H3C Technologies H3C SecPath F1000-E User Manual
Page 138
126
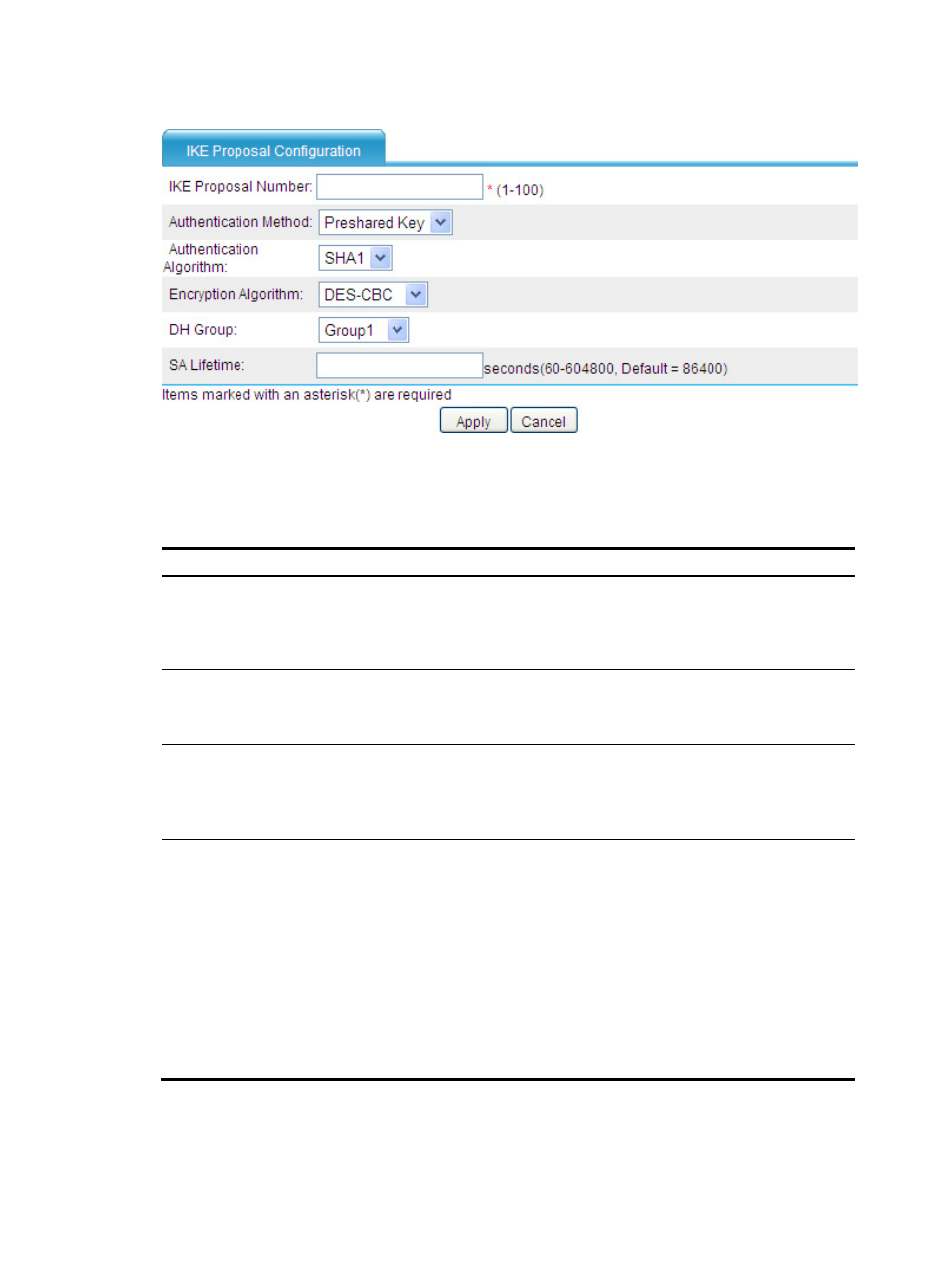
Figure 84 Adding an IKE proposal
3.
Configure an IKE proposal as described in
4.
Click Apply.
Table 6 Configuration items
Item
Description
IKE Proposal Number
Enter the IKE proposal number.
The number also stands for the priority of the IKE proposal, with a smaller value
meaning a higher priority. During IKE negotiation, the system matches IKE
proposals in order of proposal number, starting from the smallest one.
Authentication Method
Select the authentication method to be used by the IKE proposal. Options include:
•
Preshared Key—Uses the pre-shared key method.
•
RSA Signature—Uses the RSA digital signature method.
Authentication Algorithm
Select the authentication algorithm to be used by the IKE proposal. Options
include:
•
SHA1—Uses HMAC-SHA1.
•
MD5—Uses HMAC-MD5. This algorithm is not available for the FIPS mode.
Encryption Algorithm
Select the encryption algorithm to be used by the IKE proposal. Options include:
•
DES-CBC—Uses the DES algorithm in CBC mode and 56-bit keys for
encryption. This algorithm is not available for the FIPS mode.
•
3DES-CBC—Uses the 3DES algorithm in CBC mode and 168-bit keys for
encryption. This algorithm is not available for the FIPS mode.
•
AES-128—Uses the AES algorithm in CBC mode and 128-bit keys for
encryption. It is the default encryption algorithm in FIPS mode.
•
AES-192—Uses the AES algorithm in CBC mode and 192-bit keys for
encryption.
•
AES-256—Uses the AES algorithm in CBC mode and 256-bit keys for
encryption.
- H3C SecPath F5000-A5 Firewall H3C SecPath F1000-A-EI H3C SecPath F1000-E-SI H3C SecPath F1000-S-AI H3C SecPath F5000-S Firewall H3C SecPath F5000-C Firewall H3C SecPath F100-C-SI H3C SecPath F1000-C-SI H3C SecPath F100-A-SI H3C SecBlade FW Cards H3C SecBlade FW Enhanced Cards H3C SecPath U200-A U200-M U200-S H3C SecPath U200-CA U200-CM U200-CS
