Gre over ipv6 tunnel configuration example, Network requirements, Configuration procedure – H3C Technologies H3C SecPath F1000-E User Manual
Page 28
16
Step Command
Remarks
9.
Enable the GRE packet
checksum function.
gre checksum
Optional.
Disabled by default.
10.
Configure the key for the GRE
tunnel interface.
gre key key-number
Optional.
By default, no key is configured for
a GRE tunnel interface.
The two ends of a tunnel must have
the same key or have no key at the
same time.
11.
Return to system view.
quit
N/A
12.
Configure the firewall to
discard the IPv4-compatible
IPv6 packets.
tunnel discard
ipv4-compatible-packet
Optional.
By default, the firewall does not
discard the IPv4-compatible IPv6
packets.
13.
Configure a route for packet
forwarding through the
tunnel.
See Network Management
Configuration Guide
Each end of the tunnel must have a
route (static or dynamic) through
the tunnel to the other end.
NOTE:
For more information about tunnel interfaces and related configurations, see "Configuring tunneling."
GRE over IPv6 tunnel configuration example
NOTE:
In this configuration example, either Router A or Router B is the SecPath firewall.
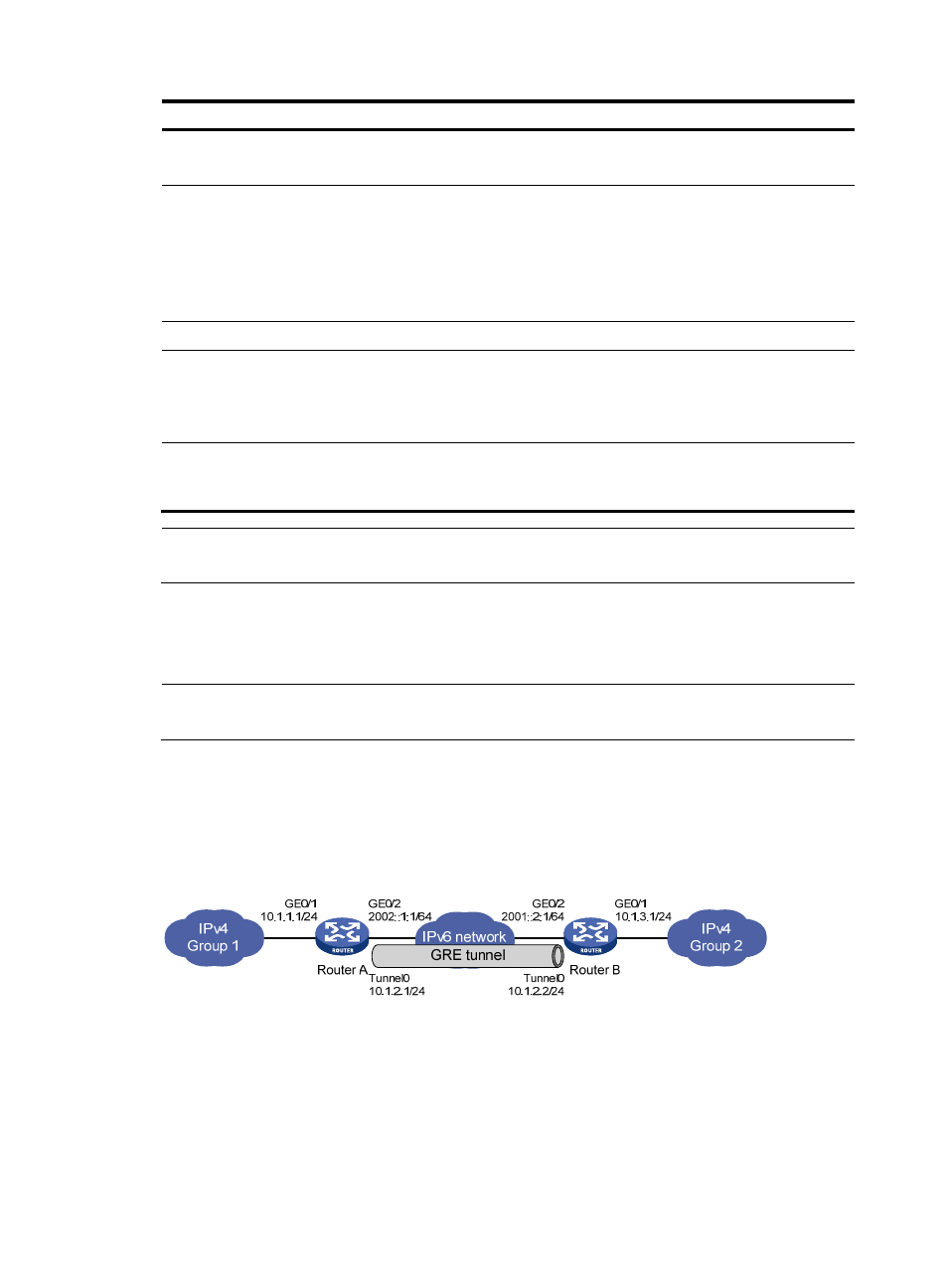
Network requirements
Two IPv4 subnets Group 1 and Group 2 are connected to an IPv6 network. Create a GRE over IPv6
tunnel between Router A and Router B, so that the two IPv4 subnets can communicate with each other
through the GRE tunnel over the IPv6 network.
Figure 15 Network diagram for a GRE over IPv6 tunnel
Configuration procedure
Before the configuration, make sure Router A and Router B can reach each other.
1.
Configure Router A:
# Enable IPv6.
[RouterA] ipv6
- H3C SecPath F5000-A5 Firewall H3C SecPath F1000-A-EI H3C SecPath F1000-E-SI H3C SecPath F1000-S-AI H3C SecPath F5000-S Firewall H3C SecPath F5000-C Firewall H3C SecPath F100-C-SI H3C SecPath F1000-C-SI H3C SecPath F100-A-SI H3C SecBlade FW Cards H3C SecBlade FW Enhanced Cards H3C SecPath U200-A U200-M U200-S H3C SecPath U200-CA U200-CM U200-CS
