Ipsec for ipv6 routing protocols, Ipsec rri – H3C Technologies H3C SecPath F1000-E User Manual
Page 167
155
3.
The IPsec tunnel interface encapsulates the packet, and then sends the packet to the forwarding
module.
4.
The forwarding module looks up the routing table again and forwards the IPsec-encrypted packet
out of the physical outbound interface that is associated with the tunnel interface.
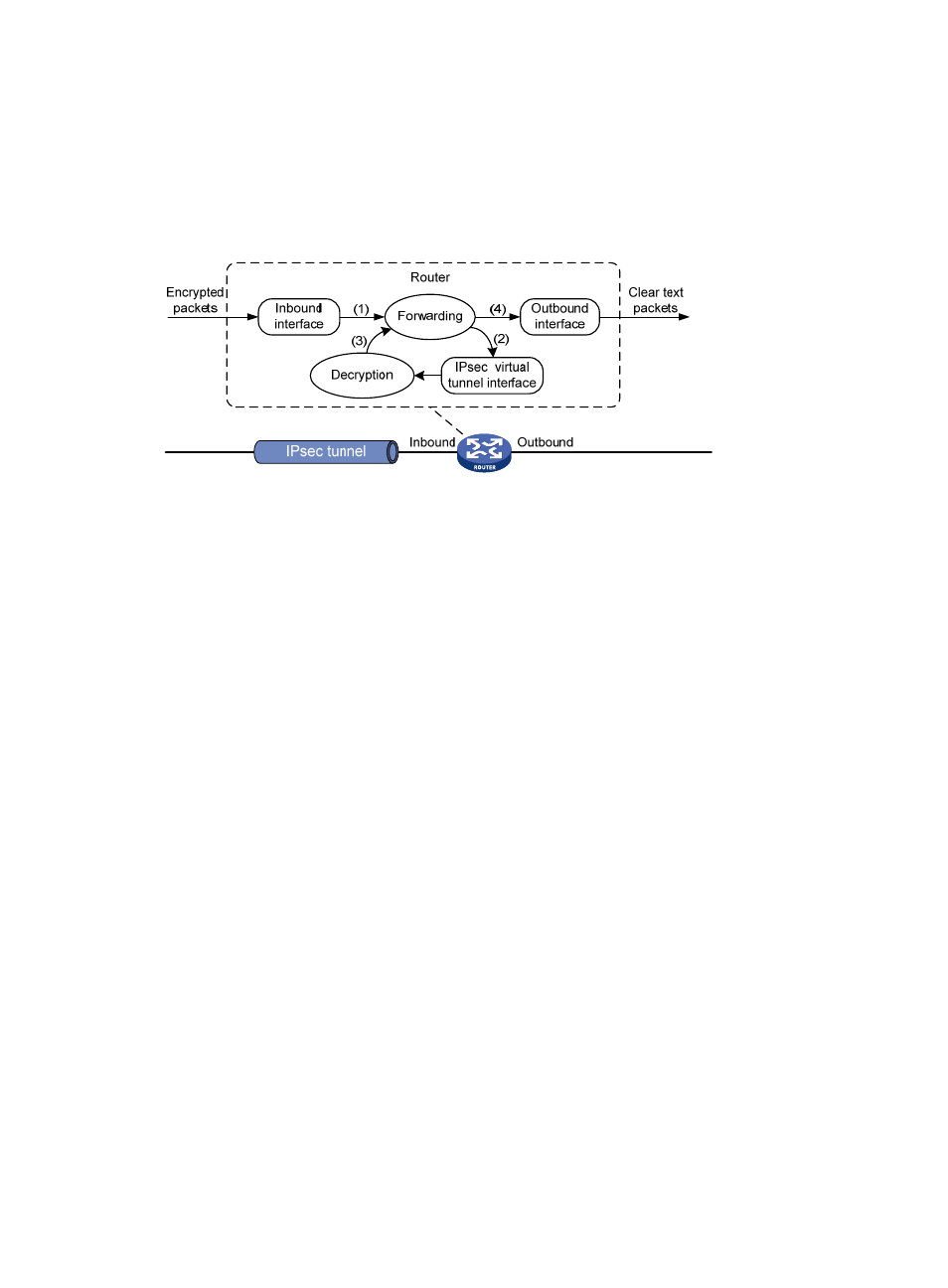
shows how an IPsec packet is de-encapsulated on an IPsec tunnel interface.
Figure 97 De-encapsulation process of an IPsec packet
5.
The router forwards an IPsec packet received on the inbound interface to the forwarding module.
6.
Identifying that the destination address of the packet is the tunnel interface and the protocol is AH
or ESP, the forwarding module forwards the packet to the IPsec tunnel interface for
de-encapsulation.
7.
The IPsec tunnel interface de-encapsulates the packet, and then delivers the resulting clear text
packet back to the forwarding module.
8.
The forwarding module looks up the routing table, and then forwards the clear text packet out of
the physical outbound interface associated with the tunnel interface.
IPsec for IPv6 routing protocols
You can use IPsec to protect routing information and defend attacks for these IPv6 routing protocols:
OSPFv3, IPv6 BGP, and RIPng. IPsec enables these IPv6 routing protocols to encapsulate outbound
protocol packets and de-encapsulate inbound protocol packets with the AH or ESP protocol. If an
inbound protocol packet is not IPsec protected, or fails to be de-encapsulated, for example, due to
decryption or authentication failure, the routing protocol discards that packet.
You must manually configure SA parameters in an IPsec policy for IPv6 routing protocols. The IKE key
exchange mechanism is applicable only to one-to-one communications. IPsec cannot implement
automatic key exchange for one-to-many communications on a broadcast network, where routers must
use the same SA parameters (SPI and key) to process packets for a routing protocol.
IPsec RRI
IPsec Reverse Route Inject (RRI) enables an IPsec tunnel gateway to automatically add static routes
destined for protected private networks or peer IPsec tunnel gateways to a routing table. In a VPN
network, IPsec RRI can add static routes to VPN instances’ routing tables.
IPsec RRI is applicable to gateways for example, a headquarters gateway that must provide many IPsec
tunnels. It frees you from the tedious work of manually configuring and maintaining static routes for IPsec
tunnels. For example, if you enable RRI on Device A in
, Device A can automatically create a
- H3C SecPath F5000-A5 Firewall H3C SecPath F1000-A-EI H3C SecPath F1000-E-SI H3C SecPath F1000-S-AI H3C SecPath F5000-S Firewall H3C SecPath F5000-C Firewall H3C SecPath F100-C-SI H3C SecPath F1000-C-SI H3C SecPath F100-A-SI H3C SecBlade FW Cards H3C SecBlade FW Enhanced Cards H3C SecPath U200-A U200-M U200-S H3C SecPath U200-CA U200-CM U200-CS
