Association, Wlan data security – H3C Technologies H3C WX3000E Series Wireless Switches User Manual
Page 242
226
Figure 215 Open system authentication process
•
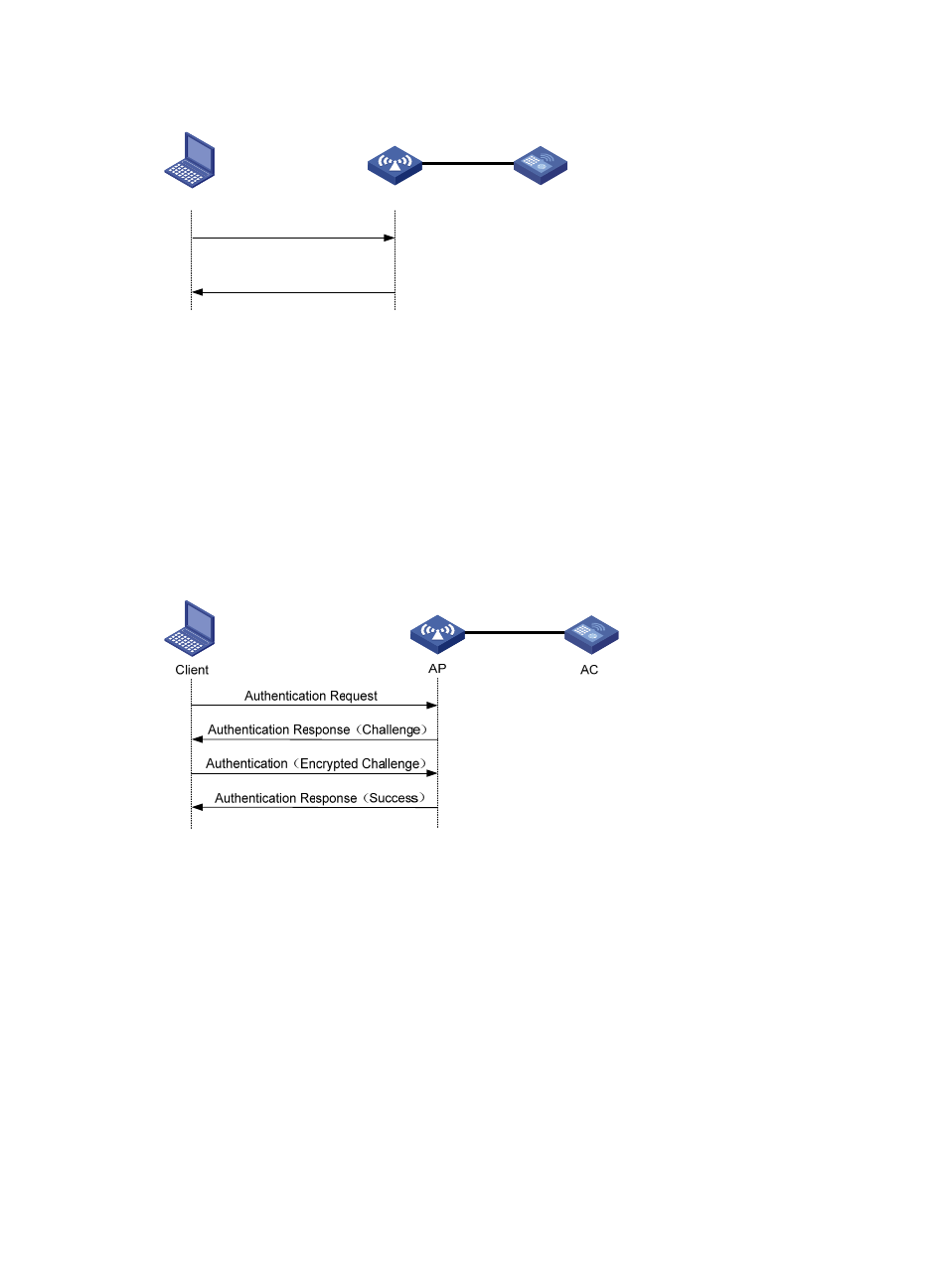
Shared key authentication
shows a shared key authentication process. The two parties have the same shared key
configured.
a.
The client sends an authentication request to the AP.
b.
The AP randomly generates a challenge and sends it to the client.
c.
The client uses the shared key to encrypt the challenge and sends it to the AP.
d.
The AP uses the shared key to encrypt the challenge and compares the result with that received
from the client. If they are identical, the client passes the authentication. If not, the
authentication fails.
Figure 216 Shared key authentication process
Association
A client that wants to access a wireless network via an AP must be associated with that AP. Once the
client chooses a compatible network with a specified SSID and authenticates to an AP, it sends an
association request frame to the AP. The AP sends an association response to the client and adds the
client's information in its database. At a time, a client can associate with only one AP. An association
process is always initiated by the client, but not by the AP.
WLAN data security
Compared with wired networks, WLAN networks are more susceptible to attacks because all WLAN
devices share the same medium and thus every device can receive data from any other sending device.
If no security service is provided, plain-text data is transmitted over the WLAN.
To secure data transmission, 802.11 protocols provide some encryption methods to ensure that devices
without the right key cannot read encrypted data.
AP
Client
Authentication request
Authentication response
AC
