Mirror image acls, Figure 105 – H3C Technologies H3C SecPath F1000-E User Manual
Page 173
161
Figure 105 IPsec policy configuration on Device B
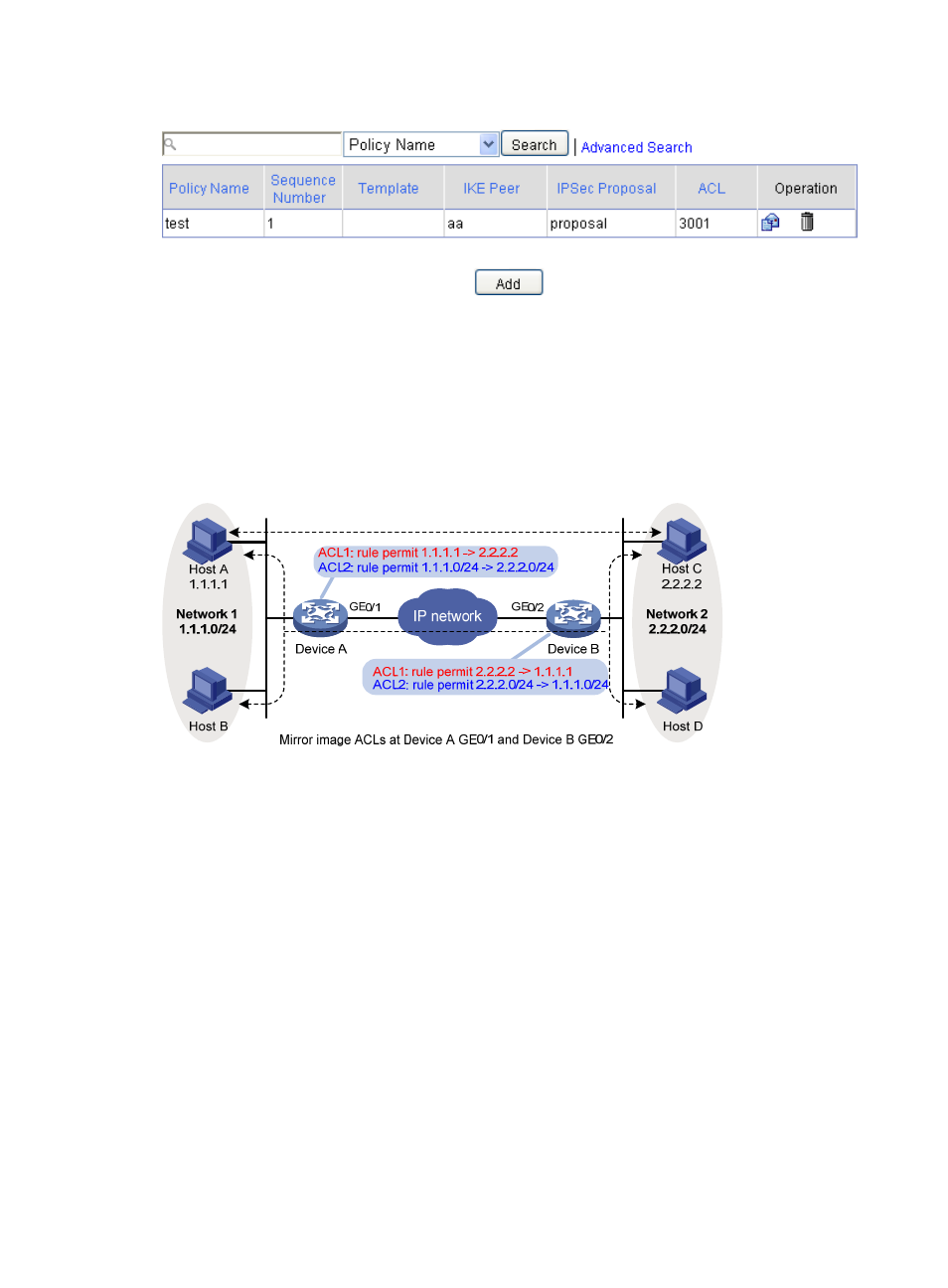
Mirror image ACLs
To make sure that SAs can be set up and the traffic protected by IPsec locally can be processed correctly
at the remote peer, on the remote peer, create a mirror image ACL rule for each ACL rule created at the
local peer. As shown in
, ACL rules on Device B are mirror images of the rules on Device A.
This makes sure that SAs can be created successfully for the traffic between Host A and Host C and the
traffic between Network 1 and Network 2.
Figure 106 Mirror image ACLs
If the ACL rules on the peers do not form mirror images of each other, SAs can be set up only when both
of the following requirements are met:
•
The range specified by an ACL rule on one peer is covered by its counterpart ACL rule on the other
peer. As shown in
, the range specified by the ACL rule configured on Device A is
covered by its counterpart on Device B.
•
The peer with the narrower rule initiates SA negotiation. If a wider ACL rule is used by the SA
initiator, the negotiation request may be rejected because the matching traffic is beyond the scope
of the responder. As shown in
, the SA negotiation initiated by Host A to Host C is
accepted but the SA negotiation from Host C to Host B or from Host D to Host A is rejected.
- H3C SecPath F5000-A5 Firewall H3C SecPath F1000-A-EI H3C SecPath F1000-E-SI H3C SecPath F1000-S-AI H3C SecPath F5000-S Firewall H3C SecPath F5000-C Firewall H3C SecPath F100-C-SI H3C SecPath F1000-C-SI H3C SecPath F100-A-SI H3C SecBlade FW Cards H3C SecBlade FW Enhanced Cards H3C SecPath U200-A U200-M U200-S H3C SecPath U200-CA U200-CM U200-CS
