Protocols and standards – H3C Technologies H3C SecPath F1000-E User Manual
Page 98
86
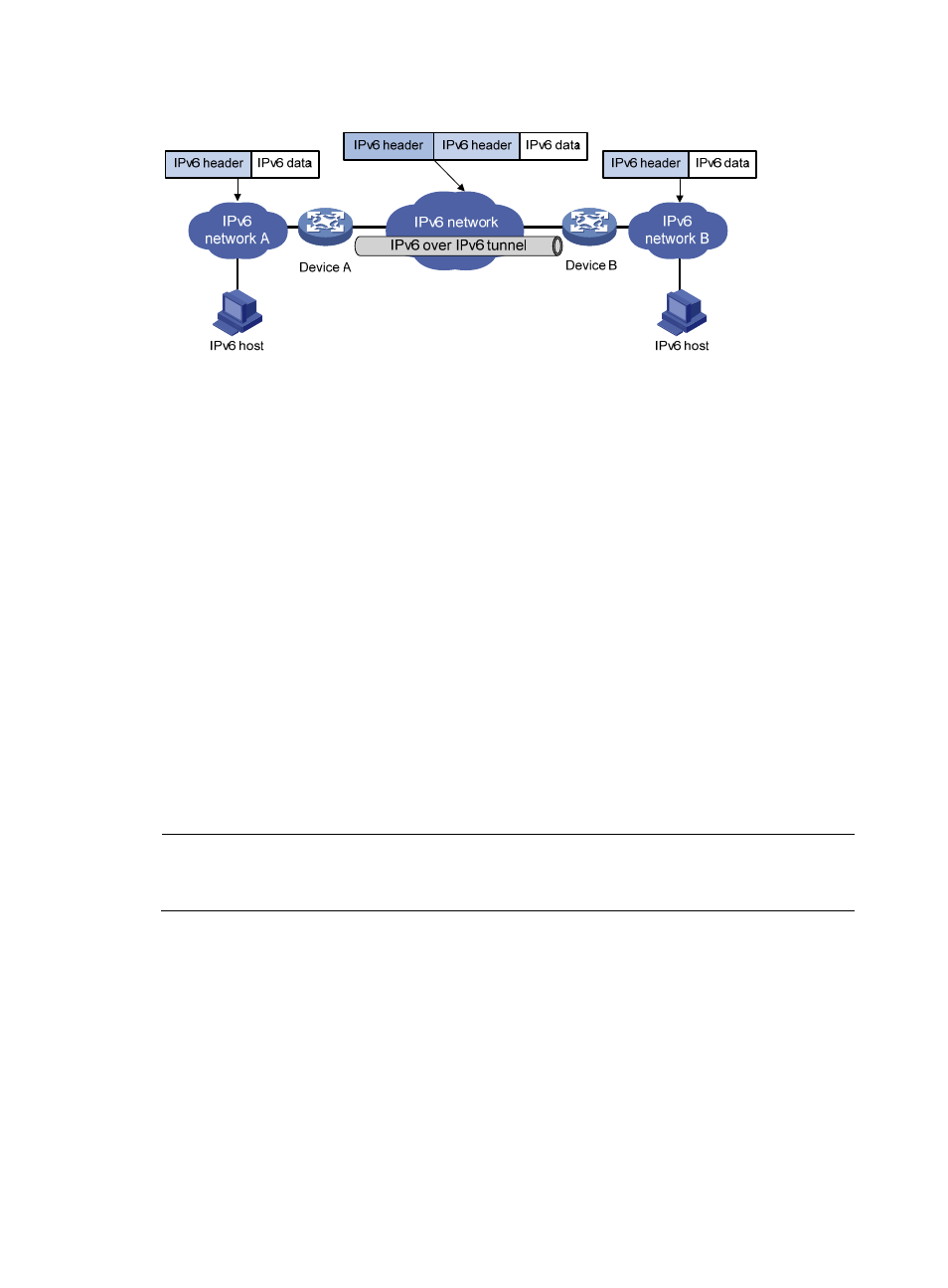
Figure 71 Principle of IPv6 over IPv6 tunneling
shows the encapsulation and de-encapsulation processes.
•
Encapsulation
a.
After receiving the IPv6 packet, the interface of Device A connecting private network A submits
it to the IPv6 module for processing. The IPv6 module then determines how to forward the
packet.
b.
If the packet is destined for Host B connected to Device B, the packet is sent to Router A's tunnel
interface that is connected to Device B.
c.
After receiving the packet, the tunnel interface adds an IPv6 header to it and submits it to the
IPv6 module for processing.
d.
The IPv6 module re-determines how to forward the packet according to the destination address
in the IPv6 header.
•
De-encapsulation
a.
The packet received from the IPv6 network interface is sent to the IPv6 module for processing.
b.
The IPv6 module checks the protocol type of the data portion encapsulated in the IPv6 packet.
If the encapsulation protocol is IPv6, the packet is sent to the tunnel processing module for
de-encapsulation.
c.
The de-encapsulated packet is sent to the IPv6 protocol module for the secondary routing
process.
NOTE:
GRE can realize the IPv6 over IPv6 tunnel function. For more information about related configurations, see
"Configuring GRE."
Protocols and standards
•
RFC 1853, IP in IP Tunneling
•
RFC 2473, Generic Packet Tunneling in IPv6 Specification
•
RFC 2893, Transition Mechanisms for IPv6 Hosts and Routers
•
RFC 3056, Connection of IPv6 Domains via IPv4 Clouds
•
RFC 4214, Intra-Site Automatic Tunnel Addressing Protocol (ISATAP)
- H3C SecPath F5000-A5 Firewall H3C SecPath F1000-A-EI H3C SecPath F1000-E-SI H3C SecPath F1000-S-AI H3C SecPath F5000-S Firewall H3C SecPath F5000-C Firewall H3C SecPath F100-C-SI H3C SecPath F1000-C-SI H3C SecPath F100-A-SI H3C SecBlade FW Cards H3C SecBlade FW Enhanced Cards H3C SecPath U200-A U200-M U200-S H3C SecPath U200-CA U200-CM U200-CS
