Ca policy, Architecture of pki – H3C Technologies H3C SecPath F1000-E User Manual
Page 288
276
been revoked. The CRLs contain the serial numbers of all revoked certificates and provide an effective
way for checking the validity of certificates.
A CA may publish multiple CRLs when the number of revoked certificates is so large that publishing them
in a single CRL may degrade network performance. In this case, CRL distribution points indicate the URLs
of these CRLs.
CA policy
A CA policy is a set of criteria that a CA follows in processing certificate requests, issuing and revoking
certificates, and publishing CRLs. Usually, a CA advertises its policy in the form of certification practice
statement (CPS). A CA policy can be acquired through out-of-band means such as phone, disk, and
email. As different CAs may use different methods to check the binding of a public key with an entity,
make sure that you understand the CA policy before selecting a trusted CA for certificate request.
Architecture of PKI
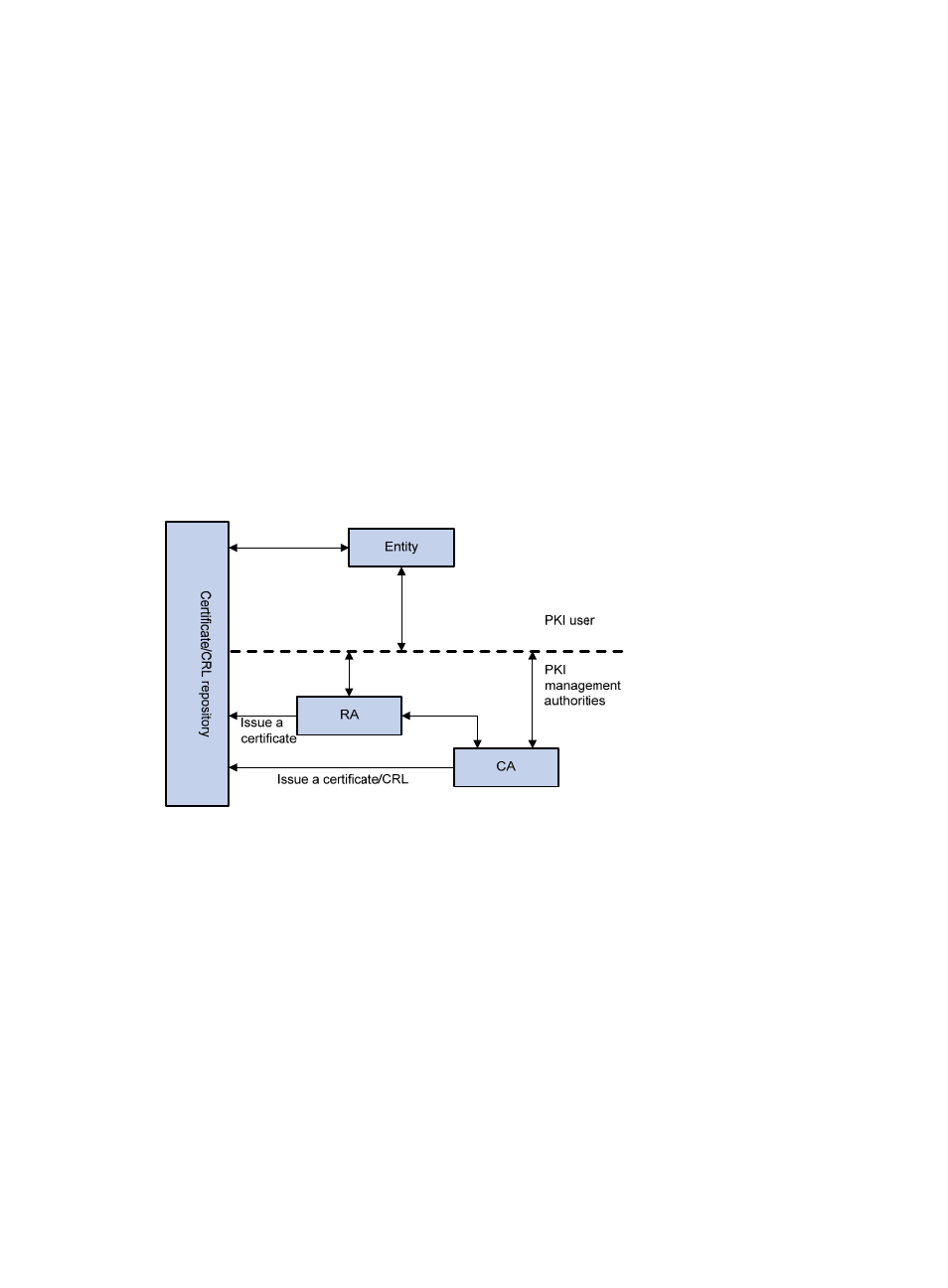
A PKI system consists of entities, a CA, a registration authority (RA) and a PKI repository, as shown
in
.
Figure 170 PKI architecture
Entity—An entity is an end user of PKI products or services, such as a person, an organization, a device
like a router or a switch, or a process running on a computer.
CA—A certificate authority (CA) is a trusted authority responsible for issuing and managing digital
certificates. A CA issues certificates, specifies the validity periods of certificates, and revokes certificates
as needed by publishing CRLs.
RA—A registration authority (RA) is an extended part of a CA or an independent authority. An RA can
implement functions including identity authentication, CRL management, key pair generation and key
pair backup. It receives registration requests, examines the qualifications of users, and decides whether
the CA can assign digital certificates to the users. Sometimes, a CA assumes the registration
management responsibility and no independent RA exists. The PKI standard recommends that an
independent RA be used for registration management to achieve higher security of application systems.
PKI repository—A PKI repository can be a Lightweight Directory Access Protocol (LDAP) server or a
common database. It stores and manages information like certificate requests, certificates, keys, CRLs
and logs and it provides a simple query function.
- H3C SecPath F5000-A5 Firewall H3C SecPath F1000-A-EI H3C SecPath F1000-E-SI H3C SecPath F1000-S-AI H3C SecPath F5000-S Firewall H3C SecPath F5000-C Firewall H3C SecPath F100-C-SI H3C SecPath F1000-C-SI H3C SecPath F100-A-SI H3C SecBlade FW Cards H3C SecBlade FW Enhanced Cards H3C SecPath U200-A U200-M U200-S H3C SecPath U200-CA U200-CM U200-CS
