Network requirements, Configuring device a – H3C Technologies H3C SecPath F1000-E User Manual
Page 310
298
IKE negotiation with RSA digital signature configuration
example
NOTE:
In this configuration example, either Device A or Device B is the SecPath firewall.
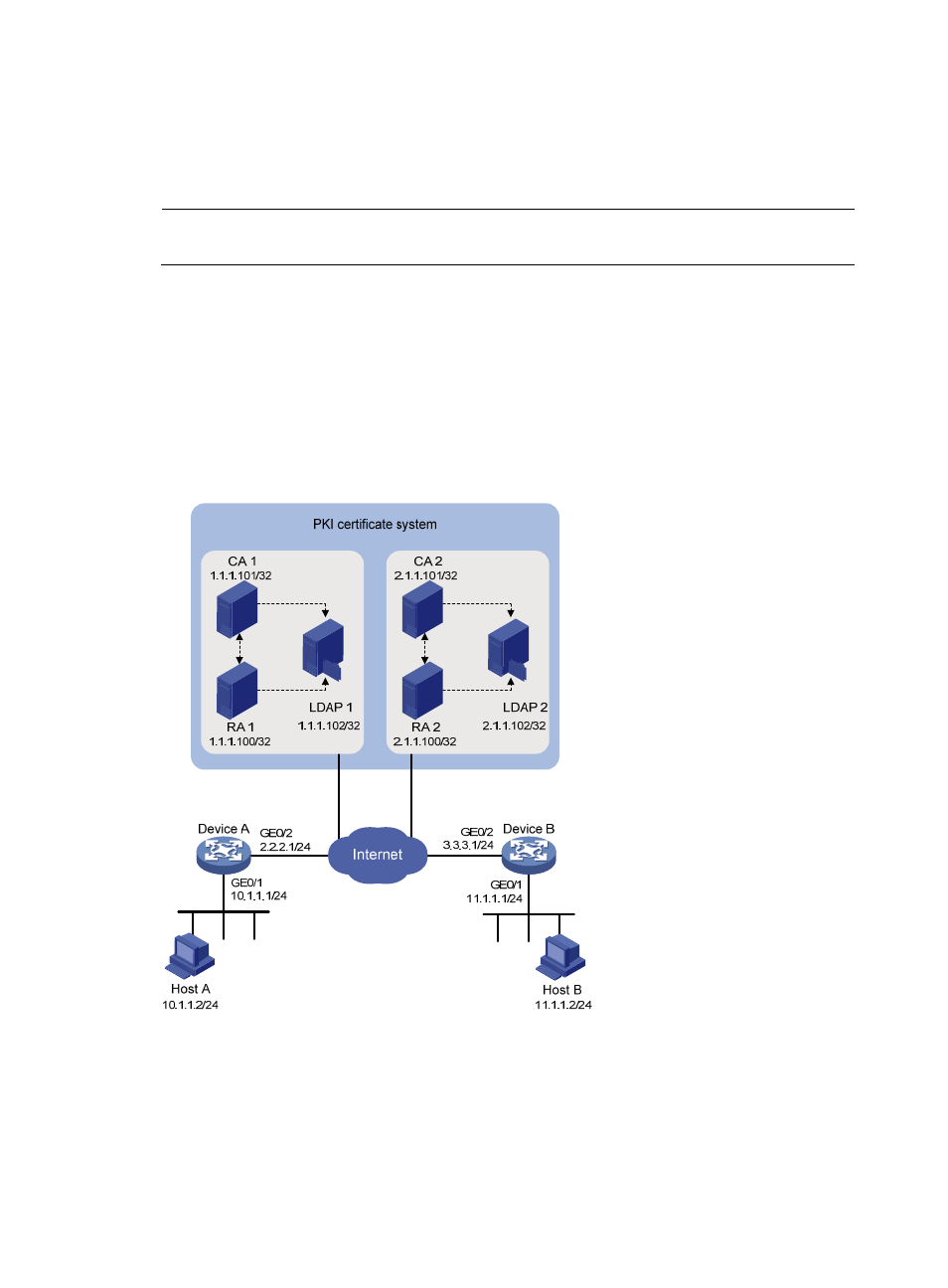
Network requirements
As shown in
,
•
An IPsec tunnel is set up between Device A and Device B to secure the traffic between Host A on
subnet 10.1.1.0/24 and Host B on subnet 11.1.1.0/24.
•
Device A and Device B use IKE for IPsec tunnel negotiation and RSA digital signature of a PKI
certificate system for identity authentication.
•
Device A and Device B use different CAs. They may also use the same CA as required.
Figure 198 Network diagram
Configuring Device A
1.
Create a PKI entity:
a.
From the navigation tree, select VPN > Certificate Management > Entity.
b.
Click Add.
- H3C SecPath F5000-A5 Firewall H3C SecPath F1000-A-EI H3C SecPath F1000-E-SI H3C SecPath F1000-S-AI H3C SecPath F5000-S Firewall H3C SecPath F5000-C Firewall H3C SecPath F100-C-SI H3C SecPath F1000-C-SI H3C SecPath F100-A-SI H3C SecBlade FW Cards H3C SecBlade FW Enhanced Cards H3C SecPath U200-A U200-M U200-S H3C SecPath U200-CA U200-CM U200-CS
