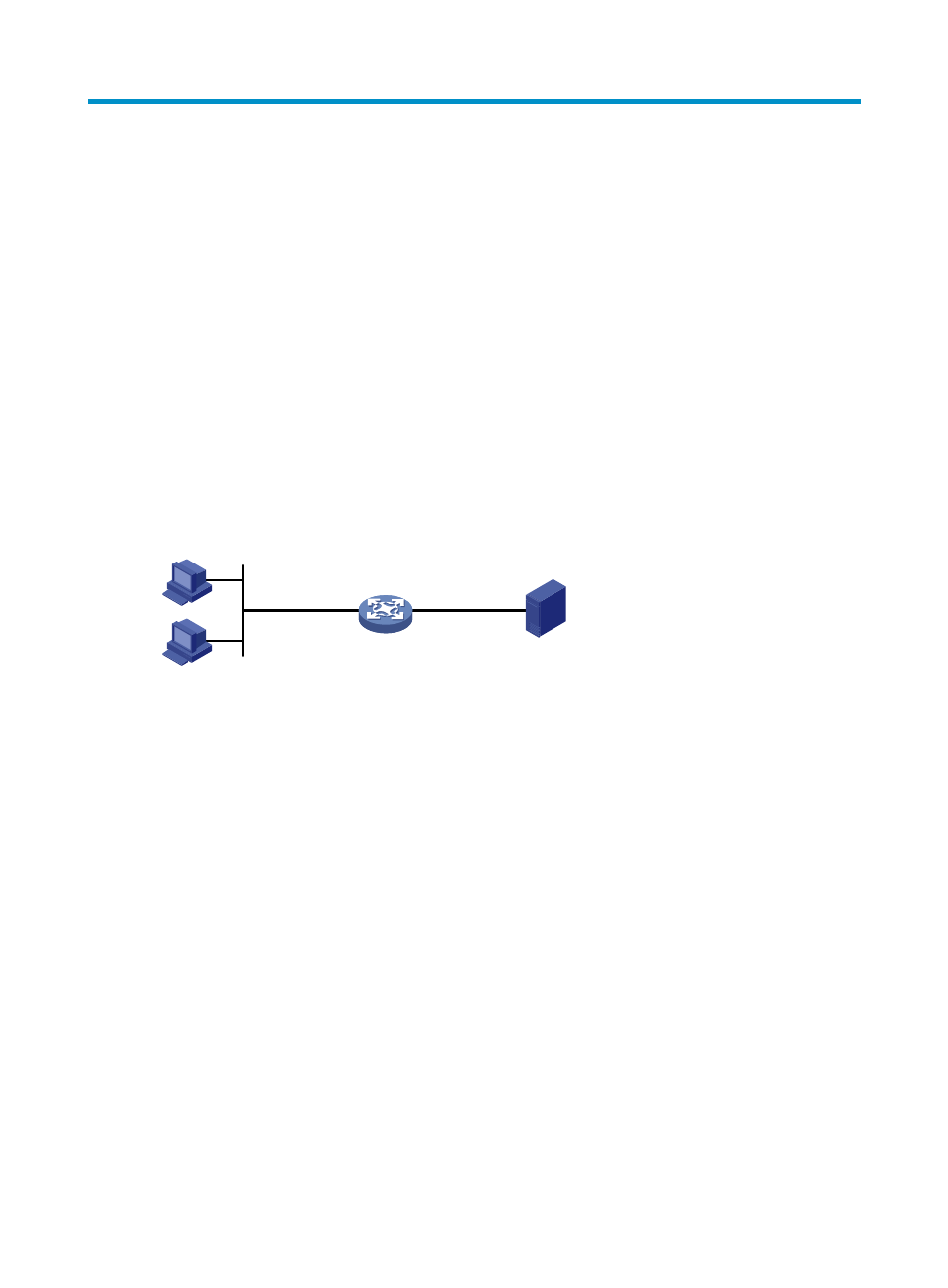
802.1X architecture
802.1X operates in the client/server model. It comprises three entities: client (the supplicant), the network
access device (the authenticator), and the authentication server, as shown in
.
Figure 410 802.1X architecture
•
The client is a user terminal seeking access to the LAN. It must have 802.1X software to authenticate
to the network access device.
•
The network access device authenticates the client to control access to the LAN. In a typical 802.1X
environment, the network access device uses an authentication server to perform authentication.
•
The authentication server is the entity that provides authentication services for the network access
device. It authenticates 802.1X clients by using the data sent from the network access device, and
returns the authentication results for the network access device to make access decisions. The
authentication server is typically a Remote Authentication Dial-in User Service (RADIUS) server. In a
small LAN, you can also use the network access device as the authentication server.
For more information about the 802.1X protocol, see H3C WX Series Access Controllers Security
Configuration Guide.
Access control methods
H3C implements port-based access control as defined in the 802.1X protocol, and extends the protocol
to support MAC-based access control.
•
With port-based access control, once an 802.1X user passes authentication on a port, any
subsequent user can access the network through the port without authentication. When the
authenticated user logs off, all other users are logged off.
Authentication server
Client
Device
